First of all, so far the Let’s encrypt certification renewal challenge worked great until today.
Since the renewal done with a cron job on IPFire, I did not notice so far that there is an issue up to now. Today, the various hosted sites behind IPFire are not reachable anymore because of certificate expiration.
Today my SSL certificates finally expired and the renewal process fails with error, domain names and public IP anonymized:
Processing XXX.mydomain.de
+ Checking expire date of existing cert...
+ Valid till May 30 04:00:47 2024 GMT (Less than 30 days). Renewing!
+ Signing domains...
+ Generating private key...
+ Generating signing request...
+ Requesting new certificate order from CA...
+ Received 1 authorizations URLs from the CA
+ Handling authorization for XXX.mydomain.de
+ 1 pending challenge(s)
+ Deploying challenge tokens...
+ Responding to challenge for XXX.mydomain.de authorization...
XXX.mydomain.de failed! + Cleaning challenge tokens...
+ Challenge validation has failed :(
ERROR: Challenge is invalid! (returned: invalid) (result: ["type"] "http-01"
["status"] "invalid"
["error","type"] "urn:ietf:params:acme:error:connection"
["error","detail"] "During secondary validation: 178.27.xxx.xx: Fetching http://XXX.mydomain.de/.well-known/acme-challenge/9NUgxoqAKvHt_H77xE6PCnFdCSuooZ2rnrIyIokM1-4: Timeout during connect (likely firewall problem)"
["error","status"] 400
["error"] {"type":"urn:ietf:params:acme:error:connection","detail":"During secondary validation: 178.27.xxx.xx: Fetching http://XXX.mydomain.de/.well-known/acme-challenge/9NUgxoqAKvHt_H77xE6PCnFdCSuooZ2rnrIyIokM1-4: Timeout during connect (likely firewall problem)","status":400}
["url"] "https://acme-v02.api.letsencrypt.org/acme/chall-v3/357319482982/oR-gvw"
["token"] "9NUgxoqAKvHt_H77xE6PCnFdCSuooZ2rnrIyIokM1-4"
["validationRecord",0,"url"] "http://XXX.mydomain.de/.well-known/acme-challenge/9NUgxoqAKvHt_H77xE6PCnFdCSuooZ2rnrIyIokM1-4"
["validationRecord",0,"hostname"] "XXX.mydomain.de"
["validationRecord",0,"port"] "80"
["validationRecord",0,"addressesResolved",0] "178.27.xxx.xx"
["validationRecord",0,"addressesResolved"] ["178.27.xxx.xx"]
["validationRecord",0,"addressUsed"] "178.27.xxx.xx"
["validationRecord",0] {"url":"http://XXX.mydomain.de/.well-known/acme-challenge/9NUgxoqAKvHt_H77xE6PCnFdCSuooZ2rnrIyIokM1-4","hostname":"XXX.mydomain.de","port":"80","addressesResolved":["178.27.xxx.xx"],"addressUsed":"178.27.xxx.xx"}
["validationRecord",1,"url"] "https://XXX.mydomain.de/.well-known/acme-challenge/9NUgxoqAKvHt_H77xE6PCnFdCSuooZ2rnrIyIokM1-4"
["validationRecord",1,"hostname"] "XXX.mydomain.de"
