Agree. But I don’t know how to do this. Any volunteers?!?
Add these lines to the config file. This is an example of the config for my allow zone for the DoH block (1st post):
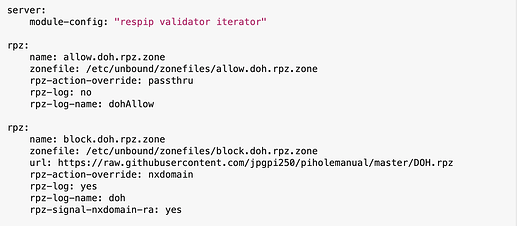
rpz:
name: allow.doh.rpz.zone
zonefile: /etc/unbound/zonefiles/allow.doh.rpz.zone
rpz-action-override: passthru
rpz-log: no
rpz-log-name: dohAllow
NOTE: This MUST go near the top of the config. Like this:
The"allows" go above the “blocks”, otherwise it won’t work.
Notice the rpz-action-override: passthru replaces the rpz-action-override: nxdomain.
Below is the DoH allow zone I use. It is placed in the /etc/unbound/zonefiles directory.
File: /etc/unbound/zonefiles/allow.doh.rpz.zone
$TTL 30 ;time (in seconds) that DNS responses are cached
@ SOA LOCALHOST. ipfire.org. (
1 ; serial number
1d ; refresh period
30m ; retry period
30d ; expire time
30 ; minimum TTL
)
NS localhost.
;
; domains and actions list
;
doh.dns.apple.com CNAME rpz-passthru.
doh.dns.apple.com.v.aaplimg.com CNAME rpz-passthru.
mask-api.icloud.com CNAME rpz-passthru.
mask-api.fe.apple-dns.net CNAME rpz-passthru.
mask.icloud.com CNAME rpz-passthru.
mask-h2.icloud.com CNAME rpz-passthru.
mask.apple-dns.net CNAME rpz-passthru.
The above is my example, Remove my items first and then place the items you want to allow in the list.
Notice the CNAME rpz-passthru. replaces the CNAME .
Make sure you increment the serial number otherwise the new zone file will not be captured into RPZ.
EDIT: Since we changed the config file make sure you do these commands:
Quick test
To check for issues in the config file, run the command on IPFire:
unbound-checkconf
Activate
Restart unbound to load config file:
/etc/init.d/unbound restart