So here are two tcpdumps when the client accessing the internal wiki.
One time with the rule destination network any and one with destination network red.
To me, it seems that it just doesnt work the way it should.
Also… why doesnt it show up in the logs as rejected?
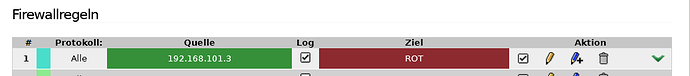
Proto:ANY, SRC: 192.168.101.3, DST: Network ANY, Action: Reject
[root@firwall~]# tcpdump -i green0 host 192.168.101.3 and not port 3389 -v -nnn
tcpdump: listening on green0, link-type EN10MB (Ethernet), capture size 262144 bytes
14:10:16.075949 IP (tos 0x0, ttl 1, id 21576, offset 0, flags [none], proto UDP (17), length 32)
192.168.101.3.53016 > 229.111.112.12.3071: UDP, length 4
14:10:18.382075 IP (tos 0x0, ttl 255, id 29993, offset 0, flags [none], proto UDP (17), length 62)
192.168.101.3.5353 > 224.0.0.251.5353: 0 [2q] A (QM)? wiki.local. AAAA (QM)? wiki.local. (34)
14:10:19.390678 IP (tos 0x0, ttl 255, id 29994, offset 0, flags [none], proto UDP (17), length 62)
192.168.101.3.5353 > 224.0.0.251.5353: 0 [2q] A (QM)? wiki.local. AAAA (QM)? wiki.local. (34)
14:10:21.343345 IP (tos 0x0, ttl 1, id 21577, offset 0, flags [none], proto UDP (17), length 32)
192.168.101.3.53016 > 229.111.112.12.3071: UDP, length 4
14:10:23.446780 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.101.3 tell 192.168.101.254, length 28
14:10:23.446924 ARP, Ethernet (len 6), IPv4 (len 4), Reply 192.168.101.3 is-at 00:50:56:ad:18:e7, length 46
14:10:26.619972 IP (tos 0x0, ttl 1, id 21578, offset 0, flags [none], proto UDP (17), length 32)
192.168.101.3.53016 > 229.111.112.12.3071: UDP, length 4
14:10:27.645470 IP (tos 0x2,ECT(0), ttl 128, id 12217, offset 0, flags [DF], proto TCP (6), length 52)
192.168.101.3.52653 > 216.58.207.170.443: Flags [SEW], cksum 0x62bf (correct), seq 2389033009, win 8192, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
14:10:27.645648 IP (tos 0xc2,ECT(0), ttl 64, id 13728, offset 0, flags [none], proto ICMP (1), length 80)
192.168.101.254 > 192.168.101.3: ICMP 216.58.207.170 tcp port 443 unreachable, length 60
IP (tos 0x2,ECT(0), ttl 127, id 12217, offset 0, flags [DF], proto TCP (6), length 52)
192.168.101.3.52653 > 216.58.207.170.443: Flags [SEW], cksum 0x62c7 (correct), seq 2389033009, win 8192, options [mss 1452,nop,wscale 8,nop,nop,sackOK], length 0
14:10:27.897125 IP (tos 0x2,ECT(0), ttl 128, id 12218, offset 0, flags [DF], proto TCP (6), length 52)
192.168.101.3.52654 > 216.58.207.170.443: Flags [SEW], cksum 0xc366 (correct), seq 3146330725, win 8192, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
14:10:27.897307 IP (tos 0xc2,ECT(0), ttl 64, id 13745, offset 0, flags [none], proto ICMP (1), length 80)
192.168.101.254 > 192.168.101.3: ICMP 216.58.207.170 tcp port 443 unreachable, length 60
IP (tos 0x2,ECT(0), ttl 127, id 12218, offset 0, flags [DF], proto TCP (6), length 52)
192.168.101.3.52654 > 216.58.207.170.443: Flags [SEW], cksum 0xc36e (correct), seq 3146330725, win 8192, options [mss 1452,nop,wscale 8,nop,nop,sackOK], length 0
14:10:30.296424 IP (tos 0x2,ECT(0), ttl 128, id 28494, offset 0, flags [DF], proto TCP (6), length 52)
192.168.101.3.52655 > 172.217.20.227.80: Flags [SEW], cksum 0x1c34 (correct), seq 2394484219, win 8192, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
14:10:30.296539 IP (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 52)
