Hello, I am currently evaluating IPFIRE as a solution for our project. The aim of the project is to delimit an area of our network and to control access to it using rules.
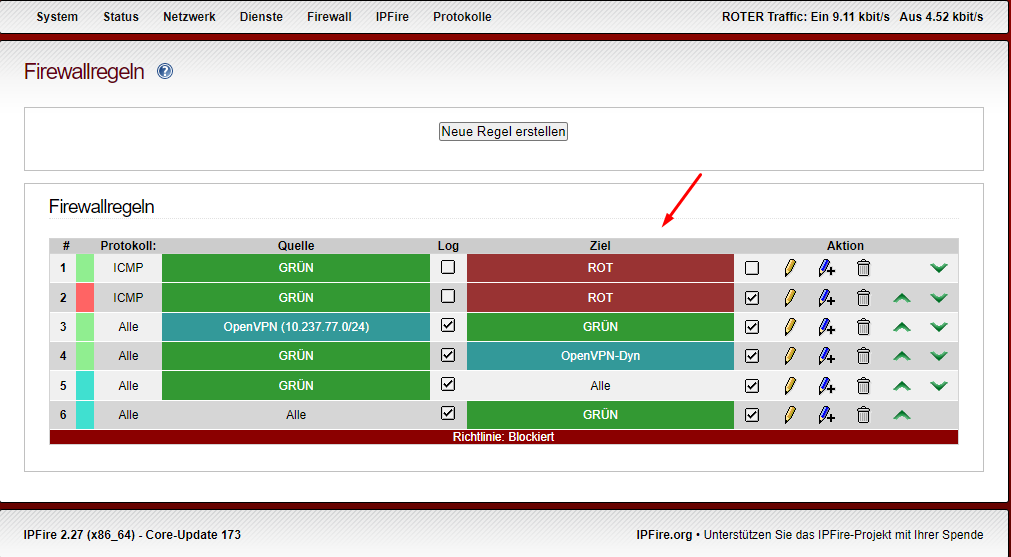
I have created rules in the firewall that block all traffic and created exceptions for incoming and outgoing traffic respectively. As a test, I’m trying to ping a target for which a disabled exception exists(red arrows). Ping does not arrive, ok. Then I enable the exception and ping again. Pink arrives, ok. Now I disable the exception and ping again. Pink still arrives, not OK. I can not find the error. Greetings Thomas
Hey Thomas,
I cannot say why the pinging does not work in the first place (with disabled exceptions) but PING or ICMP is not included in “Protokoll → Alle”, you have to choose “Protokoll → ICMP” for pings to be blocked.
Hope this will help you out! =)
Greetings
Alex
Hello Alex, thanks for your feedback.
I have now switched the protocol to ICMP (8) and also created a blocking rule with ICMP for testing. However, the behavior has not changed. If I ping with the exception disabled, it still comes through. Greetings Thomas
Hi @wolle
Welcome to the IPFire community.
I think you need to show us a picture of your network and where IPFire is positioned in it.
You said that you are looking at having IPFire inside your network to separate off a section and control it. So i would expect the IP address of your red interface to be a private ip range.
Your first two rules have a public IP address as source and destination for 1 & 2 respectively. They are shown in grey which means that IPFire has no direct access to them and can not route them as they are not part of the IPFire subnets.
Any firewall rules related to public internet addresses should be in the router/firewall that you have on your network perimeter to access the internet and not the internal IPFire.
I would expect that if the first two rules are related to total access from outside the area of your special network that IPFire is protecting that you should be using the private IP address that your red interface has and the rule would then show up as coloured red for the involved zone.
All the above is my guesswork, which is why I suggested it would be good to have a diagram of IPfire and the local IP addresses of each of the interfaces.
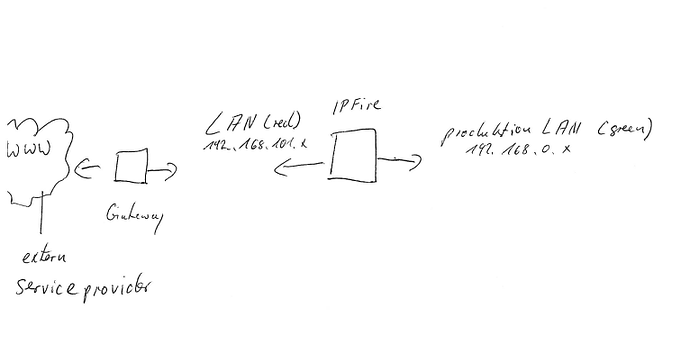
here is a small picture.
You are right, I wanted to test whether I can control access from an external service provider using IPFIRE. In our LAN (192.168.101.x) is the IPFIRE and separates the production network (192.168.0.x). The test IP 194.25.2.129 is an external DNS server just for testing.
How can I realize that I control connections with external service providers on and off.
Greetings Thomas
For explanation:
The production network contains production machines which are equipped with their own routers. These routers connect independently to the manufacturer support. We want the machines to be able to establish a connection only when necessary, and we want this to be activated.
Now I have changed the rules so that only the ping should be switched between green and red. That doesn’t work either. Again with the exception disabled, the ping arrives at an address on the red network. What am I doing wrong?
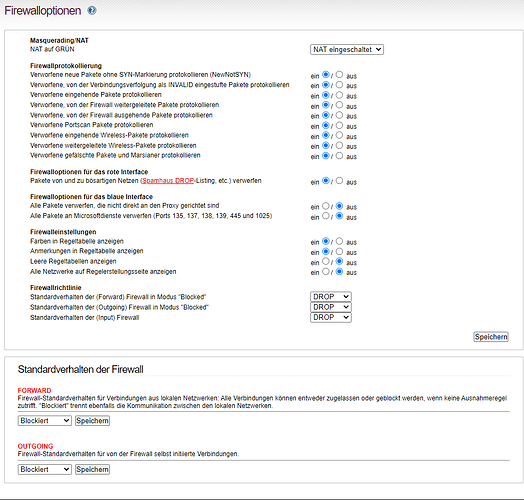
Okay, if what you are trying to do is to test if you have blocked the traffic going out from green to red then you will need to change the default setting for the IPFire Forward policy from Allowed to Blocked.
The default of Allowed that is set by IPFire means that any machine on Green can access the Internet without needing a special firewall rule.
That allow rule occurs before the rules in the firewall table, as far as I am aware.
https://wiki.ipfire.org/configuration/firewall/default-policy#forward
When you change that policy from Allowed to Blocked then all traffic from Green to any Zone will be dropped. Then you will need to create any required firewall rules to allow access going out.
This blog post will help with that.
https://blog.ipfire.org/post/firewall-configuration-recommendations-for-ipfire-users
ICMP is always allowed in the default policy even if you set the default to block. Only with an user rule it can blocked. But ICMP is not only for ping it also reports closed/unreachable messages and is used for mtu detection so you should not block it at all.
Then I need a new test scenario to test how and if I can control the traffic for individual production machines for external support. The aim is that no communication between the networks takes place without a temp. enabled exception.
Okay. Good. Just as a precautionary check, you did reboot after making that change?
Re the icmp feedback from @arne_f, he is much more knowledgeable than me on firewall aspects so it looks like a better test would be some other protocol such as 80/443. Then a browser on a machine on your green network will be able to confirm that you can control blocking or allowing browsing so that you can confirm the approach works.
OK, I’m currently testing with HTTP to the red network and to external addresses. However, what I noticed is that when I disable the exception, it takes 2-3 minutes for the change to take effect. As long as it is possible to make changes on the remote system.
The one that always gets me is it only works on new connections not established ones.