Hello Community,
I just bought the PRG310 Hardware-RNG from https://www.ibbergmann.org to improve my entropy. To save external USB ports I got the PRG310-51, which can be directly connected to the internal USB-port on the motherboard, but there are also models with regular external USB connectors. To order simply send an email over the webpage. Shipment was very fast. 
Following some posts in the old ipfire forum (https://forum.ipfire.org/viewtopic.php?f=17&t=12487) I just wanted to share how I installed the device:
0. Plug in PRG310 
1. Create start script (e.g. under /root)
vi /root/startp310.sh
copy following content inside the script:
#!/bin/bash
#Log function
logme () {
logger -t ipfire p310:$1
echo "$1"
}
logme "HWRNG detected"
logme "setup stty"
/bin/stty raw -echo -ixoff -F /dev/hwrngtty speed 921600 > /dev/null
logme "execute start command"
/bin/echo -n "4b" > /dev/hwrngtty
remark: in the last line 4 activates the PTG.3 AES128 encryption and with b the continuous random number generation is started
make the script executable with:
chmod +x /root/startp310.sh
2. Get serial from PRG310:
Execute the following command:
udevadm info -a -p $(udevadm info -q path -n ttyUSB0) | egrep -i "ATTRS{serial}|ATTRS{idVendor}|ATTRS{idProduct}" -m 3
Result should be something like this:
ATTRS{idProduct}=="6001"
ATTRS{idVendor}=="0403"
ATTRS{serial}=="XXXXXXXX"
 If idProduct and idVendor are NOT 6001 and 0403 try the above command with different ttyUSB (e.g. ttyUSB1).
If idProduct and idVendor are NOT 6001 and 0403 try the above command with different ttyUSB (e.g. ttyUSB1).
To find out which devices are connected to the system you can execute:
ls /dev/ttyUSB*
3. Create config file for udev:
vi /etc/udev/rules.d/99_ftdi_hwrng.rules
Copy the following content into the file AND replace XXXXXXXX with your serial from 2. :
SUBSYSTEM=="tty", ATTRS{idVendor}=="0403", ATTRS{idProduct}=="6001", ATTRS{serial}=="XXXXXXXX", SYMLINK+="hwrngtty", RUN+="/root/startp310.sh"
4. Restart udev and rngd
Execute the following 2 commands:
/etc/init.d/udev restart
/etc/init.d/rngd restart
5. Check functionality:
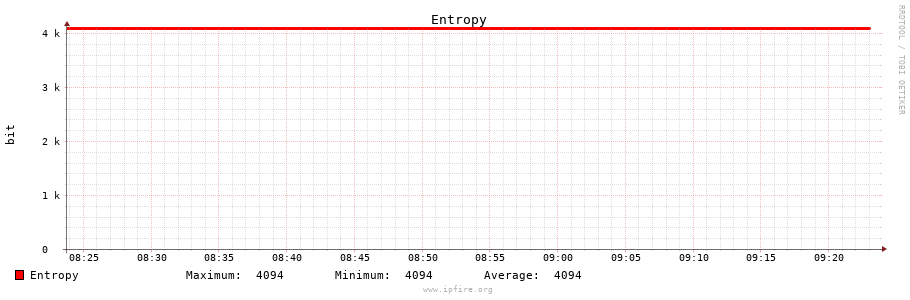
Go to the web interface of ipfire and go to “Status->Entropy”. The Entropy graph should rise quickly above 3k. “Random Number Generator Daemon” at the bottom should be green and “RUNNING”. If everything works reboot and check if everything still works as expected.
6. Enjoy


 ):
):