172.217.20.227.80 > 192.168.101.3.52655: Flags [S.], cksum 0xe78e (incorrect -> 0xfd7d), seq 465416598, ack 2394484220, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 9], length 0
14:10:30.296694 IP (tos 0x0, ttl 128, id 28495, offset 0, flags [DF], proto TCP (6), length 40)
192.168.101.3.52655 > 172.217.20.227.80: Flags [.], cksum 0xaf62 (correct), ack 1, win 256, length 0
14:10:30.296863 IP (tos 0x0, ttl 128, id 28496, offset 0, flags [DF], proto TCP (6), length 374)
192.168.101.3.52655 > 172.217.20.227.80: Flags [P.], cksum 0xa821 (correct), seq 1:335, ack 1, win 256, length 334: HTTP, length: 334
GET /generate_204 HTTP/1.1
Host: www.gstatic.com
Connection: keep-alive
Pragma: no-cache
Cache-Control: no-cache
User-Agent: Mozilla/5.0 (Windows NT 6.3; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.198 Safari/537.36
Accept-Encoding: gzip, deflate
Accept-Language: de-DE,de;q=0.9,en-US;q=0.8,en;q=0.7
14:10:30.296992 IP (tos 0x0, ttl 64, id 832, offset 0, flags [DF], proto TCP (6), length 40)
172.217.20.227.80 > 192.168.101.3.52655: Flags [.], cksum 0xe782 (incorrect -> 0xaed8), ack 335, win 60, length 0
14:10:30.359109 IP (tos 0x0, ttl 64, id 833, offset 0, flags [DF], proto TCP (6), length 250)
172.217.20.227.80 > 192.168.101.3.52655: Flags [P.], cksum 0xe854 (incorrect -> 0x4893), seq 1:211, ack 335, win 60, length 210: HTTP, length: 210
HTTP/1.1 204 No Content
Content-Length: 0
Date: Wed, 25 Nov 2020 13:10:29 GMT
X-Cache: MISS from firewall.customer.local
X-Cache-Lookup: MISS from firewall.customer.local:800
Connection: keep-alive
14:10:30.410115 IP (tos 0x0, ttl 128, id 28497, offset 0, flags [DF], proto TCP (6), length 40)
192.168.101.3.52655 > 172.217.20.227.80: Flags [.], cksum 0xad43 (correct), ack 211, win 255, length 0
14:10:30.639434 IP (tos 0x2,ECT(0), ttl 128, id 12219, offset 0, flags [DF], proto TCP (6), length 52)
192.168.101.3.52653 > 216.58.207.170.443: Flags [SEW], cksum 0x62bf (correct), seq 2389033009, win 8192, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
14:10:30.639619 IP (tos 0xc2,ECT(0), ttl 64, id 13793, offset 0, flags [none], proto ICMP (1), length 80)
192.168.101.254 > 192.168.101.3: ICMP 216.58.207.170 tcp port 443 unreachable, length 60
IP (tos 0x2,ECT(0), ttl 127, id 12219, offset 0, flags [DF], proto TCP (6), length 52)
192.168.101.3.52653 > 216.58.207.170.443: Flags [SEW], cksum 0x62c7 (correct), seq 2389033009, win 8192, options [mss 1452,nop,wscale 8,nop,nop,sackOK], length 0
14:10:30.900717 IP (tos 0x2,ECT(0), ttl 128, id 12220, offset 0, flags [DF], proto TCP (6), length 52)
192.168.101.3.52654 > 216.58.207.170.443: Flags [SEW], cksum 0xc366 (correct), seq 3146330725, win 8192, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
14:10:30.900866 IP (tos 0xc2,ECT(0), ttl 64, id 13819, offset 0, flags [none], proto ICMP (1), length 80)
192.168.101.254 > 192.168.101.3: ICMP 216.58.207.170 tcp port 443 unreachable, length 60
IP (tos 0x2,ECT(0), ttl 127, id 12220, offset 0, flags [DF], proto TCP (6), length 52)
192.168.101.3.52654 > 216.58.207.170.443: Flags [SEW], cksum 0xc36e (correct), seq 3146330725, win 8192, options [mss 1452,nop,wscale 8,nop,nop,sackOK], length 0
14:10:31.912569 IP (tos 0x0, ttl 1, id 21579, offset 0, flags [none], proto UDP (17), length 32)
