Upon looking at the list of recommended DNS for servers located in the US, I don’t see any with a US location that also include a TLS hostname. And the only Anycast server with a TLS hostname other than Google or Cloudflare that also doesn’t collect IP information is Quad 9 (9.9.9.9). Are there any US users that can recommend international TLS servers to employ?
FWIW, these seem to work reasonably well for me:
Anycast 185.222.222.222 dns.sb
Anycast 185.184.222.222 dns.sb
Anycast 9.9.9.9 dns.quad9.net
Anycast 9.9.9.10 dns.quad9.net
Oddly enough the dns.sb responds more quickly for my US address than quad9.net
Thanks. I added that one, but dns.sb collects IP info. I was hoping to avoid it, but it’s the only other Anycast server other than Google or Cloudflare.
Also, does the second Quad 9 server support TLS (9.9.9.10)? It doesn’t have a TLS hostname next to it, so I thought it wasn’t supporting TLS.
Cloudflare’s TLS hostname is cloudflare-dns.com (1.1.1.1) on port 853
The second Quad 9 server (9.9.9.10) works fine – using same hostname: dns.quad9.net
Feel free to extend the list…
This one does not support DNSSEC. It should be listed at the bottom of the DNS sever listing page.
When I check the status – mousing over the OK – on the Domain Name System page, it shows as: DNSSEC Validating – this is RE: Quad 9 server (9.9.9.10)
It shows as Validating for me too. However, visiting the Cloud 9 website reveals this:
[Quad9 provides DNSSEC validation on our primary resolvers. 9.9.9.9, 149.112.112.112
In addition we validate DNSSEC on our EDNS enabled service. 9.9.9.11, 149.112.112.11
Unsecured IP: 9.9.9.10 Provides: No security blocklist, no DNSSEC, No EDNS Client-Subnet sent. Please use the unsecured secondary address of 149.112.112.10]
Sounds like the public DNS list needs to be updated to demote or remove 9.9.9.10 and add 9.9.9.11 in its place.
Quad 9’s 9.9.9.11 server is shown as an EDNS. I’m not too familiar with that version. It responds to DNSSEC but does EDNS have any other security issues with pseudo RR’s, etc. or incompatibility with IPFire?
Trying to use IPFire’s advice from the Blog and avoid Cloudflare.
“I would once again strongly consider to avoid sending your whole browser history to the big ones that are guaranteed to use it again [sic] you. Stay away from Google, Cloudflare, etc.”
DNS over TLS not working for me
Domain Name System
Status: Broken
Nameserver Country rDNS Remark Status Action
192.168.3.1 Reverse lookup failed ISP-assigned DNS server disabled
185.222.222.222 Reverse lookup failed OK
9.9.9.9 Reverse lookup failed OK
8.8.8.8 Reverse lookup failed OK
Hi all,
have included dns.sb in my list and it works here.
;; DEBUG: Querying for owner(www.isoc.org.), class(1), type(1), server(185.222.222.222), port(853), protocol(TCP)
;; DEBUG: TLS, imported 138 certificates from '/etc/ssl/certs/ca-bundle.crt'
;; DEBUG: TLS, received certificate hierarchy:
;; DEBUG: #1, C=EE,L=Tallinn,O=xTom OU,CN=dns.sb
;; DEBUG: SHA-256 PIN: /qCm+kZoAyouNBtgd1MPMS/cwpN4KLr60bAtajPLt0k=
;; DEBUG: #2, C=US,O=DigiCert Inc,CN=DigiCert SHA2 Secure Server CA
;; DEBUG: SHA-256 PIN: 5kJvNEMw0KjrCAu7eXY5HZdvyCS13BbA0VJG1RSP91w=
;; DEBUG: TLS, skipping certificate PIN check
;; DEBUG: TLS, The certificate is trusted.
