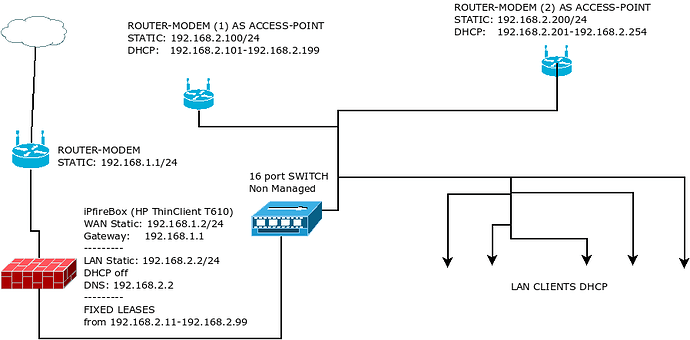
Hello, please anybody, I’m going to setup a firewall-proxy with ipFire on HP Thin Client T610 plus, which has two NIC’s, one for WAN other for LAN.
Because the need for children internet access time control and URL filtering, plus giving free WiFi access with secret password to visitors and filtered WiFi access to children mobile devices, I want to setup two router-modems configured as access points, as the attached diagram.
Any thoughts and suggestions please. Will it work as the diagram or need to make changes?
Also do I need to give fixed leases for modem-routers?
Thank you.
Probably ipFireBox LAN DHCP should be ON.
Hi,
sorry for the tardy reply.
If I understood the diagram correct - thank you for providing it, this is very helpful  - both WiFi access points run a DHCP server, serving the same broadcast domain.
- both WiFi access points run a DHCP server, serving the same broadcast domain.
This should work somehow, but I think it is better to disable the DHCP server everywhere except for your IPFire’s GREEN interface. That way, any client in your network requesting a DHCP lease will be served by IPFire, where you can configure fixed leases as well, and you avoid collisions between the two DHCP servers on the access points.
Of course, you will have to enable the DHCP server on IPFire if you want to use fixed leases there. 
Aside from that, I do not see any reason why this setup should not work.
Thanks, and best regards,
Peter Müller
Thank you sir. The whole thought is to separate WiFi Access-Points for different use, one for kids which will have time limits and web filtering for browsing and gaming, and another one for visitors -both with password- but for visitors a password “hidden” from kids, to give them more freedom without kids can access it. Of course by making fixed leases, it should be difficult to bypass security, but additionally they have mobiles, so trying to do the best I can.
The main problem for me is “if I must give fixed leases in ipFireBox for the routers that work as access-points, or not”, even by giving static IP’s.
Thank you for your time, any advice is welcome for me, because of my low level knowledge.
Hmmm, thinking again your solution, it could be much better than what I’m thinking to do.
Only problem about routers fixed leases, should I give fixed leases or not.
Thanks again.
Hi,
giving the description of your setup, you will probably need those:
Initially, you will need to configure fixed DHCP leases for any device used by your children. Ideally, use a dedicated segment of your entire GREEN/BLUE IP address range, so you can tell them apart easily after.
For example, if 192.0.2.0/24 is the IP address range you use for your network (it is a reserved netblock, though, so I just it for documentary purposes here ![]() ), and IPFire has
), and IPFire has 192.0.2.1 assigned, you could assign fixed DHCP leases for your children within 192.0.2.32/27, which equals 192.0.2.32 to 192.0.2.63 (32 IPv4 addresses in total).
Done that, configure IPFire’s DHCP server to serve a bigger network range, so you have IP space left for guest devices logging into your WiFi. Then, create a firewall rule to drop any traffic from 192.0.2.32/27 to the internet, so these clients will have to use IPFire’s web proxy in order to access websites.
(Also, consider redirecting DNS traffic to your IPFire, in case any device or app comes with a hard-coded DNS resolver.)
You can now configure the URL filter as appropriate for your children. Any other client on your network can access websites directly, bypassing the proxy unless configured to use it.