192.168.101.3.53016 > 229.111.112.12.3071: UDP, length 4
14:10:35.419474 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.101.254 (0c:c4:7a:e4:5b:78) tell 192.168.101.3, length 46
14:10:35.419505 ARP, Ethernet (len 6), IPv4 (len 4), Reply 192.168.101.254 is-at 0c:c4:7a:e4:5b:78, length 28
14:10:36.637594 IP (tos 0x0, ttl 128, id 12221, offset 0, flags [DF], proto TCP (6), length 48)
192.168.101.3.52653 > 216.58.207.170.443: Flags [S], cksum 0x778e (correct), seq 2389033009, win 8192, options [mss 1460,nop,nop,sackOK], length 0
14:10:36.637739 IP (tos 0xc0, ttl 64, id 13879, offset 0, flags [none], proto ICMP (1), length 76)
192.168.101.254 > 192.168.101.3: ICMP 216.58.207.170 tcp port 443 unreachable, length 56
IP (tos 0x0, ttl 127, id 12221, offset 0, flags [DF], proto TCP (6), length 48)
192.168.101.3.52653 > 216.58.207.170.443: Flags [S], cksum 0x7796 (correct), seq 2389033009, win 8192, options [mss 1452,nop,nop,sackOK], length 0
14:10:36.897660 IP (tos 0x0, ttl 128, id 12222, offset 0, flags [DF], proto TCP (6), length 48)
192.168.101.3.52654 > 216.58.207.170.443: Flags [S], cksum 0xd835 (correct), seq 3146330725, win 8192, options [mss 1460,nop,nop,sackOK], length 0
14:10:36.897817 IP (tos 0xc0, ttl 64, id 13910, offset 0, flags [none], proto ICMP (1), length 76)
192.168.101.254 > 192.168.101.3: ICMP 216.58.207.170 tcp port 443 unreachable, length 56
IP (tos 0x0, ttl 127, id 12222, offset 0, flags [DF], proto TCP (6), length 48)
192.168.101.3.52654 > 216.58.207.170.443: Flags [S], cksum 0xd83d (correct), seq 3146330725, win 8192, options [mss 1452,nop,nop,sackOK], length 0
14:10:37.191200 IP (tos 0x0, ttl 1, id 21580, offset 0, flags [none], proto UDP (17), length 32)
192.168.101.3.53016 > 229.111.112.12.3071: UDP, length 4
14:10:42.467671 IP (tos 0x0, ttl 1, id 21581, offset 0, flags [none], proto UDP (17), length 32)
192.168.101.3.53016 > 229.111.112.12.3071: UDP, length 4
14:10:47.756698 IP (tos 0x0, ttl 1, id 21582, offset 0, flags [none], proto UDP (17), length 32)
192.168.101.3.53016 > 229.111.112.12.3071: UDP, length 4
14:10:48.896969 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.101.22 tell 192.168.101.3, length 46
14:10:48.927449 IP (tos 0x0, ttl 128, id 25235, offset 0, flags [none], proto UDP (17), length 77)
192.168.101.3.58674 > 190.168.101.106.53: 42775+ A? content-autofill.googleapis.com. (49)
14:10:48.927587 IP (tos 0xc0, ttl 64, id 14955, offset 0, flags [none], proto ICMP (1), length 105)
192.168.101.254 > 192.168.101.3: ICMP 190.168.101.106 udp port 53 unreachable, length 85
IP (tos 0x0, ttl 127, id 25235, offset 0, flags [none], proto UDP (17), length 77)
192.168.101.3.58674 > 190.168.101.106.53: 42775+ A? content-autofill.googleapis.com. (49)
14:10:48.928020 IP (tos 0x2,ECT(0), ttl 128, id 12113, offset 0, flags [DF], proto TCP (6), length 52)
192.168.101.3.52660 > 172.217.20.234.443: Flags [SEW], cksum 0x6d79 (correct), seq 583141174, win 8192, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
14:10:48.928208 IP (tos 0xc2,ECT(0), ttl 64, id 14956, offset 0, flags [none], proto ICMP (1), length 80)
192.168.101.254 > 192.168.101.3: ICMP 172.217.20.234 tcp port 443 unreachable, length 60
IP (tos 0x2,ECT(0), ttl 127, id 12113, offset 0, flags [DF], proto TCP (6), length 52)
