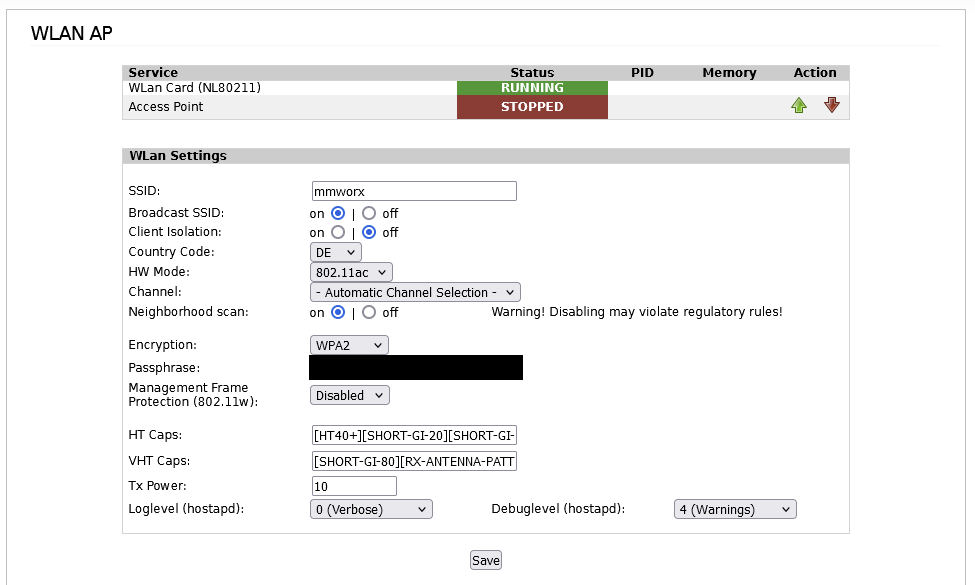
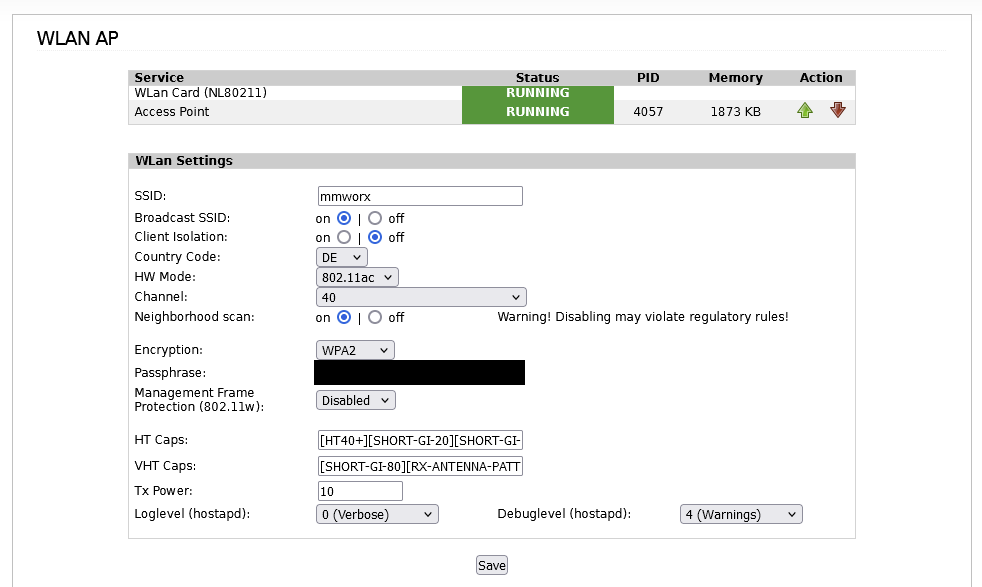
Just restarted IPFire and got an non-working AP. That’s the Log from today:
|01:11:05|hostapd:|blue0: STA 90:e8:68:ee:dd:91 WPA: event 2 notification|
|---|---|---|
|01:11:05|hostapd:|blue0: STA 90:e8:68:ee:dd:91 IEEE 802.1X: unauthorizing port|
|01:11:05|hostapd:|blue0: STA 90:e8:68:ee:dd:91 IEEE 802.11: disassociated|
|01:11:05|hostapd:|blue0: STA 90:e8:68:ee:dd:91 MLME: MLME-DISASSOCIATE.indication(90:e8:68:ee:dd: 91, 3)|
|01:11:05|hostapd:|blue0: STA 90:e8:68:ee:dd:91 MLME: MLME-DELETEKEYS.request(90:e8:68:ee:dd:91)|
|01:11:06|hostapd:|blue0: STA 90:e8:68:ee:dd:91 IEEE 802.11: deauthenticated due to inactivity (ti mer DEAUTH/REMOVE)|
|01:11:06|hostapd:|blue0: STA 90:e8:68:ee:dd:91 MLME: MLME-DEAUTHENTICATE.indication(90:e8:68:ee:d d:91, 2)|
|01:11:06|hostapd:|blue0: STA 90:e8:68:ee:dd:91 MLME: MLME-DELETEKEYS.request(90:e8:68:ee:dd:91)|
|01:14:21|hostapd:|blue0: STA 90:e8:68:ee:dd:91 IEEE 802.11: authentication OK (open system)|
|01:14:21|hostapd:|blue0: STA 90:e8:68:ee:dd:91 MLME: MLME-AUTHENTICATE.indication(90:e8:68:ee:dd: 91, OPEN_SYSTEM)|
|01:14:21|hostapd:|blue0: STA 90:e8:68:ee:dd:91 MLME: MLME-DELETEKEYS.request(90:e8:68:ee:dd:91)|
|01:14:21|hostapd:|blue0: STA 90:e8:68:ee:dd:91 IEEE 802.11: authenticated|
|01:14:21|hostapd:|blue0: STA 90:e8:68:ee:dd:91 IEEE 802.11: association OK (aid 1)|
|01:14:21|hostapd:|blue0: STA 90:e8:68:ee:dd:91 IEEE 802.11: associated (aid 1)|
|01:14:21|hostapd:|blue0: STA 90:e8:68:ee:dd:91 MLME: MLME-ASSOCIATE.indication(90:e8:68:ee:dd:91)|
|01:14:21|hostapd:|blue0: STA 90:e8:68:ee:dd:91 MLME: MLME-DELETEKEYS.request(90:e8:68:ee:dd:91)|
|01:14:21|hostapd:|blue0: STA 90:e8:68:ee:dd:91 WPA: event 1 notification|
