Hey there,
I know, I know, this feature was requested many times before and the developers said that it is too complicated or at least too time consuming and not worth the effort to implement in IPFire 2x but will be part of IPFire 3x. But since IPFire 3x probably won’t be there for quite some time I wanted to repeat the request and (in my humblest opinion) it should not be so difficult.
Thing is, we have a lot of customers, who want to improve their network-setup / internet-security / remote-accessibility etc. and I always really want to recommend IPFire. I really like it because it offers everything you need (plus a lot more), is easy to manage (even for beginners) and has reasonable prices (compared to other distributors). All pretty good aspects to pitch it to customers, who would need a support-contract anyway, so no more reason to not make a contract / subscription with LWL (for support and/or development).
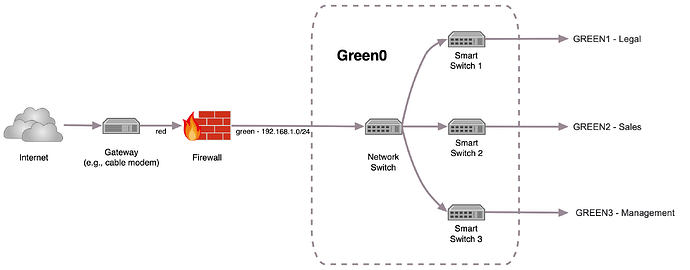
But I always stumble at the point where you need to put different departments (legal, sales, management, etc.) in different networks (mainly for security reasons but also for a better performance) and you do not want an additional device for this.
I checked a few config-files and scripts within IPFire (I’m no programmer, so please no shooting) and basically to “create” additional networks, you would only have to rename every “GREEN…” to “GREEN0…” (simplified) and create “GREEN1…”, “GREEN2…” and so on. Within those networks all the devices are able to see each other, so no need for additional configuration there, copy & paste from “GREEN0” should do it (maybe with the exception that only GREEN0 has access to the WUI, so it’s the “admin-net”). Between the networks, they need to be seperated from each other by default but all need access to red, so it’s exactly like it is with blue.
That should be it for the first step or do I miss something here?
The second and a bit more complicated part would be to assign multiple networks to one interface, because you need to implement trunking at whole. But the basis for this already is part of IPFire too, or isn’t it?
That’s it and IPFire is a serious and complete competitor for all the needs of 90% of the customers out there.
Would this really be that complicated?
Greetings and a happy new year to all of you! ![]()