["validationRecord",1,"port"] "443"
["validationRecord",1,"addressesResolved",0] "178.27.xxx.xx"
["validationRecord",1,"addressesResolved"] ["178.27.xxx.xx"]
["validationRecord",1,"addressUsed"] "178.27.xxx.xx"
["validationRecord",1] {"url":"https://XXX.mydomain.de/.well-known/acme-challenge/9NUgxoqAKvHt_H77xE6PCnFdCSuooZ2rnrIyIokM1-4","hostname":"XXX.mydomain.de","port":"443","addressesResolved":["178.27.xxx.xx"],"addressUsed":"178.27.xxx.xx"}
["validationRecord"] [{"url":"http://XXX.mydomain.de/.well-known/acme-challenge/9NUgxoqAKvHt_H77xE6PCnFdCSuooZ2rnrIyIokM1-4","hostname":"XXX.mydomain.de","port":"80","addressesResolved":["178.27.xxx.xx"],"addressUsed":"178.27.xxx.xx"},{"url":"https://XXX.mydomain.de/.well-known/acme-challenge/9NUgxoqAKvHt_H77xE6PCnFdCSuooZ2rnrIyIokM1-4","hostname":"XXX.mydomain.de","port":"443","addressesResolved":["178.27.xxx.xx"],"addressUsed":"178.27.xxx.xx"}]
["validated"] "2024-05-30T06:59:31Z")
I’ve already checked or tried the following point or steps:
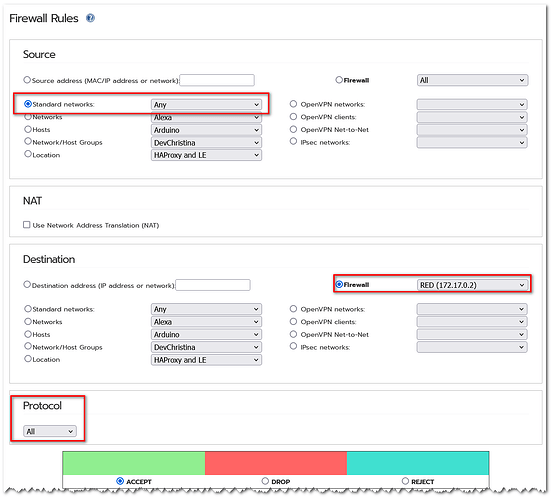
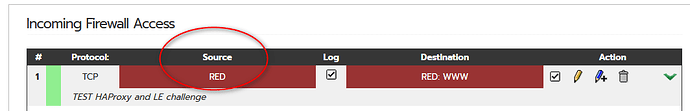
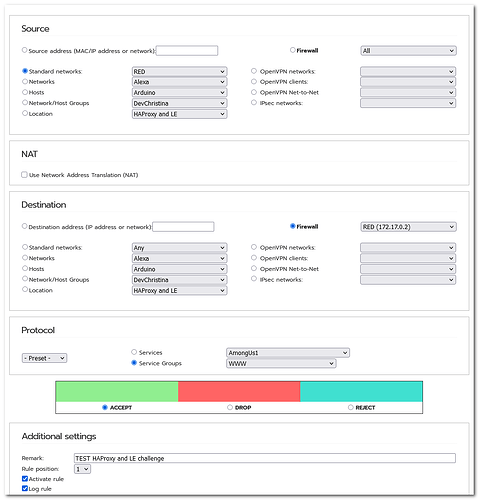
- The necessary vhost line in IPFire’s Apache http conf is in place and works as before
- Requesting the above mentioned token file, from Firefox, works using the path https://XXX.mydomain.de/.well-known/acme-challenge/9NUgxoqAKvHt_H77xE6PCnFdCSuooZ2rnrIyIokM1-4
Of course I get a certificate expired warning which Firefox let me pass, confirming the appropriate warning - I can request the token file from a IPFire SSH shell using the URI http://XXX.mydomain.de/.well-known/acme-challenge/9NUgxoqAKvHt_H77xE6PCnFdCSuooZ2rnrIyIokM1-4 with http protocol, to see if redirection from http to https (HAproxy configuration!) still works. Yes it works, get the warning about expired certificate as well of course
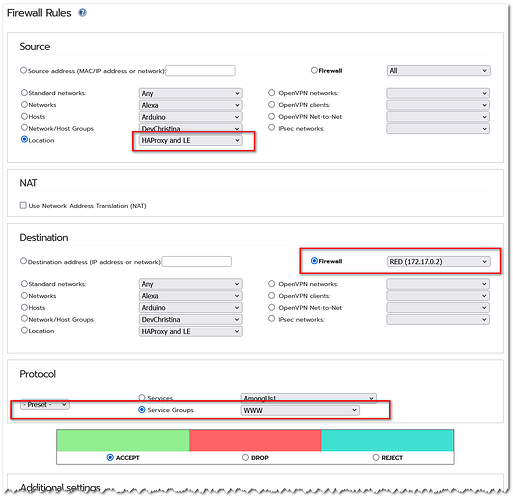
- I’ve GeoIP blocking in place within IPFire, but I disabled it completely and reloaded FW rules and re-checked the renewal process - still fails!
Previously, any well know countries (US, UK), where LE org’s servers are hosted, were excluded from Geo blocking. So, basically this should work without any chance on my side. - Various restarts of HAproxy done, to no avail!
The next step I’m testing:
- Disable SSL termination (redirects from http to https) in HAproxy’s config and start certification renewal again. Right now it’s not possible since LE blocks the process, because of too many tries

Nevertheless, I’m trying to find out what is happening and seeking for some hints in community.
So I would be happy to get some inputs on what to check what’s going on here on my side.
