I don’t understand the enthusiasm about WireGuard, as all of the client installers at Installation - WireGuard are outdated and not maintained anymore (since 2023). For example the MacOS one doesn’t work on M1 systems or newer, and you have to do an awkward Homebrew installation.
Maybe there hasn’t been much needing to be done.
I just checked the Android app, as I have it on my phone, and it has had 11 commits during the last 5 days related to upgrades of various related packages and the updating of the API, and it is the same person doing the commits that did them previously in 2023.
Hey Martin,
I hear you on not understanding the enthusiasm for WireGuard—it’s a lean VPN solution, and that simplicity can feel underwhelming. But that’s exactly why people love it: a small, secure codebase that gets the job done efficiently. The IPFire community has been eagerly awaiting WireGuard for years.
For your M1 silicon question, WireGuard’s macOS app has supported Apple Silicon since version 1.0.12 (December 2020). Check out isapplesiliconready.com for confirmation.
This is exactly it. The core of WireGuard is solid and mature at this point, with ongoing work keeping it compatible with various device APIs. Hope this helps clarify things!
Cheers,
A G
Well, the “official” WireGuard client App for Android is this one: https://play.google.com/store/apps/details?id=com.wireguard.android and dates back to 10/2023.
But indeed: Since 5 days there is activity again in wireguard-android - Android GUI for WireGuard! See the time gap leading back to 10/2023. So it seems that Jason A. Donenfeld is alive and kickin’. Great!
Hey Martin,
You’re spot-on—the official WireGuard Android app hasn’t had a Play Store update since October 2023. No need to worry, though; it’s not abandoned as WireGuard’s repo confirms
There’s also an open-source alternative, WG Tunnel, which has recent updates and extra features worth checking out.
Cheers,
A G
Great news ![]() @ag , may you know is this still actual
@ag , may you know is this still actual
103 # Add WireGuard settings
104 if (-e "/var/ipfire/wireguard/settings") {
105 my %wgsettings = ();
106 &General::readhash("/var/ipfire/wireguard/settings", \%wgsettings);
107 if (exists $wgsettings{'CLIENT_POOL'} && defined $wgsettings{'CLIENT_POOL'} && $wgsettings{'CLIENT_POOL'} ne '') {
108 $networks{$wgsettings{'CLIENT_POOL'}} = ${Header::colourwg};
109 }
110 }
111
112 # Add WireGuard peers
113 if (-e "/var/ipfire/wireguard/peers") {
114 my %wgpeers = ();
115 &General::readhasharray("/var/ipfire/wireguard/peers", \%wgpeers);
116 foreach my $key (keys %wgpeers) {
117 my $networks = $wgpeers{$key}[8];
118 my @networks = split(/\|/, $networks);
119 foreach my $network (@networks) {
120 $networks{$network} = ${Header::colourwg} if $network && &Network::check_subnet($network);
121 }
122 }
123 }
?
Apart from that, thanks for all your hard work by realizing such a new way to bring on a new candidate which should also be PQC ready https://eprint.iacr.org/2020/379.pdf ?
Best,
Erik
Hi Erik,
Thanks for pointing that out. WireGuard itself isn’t post-quantum secure right now, but if PQC is important, IPFire recently added support for PQC via IPsec, which is quite a big deal too IMHO.
Details here for those interested:
Of course, nothing stops WireGuard itself from adopting PQC down the road. The good news is I believe that we’ve already laid enough groundwork in IPFire that if an updated WireGuard (or a wg2) comes along with PQC built-in, we might be able to integrate it with less effort.
Cheers,
A G
Hopefully not. WireGuard is WireGuard. There is no way to change the protocol.
It is somewhat resistant against PQ attacks if there is a PSK being used which is the default in IPFire.
Wireguard is very good as a VPN and works great !
I mainly use it to connect to my LAN when I am not home and to do RDP via RDM (Remote Desktop Manager) on my 2016 Macbook,
Only issue is that it runs on a server I would be very glad if it was added directly to my IPFire FW !
Edit
Changed the content of the post to better convey the intent.
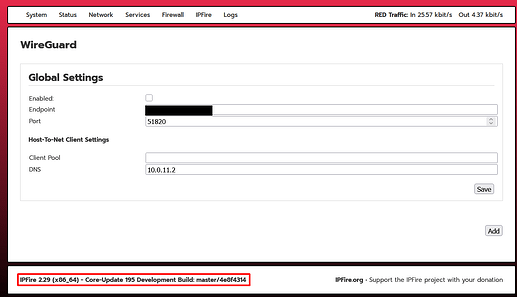
It looks like the hard work to implement Wireguard, has resulted in the test IPfire CU195 , the appearance of the configuration panel.
![]()
![]()
Regards
It didn’t just appear… It was hard work.
Thanks @ag for your insides, the additional questions which i had has also been resolved, have found it git.ipfire.org Git - ipfire-2.x.git/blob - html/cgi-bin/firewall.cgi ![]() … and THANKS @ms for all your hard work and additional infos, great work!
… and THANKS @ms for all your hard work and additional infos, great work!
Best,
Erik
I know that you have worked hard to implement Wireguard into IPFire.
I appreciate it and thank you for your efforts.
ps
In order to better convey the intentions I have changed the content of my post a bit .
Best Regards
Haha thanks. I am not offended. I just wanted to make clear that code doesn’t drop from the sky. It would have been nice to say that this was a community effort, but it wasn’t at all.
And it looks like with good results. ![]()
I set up a Net-to-Net connection and had access to remote computers.
![]()
Best Regards
Nice.
There are a few slightly hidden features there too.
If you hover your cursor over the entry name, “test” in your case, you’ll see the public key.
Also, if you hover over the flag, you’ll see the IP address, source port, and country code.
Thanks,
A G
Major thanks to the IPFire team for implementing this! I’ll be sending you guys a donation to express my gratitude! ![]()
I moved over to Wireguard a while back after I found OpenVPN to start hanging on me. I never did solve the issue either, as setting up Wireguard proved easier.
Up until now, I’ve been running a Debian Bookworm VM on my Firewall with Wireguard installed and little else with the firewall rules configured by hand. It’ll be great to be able to shut that VM down now.
Although I’ll probably wait until the actual release of Core 195 to upgrade my main firewall.
How cute are those little flags?
It would be great to have a couple of testers who are experienced with WireGuard who can report any problems that would be introduced by IPFire and which have not been there with other implementations.
I would also be curious how IPFire is doing in terms of operability with other vendors. So far we don’t have too much data, but we also have not been reported any problems at all. So I think the development team has done well to catch any bugs really early in the development process.