192.168.101.3.52660 > 172.217.20.234.443: Flags [SEW], cksum 0x6d81 (correct), seq 583141174, win 8192, options [mss 1452,nop,wscale 8,nop,nop,sackOK], length 0
14:10:49.153027 IP (tos 0x2,ECT(0), ttl 128, id 12114, offset 0, flags [DF], proto TCP (6), length 52)
192.168.101.3.52661 > 172.217.20.234.443: Flags [SEW], cksum 0xde1a (correct), seq 1148089575, win 8192, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
14:10:49.153172 IP (tos 0xc2,ECT(0), ttl 64, id 15001, offset 0, flags [none], proto ICMP (1), length 80)
192.168.101.254 > 192.168.101.3: ICMP 172.217.20.234 tcp port 443 unreachable, length 60
IP (tos 0x2,ECT(0), ttl 127, id 12114, offset 0, flags [DF], proto TCP (6), length 52)
192.168.101.3.52661 > 172.217.20.234.443: Flags [SEW], cksum 0xde22 (correct), seq 1148089575, win 8192, options [mss 1452,nop,wscale 8,nop,nop,sackOK], length 0
14:10:49.236377 IP (tos 0x2,ECT(0), ttl 128, id 12115, offset 0, flags [DF], proto TCP (6), length 52)
192.168.101.3.52662 > 172.217.20.234.443: Flags [SEW], cksum 0x2421 (correct), seq 33452368, win 8192, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
14:10:49.236518 IP (tos 0xc2,ECT(0), ttl 64, id 15022, offset 0, flags [none], proto ICMP (1), length 80)
192.168.101.254 > 192.168.101.3: ICMP 172.217.20.234 tcp port 443 unreachable, length 60
IP (tos 0x2,ECT(0), ttl 127, id 12115, offset 0, flags [DF], proto TCP (6), length 52)
192.168.101.3.52662 > 172.217.20.234.443: Flags [SEW], cksum 0x2429 (correct), seq 33452368, win 8192, options [mss 1452,nop,wscale 8,nop,nop,sackOK], length 0
^C
41 packets captured
41 packets received by filter
0 packets dropped by kernel
[root@firewall~]#
################################################################################################################################################################################################################
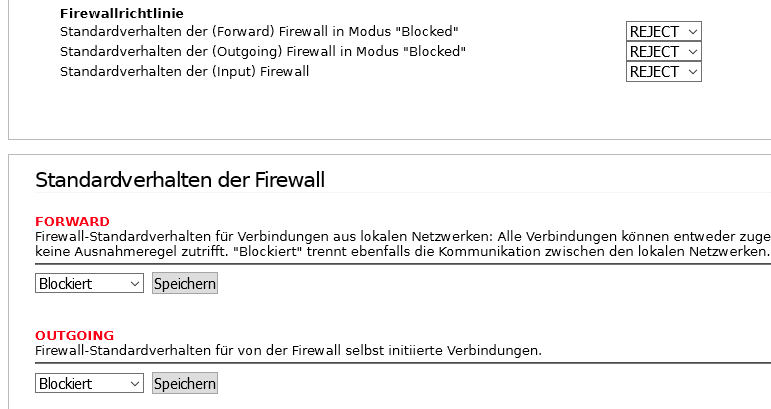
Proto:ANY, SRC: 192.168.101.3, DST: Network RED, Action: Reject
[root@firewall ~]# tcpdump -i green0 host 192.168.101.3 and not port 3389 -v -nnn
tcpdump: listening on green0, link-type EN10MB (Ethernet), capture size 262144 bytes
14:13:59.891024 IP (tos 0x0, ttl 255, id 29995, offset 0, flags [none], proto UDP (17), length 62)
192.168.101.3.5353 > 224.0.0.251.5353: 0 [2q] A (QM)? wiki.local. AAAA (QM)? wiki.local. (34)
14:14:00.900365 IP (tos 0x0, ttl 255, id 29996, offset 0, flags [none], proto UDP (17), length 62)
192.168.101.3.5353 > 224.0.0.251.5353: 0 [2q] A (QM)? wiki.local. AAAA (QM)? wiki.local. (34)
14:14:01.830887 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.101.172 tell 192.168.101.3, length 46
14:14:01.843381 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.101.22 tell 192.168.101.3, length 46
14:14:01.850022 IP (tos 0x2,ECT(0), ttl 128, id 1111, offset 0, flags [DF], proto TCP (6), length 52)
192.168.101.3.52688 > 172.217.16.195.80: Flags [SEW], cksum 0x8afc (correct), seq 1817617812, win 8192, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
14:14:01.850148 IP (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 52)
172.217.16.195.80 > 192.168.101.3.52688: Flags [S.], cksum 0xe36e (incorrect -> 0xe2bf), seq 3642064324, ack 1817617813, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 9], length 0
14:14:01.850323 IP (tos 0x0, ttl 128, id 1112, offset 0, flags [DF], proto TCP (6), length 40)