;; TLS session (TLS1.3)-(ECDHE-SECP256R1)-(RSA-PSS-RSAE-SHA256)-(AES-256-GCM)
;; ->>HEADER<<- opcode: QUERY; status: NOERROR; id: 17566
;; Flags: qr rd ra ad; QUERY: 1; ANSWER: 2; AUTHORITY: 0; ADDITIONAL: 1
;; EDNS PSEUDOSECTION:
;; Version: 0; flags: do; UDP size: 4096 B; ext-rcode: NOERROR
;; QUESTION SECTION:
;; www.isoc.org. IN A
;; ANSWER SECTION:
www.isoc.org. 300 IN A 46.43.36.222
www.isoc.org. 300 IN RRSIG A 7 3 300 20200314085007 20200229085007 29027 isoc.org. Yy0+tOrkwb+BVBrvPdfR1foG+5+5BTZZfogapZEKPSBJh78Nz94WTdkVhbRaVfcaY7+4CbwyzWPfJfcnA5jy/TLhOhOHNNmX7oQ/RVEoORX063oKy4E2sEsULaaWuuL5iRkFcTIGRtHkSEfk60aDHTuwdVRa41HRRPoMeKYcBUQ=
;; Received 225 B
;; Time 2020-02-29 14:45:54 CET
;; From 185.222.222.222@853(TCP) in 463.4 ms
Exit status: 0
IP = 185.222.222.222
TLS Hostname = dns.sb
According to the topic, DoT located in the US seems to be really rare !
Best,
Erik
I saw that too after making a change, but it cleared up after a few seconds and a refresh. If that condition persists, you probably have other issues.
I settled on the two dns.sb servers specified above and quad 9’s DNS and EDNS at 9.9.9.9 and 9.9.9.11, respectively. All four are connecting with TLS, show OK, and DNSSEC validating. No resolve issues yet.
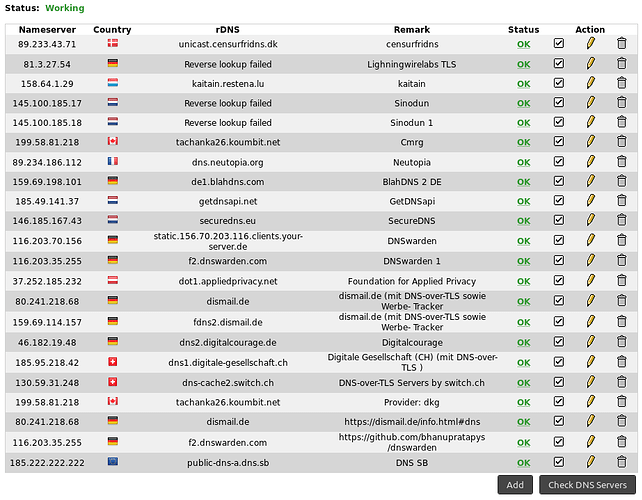
Thanks for the information. Am using currently the following except dns.sb since ~ 2 weeks, some of them much longer (~ one year) without problems.
with the following results:
=================================================================================================================================
Will check now your configured DNS-over-TLS servers from '/var/ipfire/dns/servers'
=================================================================================================================================
From Host: fdns2.dismail.de ---- With IP: 159.69.114.157 ---- Date: Sat 29 Feb 2020 03:37:49 PM CET
in 56.8 ms
The encryption is OK and works with: TLS1.2-ECDHE-X25519-RSA-SHA256-CHACHA20-POLY1305
The certificate is trusted and OK
The DNSSEC validation works and is OK
=================================================================================================================================
From Host: unicast.censurfridns.dk ---- With IP: 89.233.43.71 ---- Date: Sat 29 Feb 2020 03:37:50 PM CET
in 281.1 ms
The encryption is OK and works with: TLS1.2-ECDHE-SECP256R1-RSA-SHA256-AES-256-GCM
The certificate is trusted and OK
The DNSSEC validation works and is OK
=================================================================================================================================
From Host: fdns1.dismail.de ---- With IP: 80.241.218.68 ---- Date: Sat 29 Feb 2020 03:37:50 PM CET
in 272.8 ms
The encryption is OK and works with: TLS1.2-ECDHE-X25519-RSA-SHA256-CHACHA20-POLY1305
The certificate is trusted and OK
The DNSSEC validation works and is OK
=================================================================================================================================
From Host: getdnsapi.net ---- With IP: 185.49.141.37 ---- Date: Sat 29 Feb 2020 03:37:51 PM CET
in 244.2 ms
The encryption is OK and works with: TLS1.3-ECDHE-SECP256R1-RSA-PSS-RSAE-SHA256-AES-256-GCM
The certificate is trusted and OK
The DNSSEC validation works and is OK
=================================================================================================================================
From Host: dns.cmrg.net ---- With IP: 199.58.81.218 ---- Date: Sat 29 Feb 2020 03:37:52 PM CET
in 273.1 ms
The encryption is OK and works with: TLS1.3-ECDHE-SECP256R1-RSA-PSS-RSAE-SHA256-AES-256-GCM
The certificate is trusted and OK
The DNSSEC validation works and is OK
=================================================================================================================================
From Host: dns2.digitalcourage.de ---- With IP: 46.182.19.48 ---- Date: Sat 29 Feb 2020 03:37:52 PM CET
in 852.6 ms
The encryption is OK and works with: TLS1.2-ECDHE-SECP256R1-RSA-SHA256-AES-256-GCM
