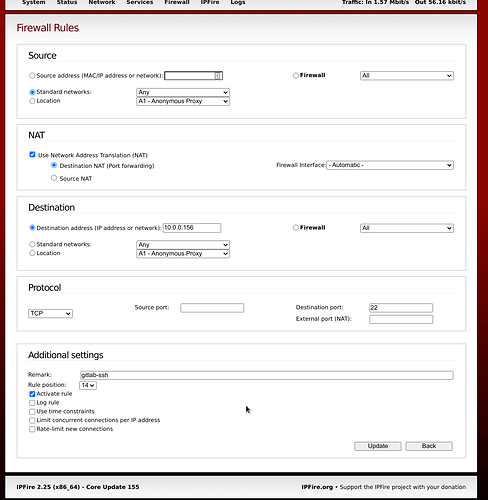
i’m trying to add a firewall rule on port 22 to reach one of my green network host.
the strange fact is i can use external port 222 to reach port 22 in my host, but i can’t trought external port 22
Can you please show the firewall rule you created.
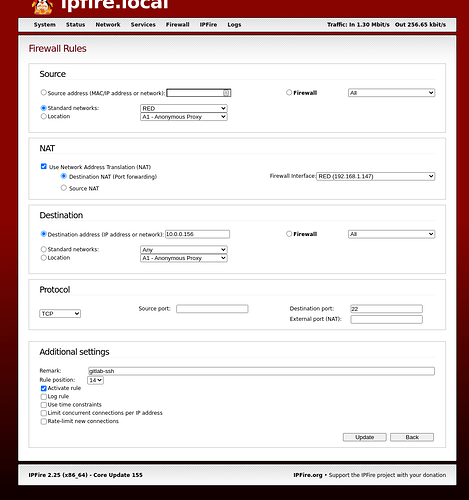
I have a vm IPFire testbed system whose red interface is on my main Green network. I have set up firewall rules on the vm IPFire to port forward port 22 to one of the vm machines on the testbed Green network.
The firewall rule I have is the same as yours with the exception that I have defined the source ip to come from a specific machine on my main Green network but that will not change anything for you.
So the firewall rule looks fine to me.
What error message are you getting from the ssh communication. You can increase the amount of debug info by adding -v or -vv or -vvv on the ssh command line that you are using. each extra v will give more detailed info. Start with -v and if there is not enough detail increase the number of v’s
You have
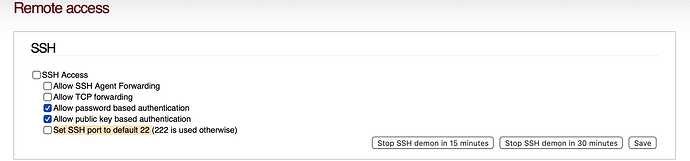
System → SSH Access → Remote access → SSH → Set SSH port to default 22
activated. Correct?
I believe he is looking at ssh’ng into a computer on his green network, not into IPFire based on his original post.
So that no misunderstandings arise. I have only stated that I think he has port 22 enabled.
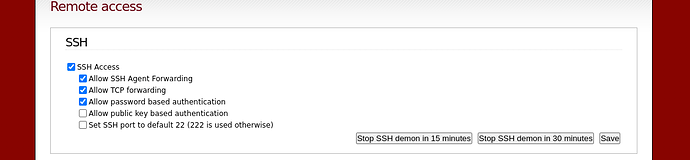
The statement should be tulpenknicker is right, uncheck the checkbox so it looks exactly like my screenshot (ignore my unset ssh)
According to my estimation you have now 3 possibilities.
- If you want to reach IPFire internal on port 22 but you want to leave your other server on 22 too, you have to set your Firewall rule, external port (nat) to something else
- You just deactivate the port 22 of IPFire, which as i said assume you have set it, with the “disadvantage” that from now on you reach IPFire on 222 but your server in green on 22
- Or you use as you already tried port 222 for your server in green
Thats already clear.
I see what you were getting at. Yes that would create a problem if set like that and trying to access an internal machine on the same port.
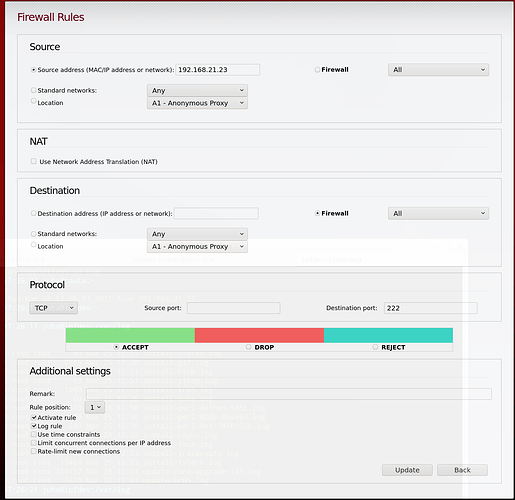
i’m trying to ssh an iternal server in green network.
as i described i can ssh into it using a custom port /mapping.
Not possible using regular port 22
ipfire himsef is on 222 port.
doing a
sudo nmap -v -sS myhost.com -Pn -p 22
it results
22/tcp filtered ssh.
i haven’t any rule that block it
What error message(s) do you get when you ssh with port 22.
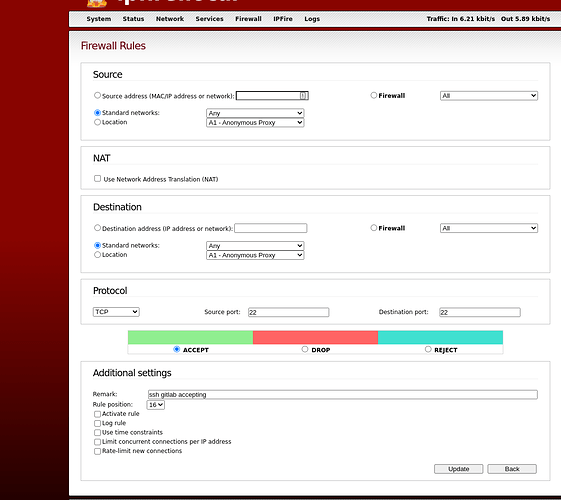
You have rule(s) that drop by default. You should have rule to allow port 22.
Probably should leave source port undefined. And check that “Activate rule” 
I have for my development IPFire:
(I have it listening the IPFire default port 222. Hmmm. reading back the first mesages on the thread… your case seems to be different…sorry
 )
)
Hi,
yes, this absolutely required, as the source port will be a random high port (> 1,023).
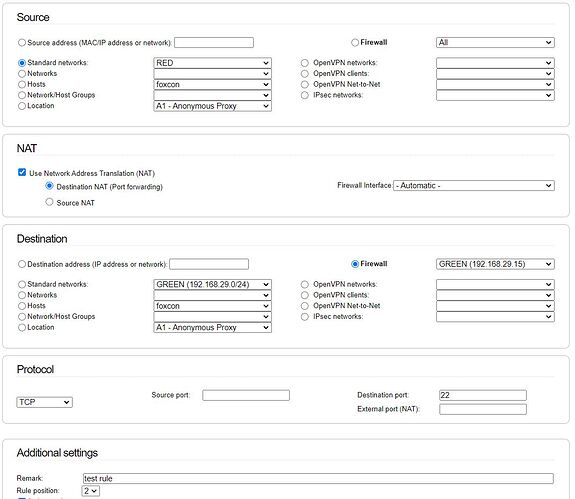
@otherego: Your first screenshot seems fine to me indeed. If I got your intention right, you want to reach the SSH server on a machine located in GREEN by connecting to port 22 on your IPFire’s RED IP.
Could you try editing that rule, and set “source” to “standard network | RED”, while setting “firewall interface” to “RED” as well?
Thanks, and best regards,
Peter Müller
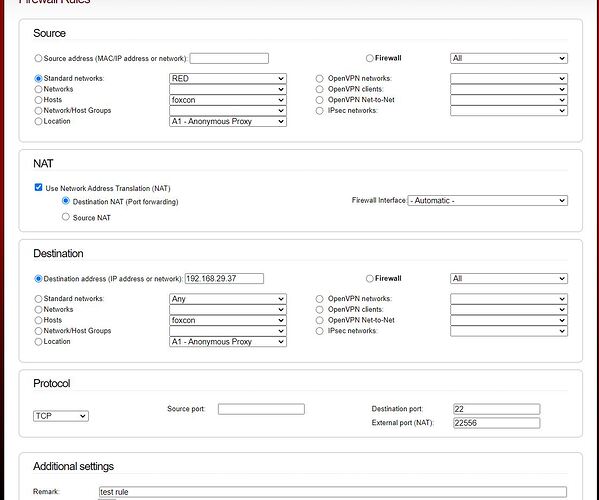
Hi otherego
I think I see what you are try to do, here is screen cap of a port mapping that works, maybe this simplifies what is happening.
External port (NAT): 22556 from the firewall then to your client machine at Destination port: 22
You will have to use the port command when connecting with ssh, -p 22556 at the end of command line.
You can add other machines on green by creating another rule with a higher port such as 22557 to the next machine at port 22.
The higher the incoming port the better, less port scans.
This should be temporary I think, I dont know your use case but using inbound VPN may be better.
i’m using that for gitlab server.
Using other external port different from port 22 is working well
just want to have it working on regular external port 22
to manage my ipfire i’m ssh-ing from vpn