192.168.101.3.52688 > 172.217.16.195.80: Flags [.], cksum 0x94a4 (correct), ack 1, win 256, length 0
14:14:01.850500 IP (tos 0x0, ttl 128, id 1113, offset 0, flags [DF], proto TCP (6), length 374)
192.168.101.3.52688 > 172.217.16.195.80: Flags [P.], cksum 0x8d63 (correct), seq 1:335, ack 1, win 256, length 334: HTTP, length: 334
GET /generate_204 HTTP/1.1
Host: www.gstatic.com
Connection: keep-alive
Pragma: no-cache
Cache-Control: no-cache
User-Agent: Mozilla/5.0 (Windows NT 6.3; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.198 Safari/537.36
Accept-Encoding: gzip, deflate
Accept-Language: de-DE,de;q=0.9,en-US;q=0.8,en;q=0.7
14:14:01.850612 IP (tos 0x0, ttl 64, id 31146, offset 0, flags [DF], proto TCP (6), length 40)
172.217.16.195.80 > 192.168.101.3.52688: Flags [.], cksum 0xe362 (incorrect -> 0x941a), ack 335, win 60, length 0
14:14:01.911657 IP (tos 0x0, ttl 64, id 31147, offset 0, flags [DF], proto TCP (6), length 250)
172.217.16.195.80 > 192.168.101.3.52688: Flags [P.], cksum 0xe434 (incorrect -> 0x35d3), seq 1:211, ack 335, win 60, length 210: HTTP, length: 210
HTTP/1.1 204 No Content
Content-Length: 0
Date: Wed, 25 Nov 2020 13:14:01 GMT
X-Cache: MISS from firwall.customer.local
X-Cache-Lookup: MISS from firewall.customer.local:800
Connection: keep-alive
14:14:01.961294 IP (tos 0x0, ttl 128, id 1114, offset 0, flags [DF], proto TCP (6), length 40)
192.168.101.3.52688 > 172.217.16.195.80: Flags [.], cksum 0x9285 (correct), ack 211, win 255, length 0
14:14:02.764652 IP (tos 0x0, ttl 1, id 21619, offset 0, flags [none], proto UDP (17), length 32)
192.168.101.3.53016 > 229.111.112.12.3071: UDP, length 4
14:14:05.876011 IP (tos 0x0, ttl 128, id 25236, offset 0, flags [none], proto UDP (17), length 66)
192.168.101.3.50844 > 190.168.101.106.53: 21436+ A? fonts.googleapis.com. (38)
14:14:05.876176 IP (tos 0xc0, ttl 64, id 41565, offset 0, flags [none], proto ICMP (1), length 94)
192.168.101.254 > 192.168.101.3: ICMP 190.168.101.106 udp port 53 unreachable, length 74
IP (tos 0x0, ttl 127, id 25236, offset 0, flags [none], proto UDP (17), length 66)
192.168.101.3.50844 > 190.168.101.106.53: 21436+ A? fonts.googleapis.com. (38)
14:14:05.902872 IP (tos 0x2,ECT(0), ttl 128, id 12223, offset 0, flags [DF], proto TCP (6), length 52)
192.168.101.3.52692 > 216.58.207.170.443: Flags [SEW], cksum 0xd182 (correct), seq 599571440, win 8192, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
14:14:05.903047 IP (tos 0xc2,ECT(0), ttl 64, id 41569, offset 0, flags [none], proto ICMP (1), length 80)
192.168.101.254 > 192.168.101.3: ICMP 216.58.207.170 tcp port 443 unreachable, length 60
IP (tos 0x2,ECT(0), ttl 127, id 12223, offset 0, flags [DF], proto TCP (6), length 52)
192.168.101.3.52692 > 216.58.207.170.443: Flags [SEW], cksum 0xd18a (correct), seq 599571440, win 8192, options [mss 1452,nop,wscale 8,nop,nop,sackOK], length 0
14:14:06.102371 IP (tos 0x2,ECT(0), ttl 128, id 12224, offset 0, flags [DF], proto TCP (6), length 52)
192.168.101.3.52693 > 216.58.207.170.443: Flags [SEW], cksum 0x4d2f (correct), seq 409619349, win 8192, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
14:14:06.102558 IP (tos 0xc2,ECT(0), ttl 64, id 41576, offset 0, flags [none], proto ICMP (1), length 80)
192.168.101.254 > 192.168.101.3: ICMP 216.58.207.170 tcp port 443 unreachable, length 60