|01:14:21|hostapd:|blue0: STA 90:e8:68:ee:dd:91 WPA: start authentication|
|01:14:21|hostapd:|blue0: STA 90:e8:68:ee:dd:91 IEEE 802.1X: unauthorizing port|
|01:14:21|hostapd:|blue0: STA 90:e8:68:ee:dd:91 WPA: sending 1/4 msg of 4-Way Handshake|
|01:14:21|hostapd:|blue0: STA 90:e8:68:ee:dd:91 WPA: received EAPOL-Key frame (2/4 Pairwise)|
|01:14:21|hostapd:|blue0: STA 90:e8:68:ee:dd:91 WPA: sending 3/4 msg of 4-Way Handshake|
|01:14:21|hostapd:|blue0: STA 90:e8:68:ee:dd:91 WPA: received EAPOL-Key frame (4/4 Pairwise)|
|01:14:21|hostapd:|blue0: STA 90:e8:68:ee:dd:91 IEEE 802.1X: authorizing port|
|01:14:21|hostapd:|blue0: STA 90:e8:68:ee:dd:91 WPA: pairwise key handshake completed (RSN)|
|01:54:36|hostapd:|blue0: STA 90:e8:68:ee:dd:91 IEEE 802.11: disassociated due to inactivity|
|01:54:36|hostapd:|blue0: STA 90:e8:68:ee:dd:91 MLME: MLME-DISASSOCIATE.indication(90:e8:68:ee:dd: 91, 4)|
|01:54:36|hostapd:|blue0: STA 90:e8:68:ee:dd:91 MLME: MLME-DELETEKEYS.request(90:e8:68:ee:dd:91)|
|01:54:37|hostapd:|blue0: STA 90:e8:68:ee:dd:91 IEEE 802.11: deauthenticated due to inactivity (ti mer DEAUTH/REMOVE)|
|01:54:37|hostapd:|blue0: STA 90:e8:68:ee:dd:91 MLME: MLME-DEAUTHENTICATE.indication(90:e8:68:ee:d d:91, 2)|
|01:54:37|hostapd:|blue0: STA 90:e8:68:ee:dd:91 MLME: MLME-DELETEKEYS.request(90:e8:68:ee:dd:91)|
|11:17:41|hostapd:|blue0: STA 90:e8:68:ee:dd:91 IEEE 802.11: authentication OK (open system)|
|11:17:41|hostapd:|blue0: STA 90:e8:68:ee:dd:91 MLME: MLME-AUTHENTICATE.indication(90:e8:68:ee:dd: 91, OPEN_SYSTEM)|
|11:17:41|hostapd:|blue0: STA 90:e8:68:ee:dd:91 MLME: MLME-DELETEKEYS.request(90:e8:68:ee:dd:91)|
|11:17:41|hostapd:|blue0: STA 90:e8:68:ee:dd:91 IEEE 802.11: authenticated|
