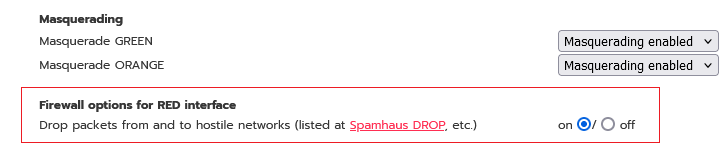
I’ve encountered a problem with access to the online shop ozon.ru (a Russian analogue of Amazon), which only appeared when the ‘Drop packets from and to hostile networks’ option was enabled.
I spent some time looking for the solution, and ended up finding this topic, and I tried running location update and re-exporting my location list with the ipset command suggested by @ross_codes:
/usr/bin/location export --directory=/var/lib/location/ipset --family=ipv4 --format=ipset
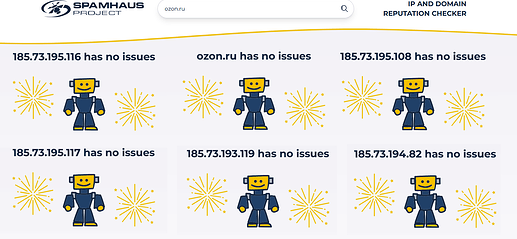
Unfortunately this didn`t help, so I searched website’s ip-addresses in updated location list and XD set, but there were neither addresses nor their subnets there. Also, the website appears to be not listed at Spamhaus or any other blocklist, so it’s shouldn’t be blocked by HOSTILE rule at all.
I’m kinda new here, so I`m not familiar with older core versions, but if I undersood it right - modern versions’ DROP_HOSTILE uses rules from HOSTILE_DROP_IN and HOSTILE_DROP_OUT iptabels, which don’t reference to any blocklists.
I fixed this issue using method from another topic, and whitelisted all the shop`s ip-addresses i could find in /etc/sysconfig/firewall.local, using code below (based on @casabenedetti’s code from the original post):
#!/bin/sh
# Used for private firewall rules
# See how we were called.
case "$1" in
start)
## add your 'start' rules here
## Ozon ip addresses
if ! iptables --check HOSTILE_DROP_OUT -p tcp -d 185.73.194.82 --dport 443 -j ACCEPT >/dev/null 2>&1 ; then
iptables --verbose --insert HOSTILE_DROP_OUT -p tcp -d 185.73.194.82 --dport 443 -j ACCEPT
iptables --verbose --insert HOSTILE_DROP_OUT -p tcp -d 185.73.194.82 --dport 443 -m limit --limit 10/sec --limit-burst 20 -j LOG --log-prefix "OZON_HOSTILE_BYPASS_OUT "
fi
if ! iptables --check HOSTILE_DROP_IN -p tcp -s 185.73.194.82 --sport 443 -j ACCEPT >/dev/null 2>&1 ; then
iptables --verbose --insert HOSTILE_DROP_IN -p tcp -s 185.73.194.82 --sport 443 -j ACCEPT
iptables --verbose --insert HOSTILE_DROP_IN -p tcp -s 185.73.194.82 --sport 443 -m limit --limit 10/sec --limit-burst 20 -j LOG --log-prefix "OZON_HOSTILE_BYPASS_OUT_IN "
fi
if ! iptables --check HOSTILE_DROP_OUT -p tcp -d 185.73.193.119 --dport 443 -j ACCEPT >/dev/null 2>&1 ; then
iptables --verbose --insert HOSTILE_DROP_OUT -p tcp -d 185.73.193.119 --dport 443 -j ACCEPT
iptables --verbose --insert HOSTILE_DROP_OUT -p tcp -d 185.73.193.119 --dport 443 -m limit --limit 10/sec --limit-burst 20 -j LOG --log-prefix "OZON_HOSTILE_BYPASS_OUT "
fi
if ! iptables --check HOSTILE_DROP_IN -p tcp -s 185.73.193.119 --sport 443 -j ACCEPT >/dev/null 2>&1 ; then
iptables --verbose --insert HOSTILE_DROP_IN -p tcp -s 185.73.193.119 --sport 443 -j ACCEPT
iptables --verbose --insert HOSTILE_DROP_IN -p tcp -s 185.73.193.119 --sport 443 -m limit --limit 10/sec --limit-burst 20 -j LOG --log-prefix "OZON_HOSTILE_BYPASS_OUT_IN "
fi
if ! iptables --check HOSTILE_DROP_OUT -p tcp -d 185.73.195.117 --dport 443 -j ACCEPT >/dev/null 2>&1 ; then
iptables --verbose --insert HOSTILE_DROP_OUT -p tcp -d 185.73.195.117 --dport 443 -j ACCEPT