Thanks, Michael
Edit: HAproxy logs during the renewal process show:
10:48:36 haproxy[21501]: 162.142.125.34:33608 [30/May/2024:10:48:36.161] stats stats/<NOSRV> 0/-1/-1/-1/0 503 217 - - SC-- 2/2/0/0/0 0/0 "GET / HTTP/1.1"
10:48:30 haproxy[21501]: 34.222.23.129:28680 http_https letsencrypt/letsencrypt 200 242 ---- "GET /.well- known/acme-challenge/6FC2-H2NAiWQU5k7xxvFwBM3AiEwpTdz3l_dbBqkGkY HTTP/1.1"
10:48:29 haproxy[21501]: 3.145.10.139:39082 http_https letsencrypt/letsencrypt 200 242 ---- "GET /.well-k nown/acme-challenge/6FC2-H2NAiWQU5k7xxvFwBM3AiEwpTdz3l_dbBqkGkY HTTP/1.1"
10:48:26 haproxy[21501]: 162.142.125.34:33956 [30/May/2024:10:48:26.892] stats stats/<NOSRV> 0/-1/-1/-1/0 503 217 - - SC-- 2/2/0/0/0 0/0 "GET / HTTP/1.1"
10:48:22 haproxy[21501]: 162.142.125.34:33948 [30/May/2024:10:48:22.847] stats stats/<NOSRV> -1/-1/-1/-1/ 0 400 0 - - PR-- 2/2/0/0/0 0/0 "<BADREQ>"
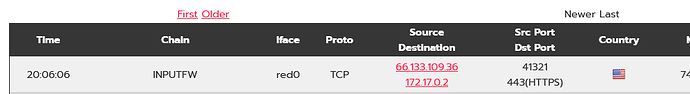
10:48:20 haproxy[21501]: 66.133.109.36:61141 http_https letsencrypt/letsencrypt 200 242 ---- "GET /.well- known/acme-challenge/6FC2-H2NAiWQU5k7xxvFwBM3AiEwpTdz3l_dbBqkGkY HTTP/1.1"
It looks to me, in the first line above, that HAproxy does not find any server to handle the request: .
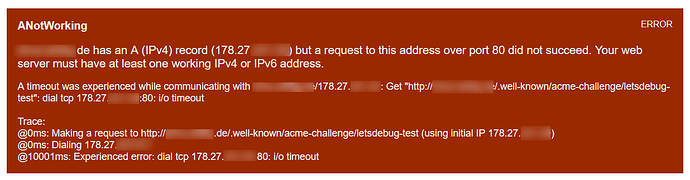
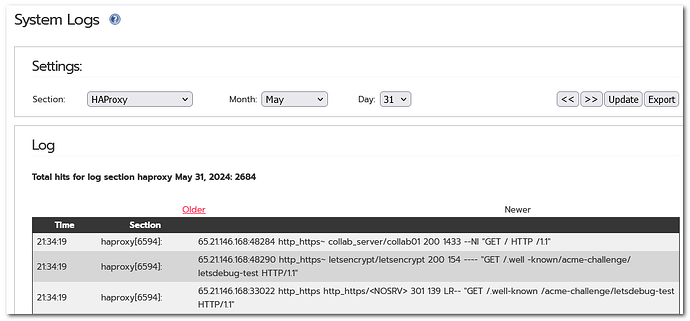
Edit2: Since LE has a debug web site, located here https://letsdebug.net/, I’ve done a test drive. The result is
The log gives me those lines:
11:41:21 haproxy[14946]: 66.133.109.36:40169 http_https~ letsencrypt/letsencrypt 404 340 ---- "GET /.well -known/acme-challenge/tn3RQ4apU59MV-QybN6H9fIV8GNOtM-t2RFcix_r6sU HTTP/1.1"
Does this mean that the Apache config does not work anymore?
# cat /etc/httpd/conf/vhosts.d/acme.conf
Listen 5001
<VirtualHost *:5001>
DocumentRoot "/var/www/dehydrated"
Alias /.well-known/acme-challenge/ /var/www/dehydrated/
</VirtualHost>
In my documentation, I’ve previously noted this error which usually points to some geoblocking in place. As written above, I’ve disabled Geo blocking in WebIf as well as IPS completely before running the debug test and during certification renewal, to no avail.
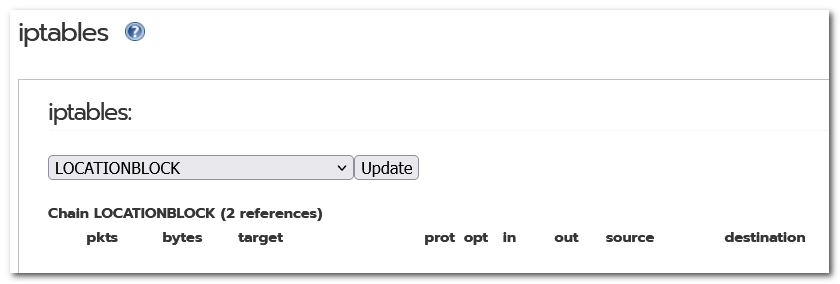
How can I check if geo blocking is still active in IPFire as it seems to be the case?
Should be disabled, right?
Whereas in a shell, gives:
# iptables -L |grep LOCATIONBLOCK
LOCATIONBLOCK all -- anywhere anywhere
LOCATIONBLOCK all -- anywhere anywhere
Chain LOCATIONBLOCK (2 references)
Is this an active blocking or not?