donbrill
10 May 2022 13:20
1
After update to 167, IPsec VPNs report Open. However, no traffic through tunnel (can not get to ipfire console on remote firewall, no ICMP traffic - ping - nor RDP sessions to hosts) unless I connect to remote firewall via OpenVPN and ping (home) firewall. After ping, IPsec tunnel functions normally. If remote firewall has not been updated (running Core Update 166), there is no issue.
Logs show no issue (unless I’m looking in the wrong place.)
30+ IPsec tunnels with similar config.
1 Like
silvio
10 May 2022 13:43
2
Hello Don,
can you see something in the IPSec log after the tunnel is created or something on the remote firewall?
Best
Silvio
steven
10 May 2022 14:36
3
I have the same issue over the weekend. After I deactivated the Spamhaus DROP-List and a reboot, the tunnel works again. A reboot with Drop-List enable, it doesnt work. I don’t know if it’s a coincidence or not. Because I don’t see why the drop list should prevent the tunnel.
silvio
10 May 2022 14:56
4
Eventually your remote IP is in a blocked network?
Silvio
steven
10 May 2022 15:59
5
No, they are not part of the drop-list. At least not when I looked. They are business VDSL connections with fixed IPs. I don’t think they’re going to be on the drop list. But who knows…
donbrill
10 May 2022 17:55
6
Currently running 33 IPsec VPNs that are all ipfire to ipfire, primarily on Dell and HP hardware. Mixture of static IP and dyndns. Tunnels all show as “Open” yet the only tunnels that have traffic are the tunnels to Core Update 166. Update 167 boxes may work, but most do not? Suspect that the route isn’t being added when the VPN opens, but that is a guess. Not sure what changes when ICMP traffic comes in from the remote and everything starts to traverse the tunnel.
donbrill
11 May 2022 01:50
7
Here’s the IPsec log from one of the VPN’s that was “Open” with no traffic until I pinged out about 21:00:
IPFire diagnostics
Section: ipsec
Date: May 10, 2022
21:04:22 charon: 11[NET] sending packet: from 96.83.209.249[4500] to 173.15.187.122[4500] (80 bytes)
21:04:22 charon: 11[ENC] generating INFORMATIONAL response 232 [ ]
21:04:22 charon: 11[ENC] parsed INFORMATIONAL request 232 [ ]
21:04:22 charon: 11[NET] received packet: from 173.15.187.122[4500] to 96.83.209.249[4500] (80 bytes)
21:03:52 charon: 13[NET] sending packet: from 96.83.209.249[4500] to 173.15.187.122[4500] (80 bytes)
21:03:52 charon: 13[ENC] generating INFORMATIONAL response 231 [ ]
21:03:52 charon: 13[ENC] parsed INFORMATIONAL request 231 [ ]
21:03:52 charon: 13[NET] received packet: from 173.15.187.122[4500] to 96.83.209.249[4500] (80 bytes)
21:03:22 charon: 01[NET] sending packet: from 96.83.209.249[4500] to 173.15.187.122[4500] (80 bytes)
21:03:22 charon: 01[ENC] generating INFORMATIONAL response 230 [ ]
21:03:22 charon: 01[ENC] parsed INFORMATIONAL request 230 [ ]
21:03:22 charon: 01[NET] received packet: from 173.15.187.122[4500] to 96.83.209.249[4500] (80 bytes)
21:02:52 charon: 13[IKE] CHILD_SA closed
21:02:52 charon: 13[IKE] received DELETE for ESP CHILD_SA with SPI ca9d31d0
21:02:52 charon: 13[ENC] parsed INFORMATIONAL response 148 [ D ]
21:02:52 charon: 13[NET] received packet: from 173.15.187.122[4500] to 96.83.209.249[4500] (80 bytes)
21:02:52 charon: 06[NET] sending packet: from 96.83.209.249[4500] to 173.15.187.122[4500] (80 bytes)
21:02:52 charon: 06[ENC] generating INFORMATIONAL request 148 [ D ]
21:02:52 charon: 06[IKE] sending DELETE for ESP CHILD_SA with SPI c22ae6e6