IP (tos 0x2,ECT(0), ttl 127, id 12224, offset 0, flags [DF], proto TCP (6), length 52)
192.168.101.3.52693 > 216.58.207.170.443: Flags [SEW], cksum 0x4d37 (correct), seq 409619349, win 8192, options [mss 1452,nop,wscale 8,nop,nop,sackOK], length 0
14:14:08.034617 IP (tos 0x0, ttl 1, id 21620, offset 0, flags [none], proto UDP (17), length 32)
192.168.101.3.53016 > 229.111.112.12.3071: UDP, length 4
14:14:08.903905 IP (tos 0x2,ECT(0), ttl 128, id 12225, offset 0, flags [DF], proto TCP (6), length 52)
192.168.101.3.52692 > 216.58.207.170.443: Flags [SEW], cksum 0xd182 (correct), seq 599571440, win 8192, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
14:14:08.904040 IP (tos 0xc2,ECT(0), ttl 64, id 41865, offset 0, flags [none], proto ICMP (1), length 80)
192.168.101.254 > 192.168.101.3: ICMP 216.58.207.170 tcp port 443 unreachable, length 60
IP (tos 0x2,ECT(0), ttl 127, id 12225, offset 0, flags [DF], proto TCP (6), length 52)
192.168.101.3.52692 > 216.58.207.170.443: Flags [SEW], cksum 0xd18a (correct), seq 599571440, win 8192, options [mss 1452,nop,wscale 8,nop,nop,sackOK], length 0
14:14:09.093982 IP (tos 0x2,ECT(0), ttl 128, id 12226, offset 0, flags [DF], proto TCP (6), length 52)
192.168.101.3.52693 > 216.58.207.170.443: Flags [SEW], cksum 0x4d2f (correct), seq 409619349, win 8192, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
14:14:09.094169 IP (tos 0xc2,ECT(0), ttl 64, id 41874, offset 0, flags [none], proto ICMP (1), length 80)
192.168.101.254 > 192.168.101.3: ICMP 216.58.207.170 tcp port 443 unreachable, length 60
IP (tos 0x2,ECT(0), ttl 127, id 12226, offset 0, flags [DF], proto TCP (6), length 52)
192.168.101.3.52693 > 216.58.207.170.443: Flags [SEW], cksum 0x4d37 (correct), seq 409619349, win 8192, options [mss 1452,nop,wscale 8,nop,nop,sackOK], length 0
14:14:13.321042 IP (tos 0x0, ttl 1, id 21621, offset 0, flags [none], proto UDP (17), length 32)
192.168.101.3.53016 > 229.111.112.12.3071: UDP, length 4
14:14:14.904798 IP (tos 0x0, ttl 128, id 12227, offset 0, flags [DF], proto TCP (6), length 48)
192.168.101.3.52692 > 216.58.207.170.443: Flags [S], cksum 0xe651 (correct), seq 599571440, win 8192, options [mss 1460,nop,nop,sackOK], length 0
14:14:14.904948 IP (tos 0xc0, ttl 64, id 43211, offset 0, flags [none], proto ICMP (1), length 76)
192.168.101.254 > 192.168.101.3: ICMP 216.58.207.170 tcp port 443 unreachable, length 56
IP (tos 0x0, ttl 127, id 12227, offset 0, flags [DF], proto TCP (6), length 48)
192.168.101.3.52692 > 216.58.207.170.443: Flags [S], cksum 0xe659 (correct), seq 599571440, win 8192, options [mss 1452,nop,nop,sackOK], length 0
14:14:15.094817 IP (tos 0x0, ttl 128, id 12228, offset 0, flags [DF], proto TCP (6), length 48)
192.168.101.3.52693 > 216.58.207.170.443: Flags [S], cksum 0x61fe (correct), seq 409619349, win 8192, options [mss 1460,nop,nop,sackOK], length 0
14:14:15.094992 IP (tos 0xc0, ttl 64, id 43254, offset 0, flags [none], proto ICMP (1), length 76)
192.168.101.254 > 192.168.101.3: ICMP 216.58.207.170 tcp port 443 unreachable, length 56
IP (tos 0x0, ttl 127, id 12228, offset 0, flags [DF], proto TCP (6), length 48)
192.168.101.3.52693 > 216.58.207.170.443: Flags [S], cksum 0x6206 (correct), seq 409619349, win 8192, options [mss 1452,nop,nop,sackOK], length 0
