sec-con
21 December 2023 11:19
1
First of all, I do not pay a lot of attention to logs. They just gather too much information in many cases and ways of limiting them to show actually dangerous activity seems to be hard and require code.
The time is 12:15 and my log has
Total number of firewall hits for December 21, 2023: 24423
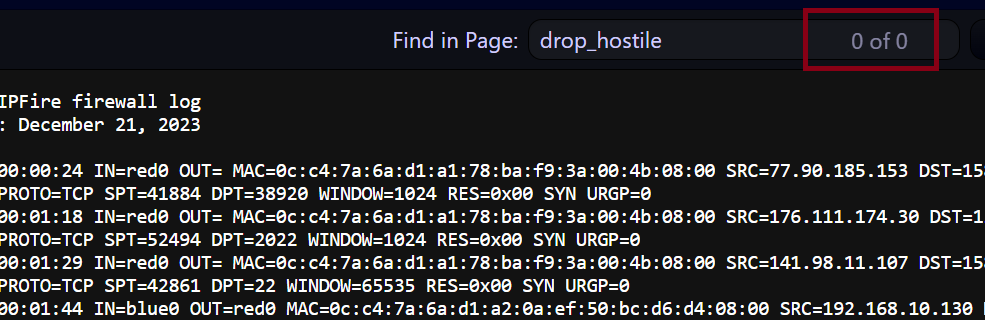
So just for a bit of fun, I thought I would make an export and sort out items labeled as
DROP_HOSTILE
So I click on Export and get a text based page with 24665 lines but zero entries labelled as DROP_HOSTILE . Ok?
Me no understand. I don’t speak “firewall”.
bbitsch
21 December 2023 13:30
2
You are right.
Alternatively you could try a search in /var/log/messages on the command line ( search tool is grep ).
1 Like
jon
21 December 2023 22:48
4
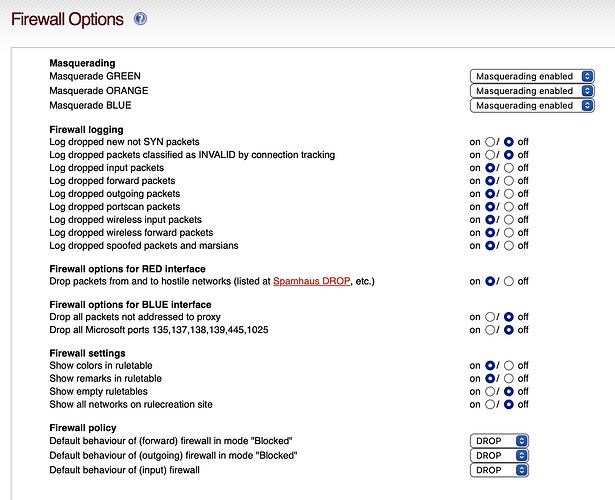
I get LOTS of DROP HOSTILEs. Please post a screenshot of your Firewall Options page.
Here is mine:
jon
21 December 2023 22:53
5
I think I see what you are saying. All the log names (e.g., DROP_xxxxxx) are missing.
Yes, please add this bug to bugzilla. That will help make sure the Development team reviews this information.
Login using your IPFire email address and your IPFire password .
IPFire Bugzilla
Bugzilla info in IPFire Wiki
EDIT:
[root@ipfire ~] # cat /var/log/messages | head -30
Dec 17 00:01:00 ipfire syslogd 1.5.1: restart (remote recep
Dec 17 00:01:01 ipfire kernel: DROP_HOSTILE IN=red0 OUT= MA
Dec 17 00:01:02 ipfire kernel: DROP_HOSTILE IN=red0 OUT= MA
Dec 17 00:01:05 ipfire dhcpd: CRE-Commit: ClientIP: 192.16
Dec 17 00:01:05 ipfire dhcpd: execute_statement argv[0] = /
Dec 17 00:01:05 ipfire dhcpd: execute_statement argv[1] = c
Dec 17 00:01:05 ipfire dhcpd: execute_statement argv[2] = 1
Dec 17 00:01:05 ipfire dhcpd: execute_statement argv[3] = i
Dec 17 00:01:05 ipfire dhcpEvent: testing --> /root/dhcpdco
Dec 17 00:01:06 ipfire dhcpEvent: commit: same -> iPhone-W0
Dec 17 00:01:06 ipfire dhcpEvent: commit: same hostname & s
Dec 17 00:01:06 ipfire dhcpEvent: commit: finished
Dec 17 00:01:06 ipfire dhcpd: DHCPREQUEST for 192.168.65.11
Dec 17 00:01:06 ipfire dhcpd: DHCPACK on 192.168.65.110 to
Dec 17 00:01:06 ipfire kernel: DROP_HOSTILE IN=red0 OUT= MA
Dec 17 00:01:07 ipfire kernel: DROP_HOSTILE IN=red0 OUT= MA
Dec 17 00:01:07 ipfire kernel: DROP_HOSTILE IN=red0 OUT= MA
Dec 17 00:01:09 ipfire unbound: [7526:0] info: validation f
Dec 17 00:01:12 ipfire unbound: [7526:0] info: rpz: applied
Dec 17 00:01:14 ipfire kernel: DROP_HOSTILE IN=red0 OUT= MA
Dec 17 00:01:15 ipfire unbound: [7526:0] info: rpz: applied
Dec 17 00:01:15 ipfire unbound: [7526:0] info: rpz: applied
Dec 17 00:01:16 ipfire kernel: DROP_HOSTILE IN=red0 OUT= MA
Dec 17 00:01:16 ipfire unbound: [7526:0] info: rpz: applied
Dec 17 00:01:27 ipfire kernel: DROP_FORWARD IN=blue0 OUT=gr
Dec 17 00:01:27 ipfire kernel: BLKLST_CIARMY IN=red0 OUT= M
Dec 17 00:01:28 ipfire rsnapshot[7436]: /usr/bin/rsnapshot
Dec 17 00:01:28 ipfire rsnapshot[7594]: /usr/bin/rsnapshot
Dec 17 00:01:29 ipfire kernel: DROP_HOSTILE IN=red0 OUT= MA
Dec 17 00:01:32 ipfire kernel: DROP_HOSTILE IN=red0 OUT= MA
hvacguy
22 December 2023 01:36
6
Wow @jon thats hard core.
jon
22 December 2023 02:51
7
my set-up? No, not as blocked as I would like…
sec-con
22 December 2023 05:47
8
As per request by the non-expert…
I will spam GodZilla a bit later. When the sun is up…
bonnietwin
22 December 2023 12:47
10
Patch with the fix has been submitted.
5 Likes
sec-con
22 December 2023 12:59
11
seen it, commented, that was fast…
bonnietwin
22 December 2023 13:09
12
Well i wasn’t doing anything else when i was reading this thread so i had a look at the code and the fix turned out to be quite simple. Glad to have been able to help.
8 Likes
bonnietwin
29 December 2023 11:12
13
11 posts were merged into an existing topic: Improving Usability?