Please note tech-savvy kids might find a way around this by setting the IP address on their devices statically to anything outside 192.0.2.32/27, changing their MAC addresses to obtain a fresh lease from IPFire’s DHCP server, or simply turning off WiFi and using cellular network only. Technical measures never make education optional. ![]()
Thanks, and best regards,
Peter Müller
Sir, you opened my mind with your suggestions for network configuration. It was like you opened a door to go through, just when I was in the end. Thanks a lot.
All done in the way you suggested:
- Set double fixed leases for LAN & WiFi Laptops MAC addresses, and configured ipfire Green DHCP range out of those addresses.
- Set Firewall rule as described in “wiki.ipfire.org - Force clients to use IPFire DNS Server”.
All working fine. Now please, if I have to set time and site limit access:
a. Should I use both Firewall rules and Proxy time settings, and if so should they be the same?
b. If I set time limit access only in firewall rules, how can I block access to some sites in some days?
c. Should I have a rule for Proxy in Firewall rules?
d. Can I set “time restrictions” in Proxy for some sites in some days and hours, out of firewall day/hours block access?
Tried to find answers by searching a lot, but you see, everyone has it’s own needs.
Thank you.
Hi,
this depends on what you want to achieve. The proxy time constraints will only have effect on those clients using the proxy (in this case, your children’s devices).
On the other hand, the firewall time constraints will apply to any communication permitted or denied by that firewall rule. In your case, that might affect all the other network devices in your WiFi, depending on the firewall rule you configure time constrains for.
Perhaps it would be easier to advise you if you could describe what you intend to do. ![]()
This is complicated: Actually, the thing we refer to as a “firewall” is more precisely described as a “packet filter”, working on layer 2 to 4 in the OSI model. There, you will only “see” IP addresses and port numbers, but not the actual application traffic (such as HTTPS).
If the web sites you are referring to are hosted exclusively on a bunch of distinct IP addresses, you could create a firewall rule permitting communication to those addresses within a certain timeframe. Technically, that rule won’t match on the web sites, but on the IP addresses hosting them. If there is an 1:1-relation between them, you won’t notice a difference.
Today, especially larger websites are often served by a Content Delivery Network (CDN). Talking about layer 3 and 4, this means a single IP address can “host” thousands of websites. Working with firewall rules here is pretty error-prone, as blocking the entire IP address creates lots of false positives.
This is why we have a web proxy, because it actually works on higher OSI layers, “seeing” at least the FQDN of the web site a device wants to talk to. That way, access can be controlled on a FQDN-basis, which is much more accurate than only dealing with IP addresses.
To cut it short: If the sites in question are served by a CDN, you will probably need the clients you want to restrict to use IPFire’s web proxy.
Could you elaborate a bit more on this? What is “rule” and “proxy” referring to? Firewall rules and proxy traffic?
Yes. Both time constraints are completely separated from each other.
No problem. Glad to help. ![]()
Thanks, and best regards,
Peter Müller
Sir, first of all thank you very much for your time. I’m trying to understand how proxy and firewall configurations can affect each other.
-All I want most, is to control time access from clients to internet (parental control).
[Trying some settings found that I can do this in firewall rules, by “drop” access for a specific client IP address (which there is in DHCP fixed leases), to RED interface, but will it drop connection after time limit ends?].
-And if possible (secondary but desired), to restrict access to some specific sites like “minecraft” or other game sites, also in youtube, and perhaps porn sites, by setting specific date/time limits and manual configured banned lists. By this time it’s a headache to me, because I don’t know if and how it depends on firewall rules.
-Following your previous suggestions, I made firewall hosts and groups, which group contains the IP addresses of users devices. Now I have to make all other stuff.
You see, I insist on use ipFire firewall, because it’s familiar to me (because of linux), and also it has all settings I need, such the plenty of proxy settings, even thought I don’t can “yet” handle them.
BUT, it has it’s cost for me, been a home user with few know-how on some important thinks.
So, keep trying, searching, asking and reading!!!