The certificate is trusted and OK
The DNSSEC validation works and is OK
=================================================================================================================================
From Host: dnsovertls3.sinodun.com ---- With IP: 145.100.185.18 ---- Date: Sat 29 Feb 2020 03:37:53 PM CET
in 329.4 ms
The encryption is OK and works with: TLS1.3-ECDHE-SECP256R1-RSA-PSS-RSAE-SHA256-AES-256-GCM
The certificate is trusted and OK
The DNSSEC validation works and is OK
=================================================================================================================================
From Host: dns.digitale-gesellschaft.ch ---- With IP: 185.95.218.42 ---- Date: Sat 29 Feb 2020 03:37:54 PM CET
in 168.4 ms
The encryption is OK and works with: TLS1.3-ECDHE-SECP256R1-RSA-PSS-RSAE-SHA256-AES-256-GCM
The certificate is trusted and OK
The DNSSEC validation works and is OK
=================================================================================================================================
From Host: dot-de.blahdns.com ---- With IP: 159.69.198.101 ---- Date: Sat 29 Feb 2020 03:37:54 PM CET
in 295.4 ms
The encryption is OK and works with: TLS1.3-ECDHE-SECP256R1-RSA-PSS-RSAE-SHA256-AES-128-GCM
The certificate is trusted and OK
The DNSSEC validation works and is OK
=================================================================================================================================
From Host: dot1.appliedprivacy.net ---- With IP: 37.252.185.232 ---- Date: Sat 29 Feb 2020 03:37:55 PM CET
in 167.8 ms
The encryption is OK and works with: TLS1.3-ECDHE-SECP256R1-RSA-PSS-RSAE-SHA256-AES-256-GCM
The certificate is trusted and OK
The DNSSEC validation works and is OK
=================================================================================================================================
From Host: dns.switch.ch ---- With IP: 130.59.31.248 ---- Date: Sat 29 Feb 2020 03:37:55 PM CET
in 160.0 ms
The encryption is OK and works with: TLS1.2-ECDHE-SECP256R1-RSA-SHA256-AES-256-GCM
The certificate is trusted and OK
The DNSSEC validation works and is OK
=================================================================================================================================
From Host: recursor01.dns.lightningwirelabs.com ---- With IP: 81.3.27.54 ---- Date: Sat 29 Feb 2020 03:37:56 PM CET
in 191.1 ms
The encryption is OK and works with: TLS1.3-ECDHE-SECP256R1-ECDSA-SECP384R1-SHA384-AES-256-GCM
The certificate is trusted and OK
The DNSSEC validation works and is OK
=================================================================================================================================
From Host: fdns1.dismail.de ---- With IP: 80.241.218.68 ---- Date: Sat 29 Feb 2020 03:37:56 PM CET
in 187.8 ms
The encryption is OK and works with: TLS1.2-ECDHE-X25519-RSA-SHA256-CHACHA20-POLY1305
The certificate is trusted and OK
The DNSSEC validation works and is OK
=================================================================================================================================
From Host: dns.sb ---- With IP: 185.222.222.222 ---- Date: Sat 29 Feb 2020 03:37:57 PM CET
in 334.8 ms
The encryption is OK and works with: TLS1.3-ECDHE-SECP256R1-RSA-PSS-RSAE-SHA256-AES-256-GCM
The certificate is trusted and OK
The DNSSEC validation works and is OK
=================================================================================================================================
From Host: dot1.dnswarden.com ---- With IP: 116.203.70.156 ---- Date: Sat 29 Feb 2020 03:37:57 PM CET
in 364.7 ms
The encryption is OK and works with: TLS1.3-ECDHE-SECP256R1-ECDSA-SECP256R1-SHA256-CHACHA20-POLY1305
The certificate is trusted and OK
The DNSSEC validation works and is OK
=================================================================================================================================
From Host: dot.securedns.eu ---- With IP: 146.185.167.43 ---- Date: Sat 29 Feb 2020 03:37:58 PM CET