21:02:52 charon: 06[IKE] closing CHILD_SA TechSupport{318} with SPIs c22ae6e6_i (0 bytes) ca9d31d0_o (0 bytes) and TS 192.168.105.0/24 === 192.168.10.0/24
21:02:52 charon: 06[IKE] closing CHILD_SA TechSupport{318} with SPIs c22ae6e6_i (0 bytes) ca9d31d0_o (0 bytes) and TS 192.168.105.0/24 === 192.168.10.0/24
21:02:52 charon: 06[IKE] outbound CHILD_SA TechSupport{320} established with SPIs c888e641_i c751ca4a_o and TS 192.168.105.0/24 === 192.168.10.0/24
21:02:52 charon: 06[IKE] outbound CHILD_SA TechSupport{320} established with SPIs c888e641_i c751ca4a_o and TS 192.168.105.0/24 === 192.168.10.0/24
21:02:52 charon: 06[IKE] inbound CHILD_SA TechSupport{320} established with SPIs c888e641_i c751ca4a_o and TS 192.168.105.0/24 === 192.168.10.0/24
21:02:52 charon: 06[IKE] inbound CHILD_SA TechSupport{320} established with SPIs c888e641_i c751ca4a_o and TS 192.168.105.0/24 === 192.168.10.0/24
21:02:52 charon: 06[CFG] selected proposal: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_4096/NO_EXT_SEQ
21:02:51 charon: 06[ENC] parsed CREATE_CHILD_SA response 147 [ N(IPCOMP_SUP) SA No KE TSi TSr ]
21:02:51 charon: 06[NET] received packet: from 173.15.187.122[4500] to 96.83.209.249[4500] (736 bytes)
21:02:51 charon: 14[NET] sending packet: from 96.83.209.249[4500] to 173.15.187.122[4500] (944 bytes)
21:02:51 charon: 14[ENC] generating CREATE_CHILD_SA request 147 [ N(REKEY_SA) N(IPCOMP_SUP) SA No KE TSi TSr ]
21:02:51 charon: 14[IKE] establishing CHILD_SA TechSupport{320} reqid 1
21:02:51 charon: 14[IKE] establishing CHILD_SA TechSupport{320} reqid 1
21:02:51 charon: 14[KNL] creating rekey job for CHILD_SA ESP/0xc22ae6e6/96.83.209.249
21:02:29 charon: 07[NET] sending packet: from 96.83.209.249[4500] to 173.15.187.122[4500] (80 bytes)
21:02:29 charon: 07[ENC] generating INFORMATIONAL response 229 [ ]
21:02:29 charon: 07[ENC] parsed INFORMATIONAL request 229 [ ]
21:02:29 charon: 07[NET] received packet: from 173.15.187.122[4500] to 96.83.209.249[4500] (80 bytes)
21:01:59 charon: 07[NET] sending packet: from 96.83.209.249[4500] to 173.15.187.122[4500] (80 bytes)
21:01:59 charon: 07[ENC] generating INFORMATIONAL response 228 [ ]
21:01:59 charon: 07[ENC] parsed INFORMATIONAL request 228 [ ]
21:01:59 charon: 07[NET] received packet: from 173.15.187.122[4500] to 96.83.209.249[4500] (80 bytes)
21:01:29 charon: 01[NET] sending packet: from 96.83.209.249[4500] to 173.15.187.122[4500] (80 bytes)
21:01:29 charon: 01[ENC] generating INFORMATIONAL response 227 [ ]
21:01:29 charon: 01[ENC] parsed INFORMATIONAL request 227 [ ]
21:01:29 charon: 01[NET] received packet: from 173.15.187.122[4500] to 96.83.209.249[4500] (80 bytes)
21:00:59 charon: 10[NET] sending packet: from 96.83.209.249[4500] to 173.15.187.122[4500] (80 bytes)
21:00:59 charon: 10[ENC] generating INFORMATIONAL response 226 [ ]
21:00:59 charon: 10[ENC] parsed INFORMATIONAL request 226 [ ]
21:00:59 charon: 10[NET] received packet: from 173.15.187.122[4500] to 96.83.209.249[4500] (80 bytes)
21:00:29 charon: 11[NET] sending packet: from 96.83.209.249[4500] to 173.15.187.122[4500] (80 bytes)
21:00:29 charon: 11[ENC] generating INFORMATIONAL response 225 [ ]
21:00:29 charon: 11[ENC] parsed INFORMATIONAL request 225 [ ]
21:00:29 charon: 11[NET] received packet: from 173.15.187.122[4500] to 96.83.209.249[4500] (80 bytes)
20:59:59 charon: 07[NET] sending packet: from 96.83.209.249[4500] to 173.15.187.122[4500] (80 bytes)
20:59:59 charon: 07[ENC] generating INFORMATIONAL response 224 [ ]
