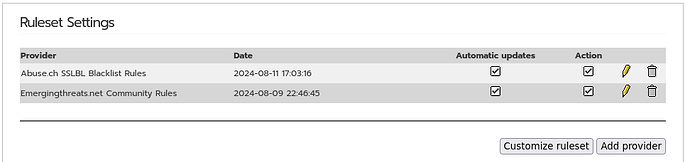
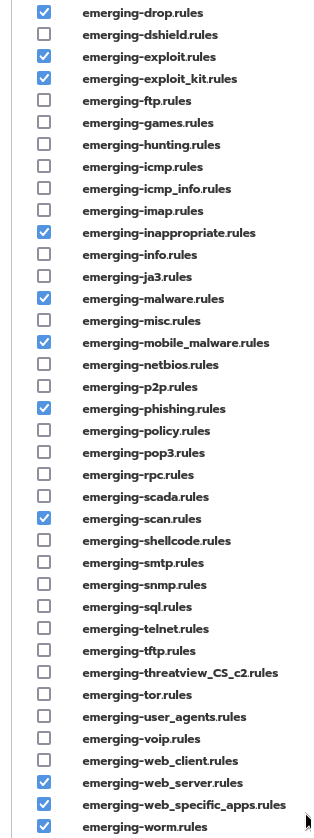
I know this has been discussed before, but I haven’t seen a resolution. When there are over 20k hits in less than 12 hours, how is one to monitor IPS logs in a meaningful way? I just exported today’s IPS logs (midnight to 11:40am). Out of over 22k logs, these are the most excessive:
Name: SURICATA STREAM ESTABLISHED invalid ack 6049 hits
Name: SURICATA STREAM ESTABLISHED packet out of window 9669 hits
Name: SURICATA STREAM Packet with invalid ack 6087 hits
Name: SURICATA STREAM Packet with invalid timestamp 326 hits
Those were the big offenders, there were several other rules that were hit a more reasonable number of times for a 12 hour period.
What’s crazy is, if I look at yesterday’s logs, in a 24 hour period there were “only” 3482 hits.
Yesterday’s big offenders:
Name: SURICATA STREAM ESTABLISHED invalid ack 1495 hits
Name: SURICATA STREAM ESTABLISHED packet out of window 234 hits
Name: SURICATA STREAM Packet with invalid ack 1505 hits
Name: SURICATA STREAM Packet with invalid timestamp 161 hits
How do you all handle monitoring your IPS logs?