in 347.9 ms
The encryption is OK and works with: TLS1.3-ECDHE-SECP256R1-RSA-PSS-RSAE-SHA256-AES-256-GCM
The certificate is trusted and OK
The DNSSEC validation works and is OK
=================================================================================================================================
From Host: dns.cmrg.net ---- With IP: 199.58.81.218 ---- Date: Sat 29 Feb 2020 03:37:59 PM CET
in 249.8 ms
The encryption is OK and works with: TLS1.3-ECDHE-SECP256R1-RSA-PSS-RSAE-SHA256-AES-256-GCM
The certificate is trusted and OK
The DNSSEC validation works and is OK
=================================================================================================================================
From Host: uncensored-dot.dnswarden.com ---- With IP: 116.203.35.255 ---- Date: Sat 29 Feb 2020 03:37:59 PM CET
in 75.1 ms
The encryption is OK and works with: TLS1.3-ECDHE-SECP256R1-ECDSA-SECP256R1-SHA256-CHACHA20-POLY1305
The certificate is trusted and OK
The DNSSEC validation works and is OK
=================================================================================================================================
From Host: dns.neutopia.org ---- With IP: 89.234.186.112 ---- Date: Sat 29 Feb 2020 03:38:00 PM CET
in 145.2 ms
The encryption is OK and works with: TLS1.3-ECDHE-SECP256R1-RSA-PSS-RSAE-SHA256-AES-256-GCM
The certificate is trusted and OK
The DNSSEC validation works and is OK
=================================================================================================================================
From Host: dot2.dnswarden.com ---- With IP: 116.203.35.255 ---- Date: Sat 29 Feb 2020 03:38:00 PM CET
in 74.9 ms
The encryption is OK and works with: TLS1.3-ECDHE-SECP256R1-ECDSA-SECP256R1-SHA256-CHACHA20-POLY1305
The certificate is trusted and OK
The DNSSEC validation works and is OK
=================================================================================================================================
From Host: kaitain.restena.lu ---- With IP: 158.64.1.29 ---- Date: Sat 29 Feb 2020 03:38:01 PM CET
in 41.6 ms
The encryption is OK and works with: TLS1.2-ECDHE-SECP256R1-RSA-SHA512-AES-256-GCM
The certificate is trusted and OK
The DNSSEC validation works and is OK
=================================================================================================================================
From Host: dnsovertls2.sinodun.com ---- With IP: 145.100.185.17 ---- Date: Sat 29 Feb 2020 03:38:01 PM CET
in 38.0 ms
The encryption is OK and works with: TLS1.2-ECDHE-SECP256R1-RSA-SHA256-AES-256-GCM
The certificate is trusted and OK
The DNSSEC validation works and is OK
=================================================================================================================================
All DNS-over-TLS servers from /var/ipfire/dns/servers has been tested.
mine
Domain Name System
Status: Broken
Nameserver Country rDNS Remark Action
192.168.3.1 Reverse lookup failed ISP-assigned DNS server
185.222.222.222 Reverse lookup failed dns.sb
8.8.8.8 Reverse lookup failed
9.9.9.9 Reverse lookup failed
8.8.4.4 Reverse lookup failed
81.3.27.54 Reverse lookup failed dns.lightningwirelabs
145.100.185.17 Reverse lookup failed Surfnet “NL”
145.100.185.18 Reverse lookup failed Surfnet “NL”
185.184.222.222 Reverse lookup failed dns.sb
9.9.9.11 Reverse lookup failed
89.233.43.71 Reverse lookup failed censurfridns.dk
DNS Configuration
Enable Safe Search
QNAME Minimisation
If i have a outgoing firewall active which blocks TCP 853, i get the same results then you.
Best,
Erik
9.9.9.10 should already be listed at the bottom of the page with the servers that are not supported.
And indeed we should advise do use 9.9.9.11 instead of 9.9.9.9 because we do speak EDNS.
Would you update this please?
I’m probably being blocked by the Verizon G1100 router.
I need to remove it from my network.
Data collection in America is very profitable for corporations.
Your data is not your own.