iptables --verbose --insert HOSTILE_DROP_OUT -p tcp -d 185.73.195.117 --dport 443 -m limit --limit 10/sec --limit-burst 20 -j LOG --log-prefix "OZON_HOSTILE_BYPASS_OUT "
fi
if ! iptables --check HOSTILE_DROP_IN -p tcp -s 185.73.195.117 --sport 443 -j ACCEPT >/dev/null 2>&1 ; then
iptables --verbose --insert HOSTILE_DROP_IN -p tcp -s 185.73.195.117 --sport 443 -j ACCEPT
iptables --verbose --insert HOSTILE_DROP_IN -p tcp -s 185.73.195.117 --sport 443 -m limit --limit 10/sec --limit-burst 20 -j LOG --log-prefix "OZON_HOSTILE_BYPASS_OUT_IN "
fi
if ! iptables --check HOSTILE_DROP_OUT -p tcp -d 185.73.195.116 --dport 443 -j ACCEPT >/dev/null 2>&1 ; then
iptables --verbose --insert HOSTILE_DROP_OUT -p tcp -d 185.73.195.116 --dport 443 -j ACCEPT
iptables --verbose --insert HOSTILE_DROP_OUT -p tcp -d 185.73.195.116 --dport 443 -m limit --limit 10/sec --limit-burst 20 -j LOG --log-prefix "OZON_HOSTILE_BYPASS_OUT "
fi
if ! iptables --check HOSTILE_DROP_IN -p tcp -s 185.73.195.116 --sport 443 -j ACCEPT >/dev/null 2>&1 ; then
iptables --verbose --insert HOSTILE_DROP_IN -p tcp -s 185.73.195.116 --sport 443 -j ACCEPT
iptables --verbose --insert HOSTILE_DROP_IN -p tcp -s 185.73.195.116 --sport 443 -m limit --limit 10/sec --limit-burst 20 -j LOG --log-prefix "OZON_HOSTILE_BYPASS_OUT_IN "
fi
if ! iptables --check HOSTILE_DROP_OUT -p tcp -d 185.73.195.108 --dport 443 -j ACCEPT >/dev/null 2>&1 ; then
iptables --verbose --insert HOSTILE_DROP_OUT -p tcp -d 185.73.195.108 --dport 443 -j ACCEPT
iptables --verbose --insert HOSTILE_DROP_OUT -p tcp -d 185.73.195.108 --dport 443 -m limit --limit 10/sec --limit-burst 20 -j LOG --log-prefix "OZON_HOSTILE_BYPASS_OUT "
fi
if ! iptables --check HOSTILE_DROP_IN -p tcp -s 185.73.195.108 --sport 443 -j ACCEPT >/dev/null 2>&1 ; then
iptables --verbose --insert HOSTILE_DROP_IN -p tcp -s 185.73.195.108 --sport 443 -j ACCEPT
iptables --verbose --insert HOSTILE_DROP_IN -p tcp -s 185.73.195.108 --sport 443 -m limit --limit 10/sec --limit-burst 20 -j LOG --log-prefix "OZON_HOSTILE_BYPASS_OUT_IN "
fi
## Ozon ip addresses
;;
stop)
## add your 'stop' rules here
## Ozon ip addresses
if iptables --check HOSTILE_DROP_OUT -p tcp -d 185.73.194.82 --dport 443 -j ACCEPT >/dev/null 2>&1 ; then
iptables --verbose --delete HOSTILE_DROP_OUT -p tcp -d 185.73.194.82 --dport 443 -j ACCEPT
iptables --verbose --delete HOSTILE_DROP_OUT -p tcp -d 185.73.194.82 --dport 443 -m limit --limit 10/sec --limit-burst 20 -j LOG --log-prefix "OZON_HOSTILE_BYPASS_OUT "
fi
if iptables --check HOSTILE_DROP_IN -p tcp -s 185.73.194.82 --sport 443 -j ACCEPT >/dev/null 2>&1 ; then
iptables --verbose --delete HOSTILE_DROP_IN -p tcp -s 185.73.194.82 --sport 443 -j ACCEPT
iptables --verbose --delete HOSTILE_DROP_IN -p tcp -s 185.73.194.82 --sport 443 -m limit --limit 10/sec --limit-burst 20 -j LOG --log-prefix "OZON_HOSTILE_BYPASS_OUT_IN "
fi
if iptables --check HOSTILE_DROP_OUT -p tcp -d 185.73.193.119 --dport 443 -j ACCEPT >/dev/null 2>&1 ; then
iptables --verbose --delete HOSTILE_DROP_OUT -p tcp -d 185.73.193.119 --dport 443 -j ACCEPT
