Hey Guys,
a few days ago i updated from 139 to 141 and then directly to 142.
From there i got massiv Problems with DNS, like many others. I tried several recommended soulutions, but nothings helped.
First: Booting the APU32c takes a long Time, unusually long, about 10min.
Unbound is up and running:
]# unbound-control status
version: 1.9.6
verbosity: 1
threads: 1
modules: 2 [ validator iterator ]
uptime: 42322 seconds
options: reuseport control
unbound (pid 28341) is running…
(serveral restarts did not solve my problems)
Name Resolution seems not to be working:
~]# /etc/init.d/unbound resolve de.wikipedia.com
;;
connection timed out;
no servers could be reached
Even when i try to reach e.g. de.wikipedia.org:
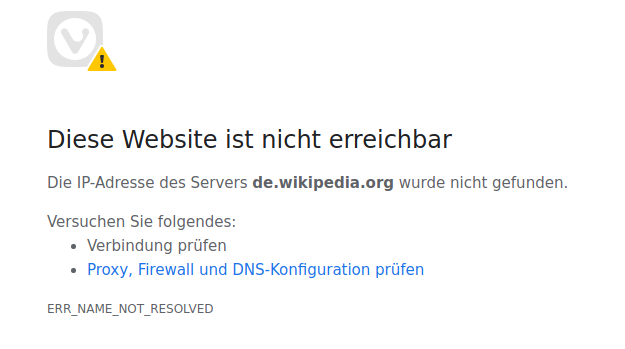
other URL’s are working fine, bit even IPFIRE.ORG cannor be reached. Pakfire is also not working…
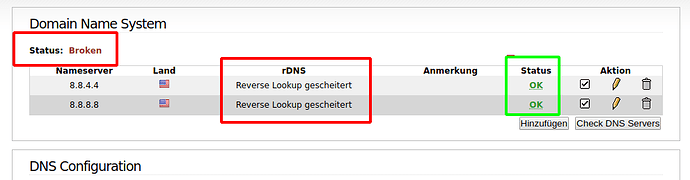
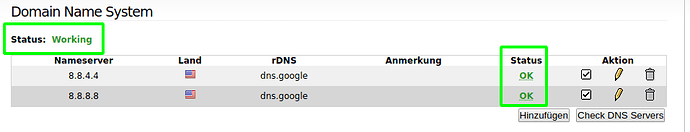
i use the Google DNS, which are officially recommended, but somthing seems to be broken:
Status for each DNS is “OK”, but the Status in the Header says “Broken”)
Oh, and the Log is full of Errors:
nfigured stub or forward servers failed, at zone .
Mar 24 08:03:52 knox unbound: [28341:0] info: validation failure <www.eff.org. A IN>: key for validation org. is marked as invalid
Mar 24 08:04:01 knox unbound: [28341:0] info: validation failure <ocsp.int-x3.letsencrypt.org. A IN>: key for validation org. is marked as invalid
Mar 24 08:04:06 knox unbound: [28341:0] error: SERVFAIL <org. DNSKEY IN>: all the configured stub or forward servers failed, at zone .
Mar 24 08:04:36 knox unbound: [28341:0] error: SERVFAIL <org. DNSKEY IN>: all the configured stub or forward servers failed, at zone .
Mar 24 08:04:36 knox unbound: [28341:0] info: validation failure <de.wikipedia.com. A IN>: No DNSKEY record for key org. while building chain of trust
Mar 24 08:05:01 knox unbound: [28341:0] info: validation failure <2.de.pool.ntp.org. A IN>: key for validation org. is marked as invalid
Mar 24 08:05:01 knox unbound: [28341:0] info: validation failure <2.de.pool.ntp.org. AAAA IN>: key for validation org. is marked as invalid
Mar 24 08:05:01 knox unbound: [28341:0] info: validation failure <3.de.pool.ntp.org. AAAA IN>: key for validation org. is marked as invalid
Mar 24 08:05:01 knox unbound: [28341:0] info: validation failure <3.de.pool.ntp.org. A IN>: key for validation org. is marked as invalid
Mar 24 08:05:06 knox unbound: [28341:0] error: SERVFAIL <org. DNSKEY IN>: all the configured stub or forward servers failed, at zone .
Mar 24 08:05:37 knox unbound: [28341:0] error: SERVFAIL <org. DNSKEY IN>: all the configured stub or forward servers failed, at zone .
Mar 24 08:06:05 knox unbound: [28341:0] error: SERVFAIL <ping.ipfire.org. A IN>: all the configured stub or forward servers failed, at zone .
Mar 24 08:06:07 knox unbound: [28341:0] error: SERVFAIL <org. DNSKEY IN>: all the configured stub or forward servers failed, at zone .
Mar 24 08:07:07 knox unbound: [28341:0] info: validation failure <de.wikipedia.org. A IN>: No DNSKEY record for key org. while building chain of trust
Mar 24 08:07:37 knox unbound: [28341:0] error: SERVFAIL <org. DNSKEY IN>: all the configured stub or forward servers failed, at zone .
Mar 24 08:08:07 knox unbound: [28341:0] error: SERVFAIL <org. DNSKEY IN>: all the configured stub or forward servers failed, at zone .
As i said, i tried many of the recommended solutions of this Forum, but nothing helped.
Would be happy if someone would help me. If you need more Information, just call, i try to bring it.
tyvm