14:14:18.606839 IP (tos 0x0, ttl 1, id 21622, offset 0, flags [none], proto UDP (17), length 32)
192.168.101.3.53016 > 229.111.112.12.3071: UDP, length 4
14:14:23.897574 IP (tos 0x0, ttl 1, id 21623, offset 0, flags [none], proto UDP (17), length 32)
192.168.101.3.53016 > 229.111.112.12.3071: UDP, length 4
14:14:27.159396 IP (tos 0x0, ttl 128, id 25237, offset 0, flags [none], proto UDP (17), length 77)
192.168.101.3.52966 > 190.168.101.106.53: 602+ A? content-autofill.googleapis.com. (49)
14:14:27.159541 IP (tos 0xc0, ttl 64, id 43563, offset 0, flags [none], proto ICMP (1), length 105)
192.168.101.254 > 192.168.101.3: ICMP 190.168.101.106 udp port 53 unreachable, length 85
IP (tos 0x0, ttl 127, id 25237, offset 0, flags [none], proto UDP (17), length 77)
192.168.101.3.52966 > 190.168.101.106.53: 602+ A? content-autofill.googleapis.com. (49)
14:14:27.161912 IP (tos 0x2,ECT(0), ttl 128, id 5660, offset 0, flags [DF], proto TCP (6), length 52)
192.168.101.3.52697 > 216.58.206.10.443: Flags [SEW], cksum 0x45ed (correct), seq 2991241874, win 8192, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
14:14:27.162055 IP (tos 0xc2,ECT(0), ttl 64, id 43564, offset 0, flags [none], proto ICMP (1), length 80)
192.168.101.254 > 192.168.101.3: ICMP 216.58.206.10 tcp port 443 unreachable, length 60
IP (tos 0x2,ECT(0), ttl 127, id 5660, offset 0, flags [DF], proto TCP (6), length 52)
192.168.101.3.52697 > 216.58.206.10.443: Flags [SEW], cksum 0x45f5 (correct), seq 2991241874, win 8192, options [mss 1452,nop,wscale 8,nop,nop,sackOK], length 0
14:14:27.399808 IP (tos 0x2,ECT(0), ttl 128, id 5661, offset 0, flags [DF], proto TCP (6), length 52)
192.168.101.3.52698 > 216.58.206.10.443: Flags [SEW], cksum 0xb724 (correct), seq 519756970, win 8192, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
14:14:27.399974 IP (tos 0xc2,ECT(0), ttl 64, id 43591, offset 0, flags [none], proto ICMP (1), length 80)
192.168.101.254 > 192.168.101.3: ICMP 216.58.206.10 tcp port 443 unreachable, length 60
IP (tos 0x2,ECT(0), ttl 127, id 5661, offset 0, flags [DF], proto TCP (6), length 52)
192.168.101.3.52698 > 216.58.206.10.443: Flags [SEW], cksum 0xb72c (correct), seq 519756970, win 8192, options [mss 1452,nop,wscale 8,nop,nop,sackOK], length 0
14:14:27.475050 IP (tos 0x2,ECT(0), ttl 128, id 5662, offset 0, flags [DF], proto TCP (6), length 52)
192.168.101.3.52699 > 216.58.206.10.443: Flags [SEW], cksum 0x980a (correct), seq 751037946, win 8192, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
14:14:27.475233 IP (tos 0xc2,ECT(0), ttl 64, id 43596, offset 0, flags [none], proto ICMP (1), length 80)
192.168.101.254 > 192.168.101.3: ICMP 216.58.206.10 tcp port 443 unreachable, length 60
IP (tos 0x2,ECT(0), ttl 127, id 5662, offset 0, flags [DF], proto TCP (6), length 52)
192.168.101.3.52699 > 216.58.206.10.443: Flags [SEW], cksum 0x9812 (correct), seq 751037946, win 8192, options [mss 1452,nop,wscale 8,nop,nop,sackOK], length 0
14:14:29.190822 IP (tos 0x0, ttl 1, id 21624, offset 0, flags [none], proto UDP (17), length 32)
192.168.101.3.53016 > 229.111.112.12.3071: UDP, length 4
14:14:29.420084 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.101.3 tell 192.168.101.254, length 28
14:14:29.420252 ARP, Ethernet (len 6), IPv4 (len 4), Reply 192.168.101.3 is-at 00:50:56:ad:18:e7, length 46
