Continuing the discussion from:
I read through many of the PDFs from jpgpi250 and I really like this one for DoH blocking:
https://github.com/jpgpi250/piholemanual/blob/master/doc/Unbound%20response%20policy%20zones.pdf
This looks like it will block DoH servers and (this is the best part) the DoH rpz list is updated most every day. I think RPZ (i.e., Unbound’s Response Policy Zones) will solve the issues found when running it as a blocklist.
So I gave it a try. Installing RPZ on an IPFire device is easy to set-up and activate and to use:
| Note | |
|---|---|
| • All of the info below came from jpgpi250’s PDF. And from experiments while using RPZ on IPFire. | |
| • For the most part I followed the steps in the PDF but some instructions changed to fit within IPFire. | |
| • Please experiment on your test IPFire system and not on a production system. | |
• Keep in mind this will block DoH servers you may want to access (e.g., doh.dns.apple.com or mozilla.cloudflare-dns.com). |
1. Set-up
A new directory is needed. Enter the command:
mkdir -v -p -m757 /etc/unbound/zonefiles
Now edit a new configuration file:
nano /etc/unbound/local.d/doh.conf
And add these lines:
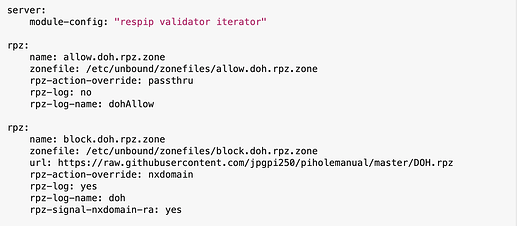
server:
module-config: "respip validator iterator"
rpz:
name: doh
zonefile: /etc/unbound/zonefiles/block.doh.rpz.zone
url: https://raw.githubusercontent.com/jpgpi250/piholemanual/master/DOH.rpz
rpz-action-override: nxdomain
rpz-log: yes
rpz-log-name: doh
Exit `nano` and save file.
Since the unbound program runs as nobody the following lines are needed for all zonefiles to avoid permission errors:
touch /etc/unbound/zonefiles/block.doh.rpz.zone
chown nobody:nobody /etc/unbound/zonefiles/block.doh.rpz.zone
chmod 644 /etc/unbound/zonefiles/block.doh.rpz.zone
Quick test
To check for issues in the config file, run the command on IPFire:
unbound-checkconf
2. Activate
Restart unbound to load config file:
/etc/init.d/unbound restart
3. Test
-
Pick a DNS server in the DOH.rpz list and run it on a computer connected to IPFire local GREEN or BLUE network.
dig 1111.cloudflare-dns.com | grep status -
Look for
status: NXDOMAIN(this is good!):$ dig 1111.cloudflare-dns.com | grep status ;; ->>HEADER<<- opcode: QUERY, status: NXDOMAIN, id: 10004 -
Look for this in the IPFire message log:
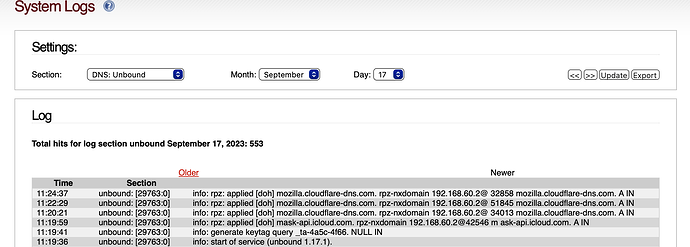
ipfire unbound: [12639:0] info: rpz: applied [doh] mozilla.cloudflare-dns.com. rpz-nxdomain 192.168.60.2@55807 mozilla.cloudflare-dns.com. A IN
Monitoring on IPFire
grep rpz /var/log/messages
# -or-
tail -f /var/log/messages | grep -i rpz
FAQs
- How often does RPZ update?
- the
DOH.rpzfile is updated per an SOA line.DOH.rpzupdates once a day per the SOA line and its refresh number.
- the
- Does anything need to
restartto get a new update?- Yes, for a change to the
doh.confconfig file (see above) - No, not for the RPZ zone files
- Yes, for a change to the
- What “bad” can happen from enable DoHblock?
- There will be LOTS of messages like this in the message log:
Sep 4 20:01:32 ipfire unbound: [12639:0] info: rpz: applied [doh] doh.dns.apple.com. rpz-nxdomain 192.168.60.2@40360 doh.dns.apple.com. HTTPS IN ... Sep 5 09:38:35 ipfire unbound: [12639:0] info: rpz: applied [doh] mozilla.cloudflare-dns.com. rpz-nxdomain 192.168.60.2@34446 mozilla.cloudflare-dns.com. A IN- On Apple iOS / Mac OS: I know this stops the Apple’s Private Relay and maybe the Apple’s Limit IP Address Tracking.
- On a Firefox browser: This stops Firefox’s DoH via Cloudflare.
- Android probably has something similar…
And I am still learning… And more changes coming…
EDIT: I made a few mistakes above concerning RPZ refreshing…
EDIT2: updated zonefile directory permissions:
mkdir -v -p -m757 /etc/unbound/zonefiles
updated /etc/unbound/local.d/doh.conf config file:
zonefile: /etc/unbound/zonefiles/block.doh.rpz.zone