Tim Richardson:
I’m finding the firewall rule setup very, very hard to understand.
It is indeed a complex topic with many nuances. It’s common to find it challenging initially.
On the Blue network, out of the box, I can’t ping a machine on the Green network.
By default, the blue network is quite restricted. To initiate communication, you will first need to allow the MAC address through, or remove the layer 2 block entirely. Following this, you can access the red interface and the firewall itself, though you might want to restrict access to the firewall to maintain a higher security level.
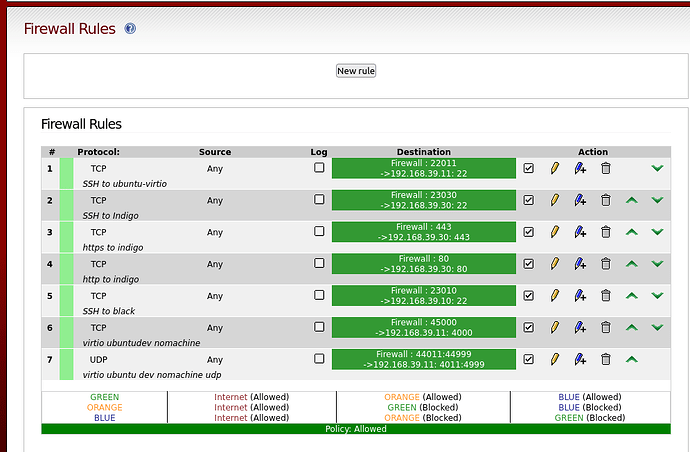
So I make a rule
Creating a rule essentially means opening a pinhole in the green network. The goal is to permit only necessary traffic, minimizing potential vulnerabilities.
But if I change the destination in the rule to be 192.168.39.11 then I can ping 39.11 but no longer 39.10
To allow communication with the entire network, set the destination to encompass the whole green network, rather than a specific IP. Or you can group all the IPs together, name the group and use that name in your rule.
So the “destination” address is somehow relevant to the rule. Not only does it choose which hosts respond, but it is filtering according to the request.
Indeed, rules can be defined based on various packet attributes including source, destination, and protocol, allowing for precise control over the network traffic.
Because I have a rule which sends port 443 traffic from the internet (red) to a host 192.168.39.15 but on the internet, the request is to the static IP address of my ISP, not 192.168.39.15
This is achieved through a mechanisms called Source Network Address Translation (SNAT) or IP masquerading, which allow multiple services on your LAN to operate behind a single public IP.
This does not make sense to me
I think you have a mental model that does not accurately map the design of the firewall, including the flexibility and broad capabilities of IPTables, the Linux firewall subsystem. It is designed to cater to a wide range of network configurations and requirements.
Fine. But then, why does the first rule not take any SSH request or any ping request and send it to the destination server?
Here, it is vital to differentiate between different protocols and ports. For instance, ping operates differently from TCP packets, and SSH utilizes different ports compared to HTTPS. Understanding these distinctions will enable you to set up rules that accurately reflect your network’s needs minimizing the surface of attach coming from Internet to your local network.