Hi,
apologies for my tardy reply.
I see. Configuring this via the proxy time constraints would be my first approach to do so.
Yes, that should work as well, but you will have to set the “destination” to the RED zone, not the RED interface of IPFire.
To the best of my knowledge, the time constraint functionality of firewall rules works well, but does not apply to connections already established. So, if a client established a connection at 9:59 pm, and keeps it opened/in use, it would still be established after 10 pm, even if new connections from the same client would then be blocked.
Providing your IPFire itself can access all those sites around the clock (because for the firewall engine, the web proxy causes connections to web sites to originate from IPFire itself, not from the actual client), then firewall rules won’t interfere here.
It might be helpful to enable logging for firewall rules, if you are unsure whether they are correct. If something stops working, you will then see the dropped packets logged, and can correct the firewall rule causing that.
I am glad to read IPFire is helpful to you. No worries about the knowledge - we were all beginners once. ![]()
Thanks, and best regards,
Peter Müller
Dear Sir, I have no words to say thank you for your answers and all that time you spend for me.
You gave me a lot of clear answers, and if it’s possible for you, I’d like to ask some more explanations about all these. I’ll write here my thoughts about ipfire configuration, and you can correct me.
So, as I have understand till now:
-
First of all I must set the following firewall rules,
a) block clients to bypass ipfire as in “wiki.ipfire.org - Force clients to use IPFire DNS Server”,
b) deny access from “green to red” for HTTP & HTTPS (or the “a” is enough?),
c) deny access from “green to red” for “any to any”, else which of a,b,c rules is OK?
d) by setting all or some of the above rules, will client requests go to proxy OR must set another rule to “reject” clients on proxy port? -
Have been set custom DNS servers from “DNS Servers - uncensoreddns blog”, and in DNS configuration I have set:
a) Unchecked “ISP-assigned DNS servers”,
b) Set “Protocol for DNS queries” the TLS,
c) Checked the “Enable Safe Search”,
d) Set “QNAME Minimisation” to “strict”.
(All DNS settings looks that work, I did not had any problem by accessing internet).
That’s all (hope to be correct), you see need to understand the way that client requests go through IPFire, so that can handle the whole traffic.
Thank you very much again. I offer a lot to you.
Hi,
first of all, apologies for my tardy reply. I thought I answered your post already, but now realised I did not. ![]()
Yes, that can never hurt, but keep in mind this one only applies to DNS.
Yes, this is needed to prevent clients from establishing HTTP(S) connections to the internet directly. Since you mentioned some clients should be allowed to do this, it might make sense to limit this rule to the clients that must use IPFire’s proxy.
In general, I think it is less work to block all network traffic, and only allow the traffic you want to permit. In this case, blocking traffic to destination ports 80 and 443 works, but clients can bypass this if they find an open proxy on the internet that runs on a different port (such as 8080).
Therefore, changing the firewall default policy to block outgoing and forwarded connections would be the more robust approach. Please keep in mind you will then have to create firewall rules for all traffic that needs to be allowed (DNS, NTP, etc.) - see this blog post for details.
The DNS configuration looks fine to me. To increase robustness in case that DNS provider becomes unreachable, consider adding some more DNS servers to your configuration. Here is a list of them - any server supporting DNS over TLS is fine.
Thanks, and best regards,
Peter Müller
For one more time thank you Sir.
So, as you suggest, the best and safest way for my needs, is to block all outgoing network traffic.
Doing this, and leaving the already been settings for DNS, will all traffic go through proxy or I have to make a rule for allowing that, and if so how to do it (force to proxy and allow proxy to outgoing)?
Sorry but it’s to complicated for me, and going on step by step each time.
Also the way that ipFire internal rules works is not clear to me, and cannot set the necessary rules for all network, internal and outgoing.
Now I had a problem with a network card that hanged all my ipFire-Box, and until to find what was the problem, took me a lot of time and work.
Now I’m going to get another one, used in good condition but also with 4 ports, so that can do more to my LAN.