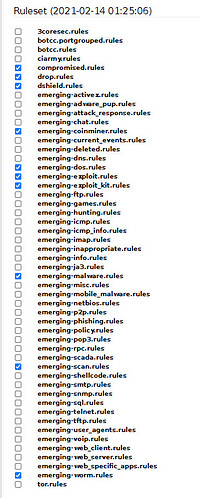
Hello everybody,
in my IPS I am using the Emerging Threats community rules. When checking the newly downloaded ruleset I realised that emerging-trojan.rules were missing.
Can I download these rules manually and copy them in the folder /var/lib/suricata ?
Should your answer be ‘yes’, is it guaranteed when downloading next time they are contained in the new ruleset?
Thank you for your assist in advance 
Cheers, Pierre
https://rules.emergingthreats.net/open/suricata-4.0/rules/
Looks like proofpoint has removed the trojan group or moved to the commercial pro ruleset.
Hi Arne,
it’s not correct, what you wrote. I have registered to the mailing list for Emerging updates.
As of 11/02/2021 I received these news:
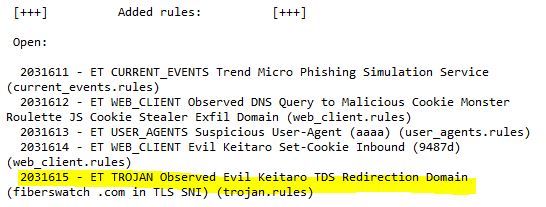
Here you’ll find the according archive entry:
https://lists.emergingthreats.net/pipermail/emerging-updates/2021-February/005022.html
I still don’t know, whether I can download the missing rules manually and paste them in the appropriate folder.
Regards,
Pierre
Am I the only one with this problem?
Hi @anon4944014
So I had a look at the code for getting the rules and found the url to get the community rules. I downloaded the tarball from that url and had a look in it and the emerging-trojan.rules rule is missing from it.
I then went to the emergingthreats.net website and found the rules and had a look at them. There are two directories of community rules one for suricata-4.0 and one for suricata-5.0
IPFire downloads the rules from suricata-5.0 This set no longer has the emerging-trojan.rules in it.
The suricata-4.0 set still has the emerging-trojan.rules in it.
You need to contact emergingthreats.net to find out why the rule was removed from the suricata-5.0 directory set and if it can be returned.
@bonnietwin … thanks for the follow-up.
Hi all,
today I sent a mail concerning this topic to proofpoint and emergingthreats as well. I wonder whether I shall get a reply. I keep you informed.
@Arne.F
Excuse me please, I have not resarched accurately enough. My statement in posting No.3 was not correct.
Cheers, Pierre
Hi,
today morning I received a reply from proofpoint. Here ist the most interesting part:
The “Trojan” category has been renamed to “Malware” in our Suricata 5 ruleset. For example, you will find SID 2031615 here, in our Suricata 5 ET OPEN set: https://rules.emergingthreatspro.com/open/suricata-5.0/rules/emerging-malware.rules
The daily notification is automatically generated from our Suricata 4 rule release, so it still has the ‘older’ category reference. I understand this is confusing and we’re working to make that change.
I think it is the solution for us.
Cheers, Pierre
Thanks @anon4944014.
I taked a look to malware section, and actually it’s huge.
UT1
Thanks @anon4944014!!!
BR