|11:17:41|hostapd:|blue0: STA 90:e8:68:ee:dd:91 IEEE 802.11: association OK (aid 1)|
|11:17:41|hostapd:|blue0: STA 90:e8:68:ee:dd:91 IEEE 802.11: associated (aid 1)|
|11:17:41|hostapd:|blue0: STA 90:e8:68:ee:dd:91 MLME: MLME-ASSOCIATE.indication(90:e8:68:ee:dd:91)|
|11:17:41|hostapd:|blue0: STA 90:e8:68:ee:dd:91 MLME: MLME-DELETEKEYS.request(90:e8:68:ee:dd:91)|
|11:17:41|hostapd:|blue0: STA 90:e8:68:ee:dd:91 WPA: event 1 notification|
|11:17:41|hostapd:|blue0: STA 90:e8:68:ee:dd:91 WPA: start authentication|
|11:17:41|hostapd:|blue0: STA 90:e8:68:ee:dd:91 IEEE 802.1X: unauthorizing port|
|11:17:41|hostapd:|blue0: STA 90:e8:68:ee:dd:91 WPA: sending 1/4 msg of 4-Way Handshake|
|11:17:41|hostapd:|blue0: STA 90:e8:68:ee:dd:91 WPA: received EAPOL-Key frame (2/4 Pairwise)|
|11:17:41|hostapd:|blue0: STA 90:e8:68:ee:dd:91 WPA: sending 3/4 msg of 4-Way Handshake|
|11:17:41|hostapd:|blue0: STA 90:e8:68:ee:dd:91 WPA: received EAPOL-Key frame (4/4 Pairwise)|
|11:17:41|hostapd:|blue0: STA 90:e8:68:ee:dd:91 IEEE 802.1X: authorizing port|
|11:17:41|hostapd:|blue0: STA 90:e8:68:ee:dd:91 WPA: pairwise key handshake completed (RSN)|
|12:48:20|hostapd:|blue0: STA 90:e8:68:ee:dd:91 IEEE 802.11: disconnected due to excessive missing ACKs|
|12:48:20|hostapd:|blue0: STA 90:e8:68:ee:dd:91 MLME: MLME-DISASSOCIATE.indication(90:e8:68:ee:dd: 91, 34)|
|12:48:20|hostapd:|blue0: STA 90:e8:68:ee:dd:91 MLME: MLME-DELETEKEYS.request(90:e8:68:ee:dd:91)|
|12:48:29|hostapd:|blue0: STA 90:e8:68:ee:dd:91 MLME: MLME-DEAUTHENTICATE.indication(90:e8:68:ee:d d:91, 1)|
|12:48:29|kernel: ath10k_pci 0000:03:00.0:|DFS region 0x0 not supported, will trigger radar for every pulse|
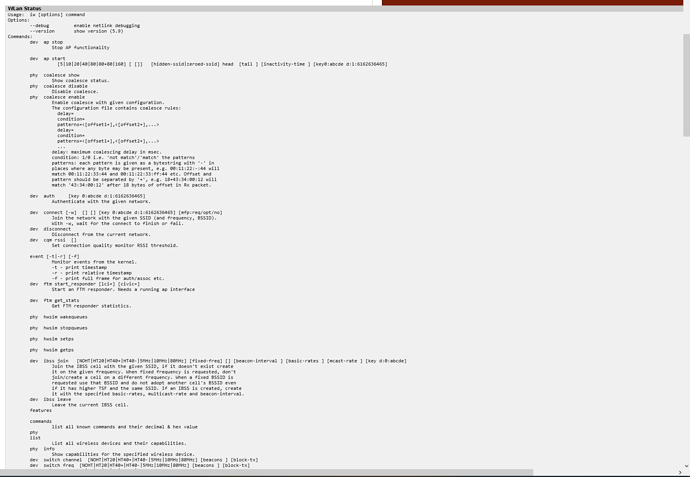
Config unchanged: Also I’m getting a strange wlan status displayed: