Hi,
I am trying to create a firewall rule for ICMP Protocol to allow only some clients the use of “ping”.
But for some reason it does not work as expected and I do not know why.
I am using the following rules for the firewall:
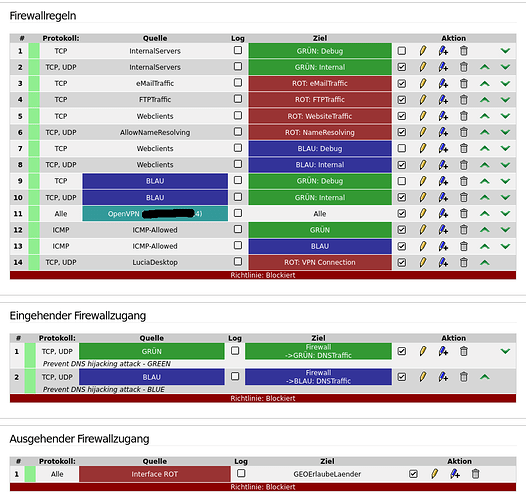
here the general overview of all rules:
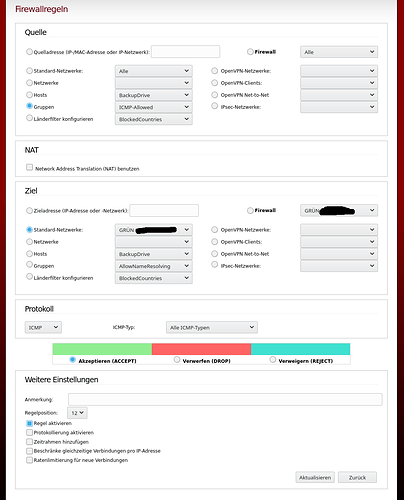
Here specially the rule for the ICMP packages:
Only two clients are within the group of ICMP-Allowed and the green network is a bridged network of 3 network cards. I used the IP Address for the rule instead of the mac address, which I normally use.
The first client (the firewall itself), can not execute a ping to a other client and I get the following message in the log file:
Jul 27 18:12:22 central kernel: DROP_OUTPUT IN= OUT=green0 SRC=A.B.C.1 DST=A.B.C.2 LEN=84 TOS=0x00 PREC=0x00 TTL=64 ID=26008 DF PROTO=ICMP TYPE=8 CODE=0 ID=4832 SEQ=8
But the client “A.B.C.2” can do a ping to “A.B.C.1” which should not go, because this client is not in the group of allowed computers for “ICMP”.
Where Is my problem, what Do I have to read to fix this problem.
Best regards
R.