iptables --verbose --delete HOSTILE_DROP_OUT -p tcp -d 185.73.193.119 --dport 443 -m limit --limit 10/sec --limit-burst 20 -j LOG --log-prefix "OZON_HOSTILE_BYPASS_OUT "
fi
if iptables --check HOSTILE_DROP_IN -p tcp -s 185.73.193.119 --sport 443 -j ACCEPT >/dev/null 2>&1 ; then
iptables --verbose --delete HOSTILE_DROP_IN -p tcp -s 185.73.193.119 --sport 443 -j ACCEPT
iptables --verbose --delete HOSTILE_DROP_IN -p tcp -s 185.73.193.119 --sport 443 -m limit --limit 10/sec --limit-burst 20 -j LOG --log-prefix "OZON_HOSTILE_BYPASS_OUT_IN "
fi
if iptables --check HOSTILE_DROP_OUT -p tcp -d 185.73.195.117 --dport 443 -j ACCEPT >/dev/null 2>&1 ; then
iptables --verbose --delete HOSTILE_DROP_OUT -p tcp -d 185.73.195.117 --dport 443 -j ACCEPT
iptables --verbose --delete HOSTILE_DROP_OUT -p tcp -d 185.73.195.117 --dport 443 -m limit --limit 10/sec --limit-burst 20 -j LOG --log-prefix "OZON_HOSTILE_BYPASS_OUT "
fi
if iptables --check HOSTILE_DROP_IN -p tcp -s 185.73.195.117 --sport 443 -j ACCEPT >/dev/null 2>&1 ; then
iptables --verbose --delete HOSTILE_DROP_IN -p tcp -s 185.73.195.117 --sport 443 -j ACCEPT
iptables --verbose --delete HOSTILE_DROP_IN -p tcp -s 185.73.195.117 --sport 443 -m limit --limit 10/sec --limit-burst 20 -j LOG --log-prefix "OZON_HOSTILE_BYPASS_OUT_IN "
fi
if iptables --check HOSTILE_DROP_OUT -p tcp -d 185.73.195.116 --dport 443 -j ACCEPT >/dev/null 2>&1 ; then
iptables --verbose --delete HOSTILE_DROP_OUT -p tcp -d 185.73.195.116 --dport 443 -j ACCEPT
iptables --verbose --delete HOSTILE_DROP_OUT -p tcp -d 185.73.195.116 --dport 443 -m limit --limit 10/sec --limit-burst 20 -j LOG --log-prefix "OZON_HOSTILE_BYPASS_OUT "
fi
if iptables --check HOSTILE_DROP_IN -p tcp -s 185.73.195.116 --sport 443 -j ACCEPT >/dev/null 2>&1 ; then
iptables --verbose --delete HOSTILE_DROP_IN -p tcp -s 185.73.195.116 --sport 443 -j ACCEPT
iptables --verbose --delete HOSTILE_DROP_IN -p tcp -s 185.73.195.116 --sport 443 -m limit --limit 10/sec --limit-burst 20 -j LOG --log-prefix "OZON_HOSTILE_BYPASS_OUT_IN "
fi
if iptables --check HOSTILE_DROP_OUT -p tcp -d 185.73.195.108 --dport 443 -j ACCEPT >/dev/null 2>&1 ; then
iptables --verbose --delete HOSTILE_DROP_OUT -p tcp -d 185.73.195.108 --dport 443 -j ACCEPT
iptables --verbose --delete HOSTILE_DROP_OUT -p tcp -d 185.73.195.108 --dport 443 -m limit --limit 10/sec --limit-burst 20 -j LOG --log-prefix "OZON_HOSTILE_BYPASS_OUT "
fi
if iptables --check HOSTILE_DROP_IN -p tcp -s 185.73.195.108 --sport 443 -j ACCEPT >/dev/null 2>&1 ; then
iptables --verbose --delete HOSTILE_DROP_IN -p tcp -s 185.73.195.108 --sport 443 -j ACCEPT
iptables --verbose --delete HOSTILE_DROP_IN -p tcp -s 185.73.195.108 --sport 443 -m limit --limit 10/sec --limit-burst 20 -j LOG --log-prefix "OZON_HOSTILE_BYPASS_OUT_IN "
fi
## Ozon ip addresses
;;
reload)
$0 stop
$0 start
## add your 'reload' rules here
;;
*)
echo "Usage: $0 {start|stop|reload}"
;;
esac
And it helped! Connection to the website is actually working now.
But it’s obviously not a permanent fix, and it’s really feels more like a kluge, so I wonder if there is a better solution to my problem.
And if there is none - I hope this topic will help someone with similar problem.