14:14:30.159570 IP (tos 0x2,ECT(0), ttl 128, id 5663, offset 0, flags [DF], proto TCP (6), length 52)
192.168.101.3.52697 > 216.58.206.10.443: Flags [SEW], cksum 0x45ed (correct), seq 2991241874, win 8192, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
14:14:30.159726 IP (tos 0xc2,ECT(0), ttl 64, id 43760, offset 0, flags [none], proto ICMP (1), length 80)
192.168.101.254 > 192.168.101.3: ICMP 216.58.206.10 tcp port 443 unreachable, length 60
IP (tos 0x2,ECT(0), ttl 127, id 5663, offset 0, flags [DF], proto TCP (6), length 52)
192.168.101.3.52697 > 216.58.206.10.443: Flags [SEW], cksum 0x45f5 (correct), seq 2991241874, win 8192, options [mss 1452,nop,wscale 8,nop,nop,sackOK], length 0
^C
43 packets captured
43 packets received by filter
0 packets dropped by kernel
[root@firewall ~]#
and the firewall logs when i try to connect to an external https site, also takes forever until it says its not reachable…
[root@firewall ~]# tail -f /var/log/messages | grep '192.168.101.3 '
Nov 25 14:25:37 firewall kernel: FORWARDFW IN=green0 OUT=ppp0 MAC=0c:c4:7a:e4:5b:78:00:50:56:ad:18:e7:08:00 SRC=192.168.101.3 DST=193.99.144.85 LEN=52 TOS=0x02 PREC=0x00 TTL=127 ID=7546 DF PROTO=TCP SPT=52774 DPT=443 WINDOW=8192 RES=0x00 CWR ECE SYN URGP=0
Nov 25 14:25:37 firewall kernel: FORWARDFW IN=green0 OUT=ppp0 MAC=0c:c4:7a:e4:5b:78:00:50:56:ad:18:e7:08:00 SRC=192.168.101.3 DST=193.99.144.85 LEN=52 TOS=0x02 PREC=0x00 TTL=127 ID=7547 DF PROTO=TCP SPT=52775 DPT=443 WINDOW=8192 RES=0x00 CWR ECE SYN URGP=0
Nov 25 14:25:37 firewall kernel: FORWARDFW IN=green0 OUT=ppp0 MAC=0c:c4:7a:e4:5b:78:00:50:56:ad:18:e7:08:00 SRC=192.168.101.3 DST=193.99.144.85 LEN=52 TOS=0x02 PREC=0x00 TTL=127 ID=7548 DF PROTO=TCP SPT=52776 DPT=443 WINDOW=8192 RES=0x00 CWR ECE SYN URGP=0
Nov 25 14:25:40 firewall kernel: FORWARDFW IN=green0 OUT=ppp0 MAC=0c:c4:7a:e4:5b:78:00:50:56:ad:18:e7:08:00 SRC=192.168.101.3 DST=193.99.144.85 LEN=52 TOS=0x02 PREC=0x00 TTL=127 ID=7549 DF PROTO=TCP SPT=52774 DPT=443 WINDOW=8192 RES=0x00 CWR ECE SYN URGP=0
Nov 25 14:25:40 firewall kernel: FORWARDFW IN=green0 OUT=ppp0 MAC=0c:c4:7a:e4:5b:78:00:50:56:ad:18:e7:08:00 SRC=192.168.101.3 DST=193.99.144.85 LEN=52 TOS=0x02 PREC=0x00 TTL=127 ID=7550 DF PROTO=TCP SPT=52775 DPT=443 WINDOW=8192 RES=0x00 CWR ECE SYN URGP=0
Nov 25 14:25:40 firewall kernel: FORWARDFW IN=green0 OUT=ppp0 MAC=0c:c4:7a:e4:5b:78:00:50:56:ad:18:e7:08:00 SRC=192.168.101.3 DST=193.99.144.85 LEN=52 TOS=0x02 PREC=0x00 TTL=127 ID=7551 DF PROTO=TCP SPT=52776 DPT=443 WINDOW=8192 RES=0x00 CWR ECE SYN URGP=0
Nov 25 14:25:46 firewall kernel: FORWARDFW IN=green0 OUT=ppp0 MAC=0c:c4:7a:e4:5b:78:00:50:56:ad:18:e7:08:00 SRC=192.168.101.3 DST=193.99.144.85 LEN=48 TOS=0x00 PREC=0x00 TTL=127 ID=7552 DF PROTO=TCP SPT=52774 DPT=443 WINDOW=8192 RES=0x00 SYN URGP=0
Nov 25 14:25:46 firewall kernel: FORWARDFW IN=green0 OUT=ppp0 MAC=0c:c4:7a:e4:5b:78:00:50:56:ad:18:e7:08:00 SRC=192.168.101.3 DST=193.99.144.85 LEN=48 TOS=0x00 PREC=0x00 TTL=127 ID=7553 DF PROTO=TCP SPT=52775 DPT=443 WINDOW=8192 RES=0x00 SYN URGP=0
Nov 25 14:25:46 firewall kernel: FORWARDFW IN=green0 OUT=ppp0 MAC=0c:c4:7a:e4:5b:78:00:50:56:ad:18:e7:08:00 SRC=192.168.101.3 DST=193.99.144.85 LEN=48 TOS=0x00 PREC=0x00 TTL=127 ID=7554 DF PROTO=TCP SPT=52776 DPT=443 WINDOW=8192 RES=0x00 SYN URGP=0
^C
[root@firewall ~]#