20:59:59 charon: 07[ENC] parsed INFORMATIONAL request 224 [ ]
20:59:59 charon: 07[NET] received packet: from 173.15.187.122[4500] to 96.83.209.249[4500] (80 bytes)
20:59:29 charon: 06[NET] sending packet: from 96.83.209.249[4500] to 173.15.187.122[4500] (80 bytes)
20:59:29 charon: 06[ENC] generating INFORMATIONAL response 223 [ ]
20:59:29 charon: 06[ENC] parsed INFORMATIONAL request 223 [ ]
20:59:29 charon: 06[NET] received packet: from 173.15.187.122[4500] to 96.83.209.249[4500] (80 bytes)
20:58:59 charon: 14[NET] sending packet: from 96.83.209.249[4500] to 173.15.187.122[4500] (80 bytes)
20:58:59 charon: 14[ENC] generating INFORMATIONAL response 222 [ ]
20:58:59 charon: 14[ENC] parsed INFORMATIONAL request 222 [ ]
20:58:59 charon: 14[NET] received packet: from 173.15.187.122[4500] to 96.83.209.249[4500] (80 bytes)
20:58:29 charon: 12[NET] sending packet: from 96.83.209.249[4500] to 173.15.187.122[4500] (80 bytes)
20:58:29 charon: 12[ENC] generating INFORMATIONAL response 221 [ ]
20:58:29 charon: 12[ENC] parsed INFORMATIONAL request 221 [ ]
20:58:29 charon: 12[NET] received packet: from 173.15.187.122[4500] to 96.83.209.249[4500] (80 bytes)
20:57:59 charon: 09[NET] sending packet: from 96.83.209.249[4500] to 173.15.187.122[4500] (80 bytes)
20:57:59 charon: 09[ENC] generating INFORMATIONAL response 220 [ ]
20:57:59 charon: 09[ENC] parsed INFORMATIONAL request 220 [ ]
20:57:59 charon: 09[NET] received packet: from 173.15.187.122[4500] to 96.83.209.249[4500] (80 bytes)
20:57:29 charon: 08[NET] sending packet: from 96.83.209.249[4500] to 173.15.187.122[4500] (80 bytes)
20:57:29 charon: 08[ENC] generating INFORMATIONAL response 219 [ ]
20:57:29 charon: 08[ENC] parsed INFORMATIONAL request 219 [ ]
20:57:29 charon: 08[NET] received packet: from 173.15.187.122[4500] to 96.83.209.249[4500] (80 bytes)
20:56:59 charon: 09[IKE] CHILD_SA closed
20:56:59 charon: 09[IKE] received DELETE for ESP CHILD_SA with SPI c401a08a
20:56:59 charon: 09[ENC] parsed INFORMATIONAL response 146 [ D ]
20:56:59 charon: 09[NET] received packet: from 173.15.187.122[4500] to 96.83.209.249[4500] (80 bytes)
20:56:59 charon: 14[NET] sending packet: from 96.83.209.249[4500] to 173.15.187.122[4500] (80 bytes)
20:56:59 charon: 14[ENC] generating INFORMATIONAL request 146 [ D ]
20:56:59 charon: 14[IKE] sending DELETE for ESP CHILD_SA with SPI c77011f7
20:56:59 charon: 14[IKE] closing CHILD_SA TechSupport{317} with SPIs c77011f7_i (0 bytes) c401a08a_o (0 bytes) and TS 192.168.105.0/24 === 192.168.10.0/24
20:56:59 charon: 14[IKE] closing CHILD_SA TechSupport{317} with SPIs c77011f7_i (0 bytes) c401a08a_o (0 bytes) and TS 192.168.105.0/24 === 192.168.10.0/24
20:56:59 charon: 14[IKE] outbound CHILD_SA TechSupport{319} established with SPIs cc95110c_i c4492ce0_o and TS 192.168.105.0/24 === 192.168.10.0/24
20:56:59 charon: 14[IKE] outbound CHILD_SA TechSupport{319} established with SPIs cc95110c_i c4492ce0_o and TS 192.168.105.0/24 === 192.168.10.0/24
20:56:59 charon: 14[IKE] inbound CHILD_SA TechSupport{319} established with SPIs cc95110c_i c4492ce0_o and TS 192.168.105.0/24 === 192.168.10.0/24
20:56:59 charon: 14[IKE] inbound CHILD_SA TechSupport{319} established with SPIs cc95110c_i c4492ce0_o and TS 192.168.105.0/24 === 192.168.10.0/24
20:56:59 charon: 14[CFG] selected proposal: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_4096/NO_EXT_SEQ
20:56:59 charon: 14[ENC] parsed CREATE_CHILD_SA response 145 [ N(IPCOMP_SUP) SA No KE TSi TSr ]
20:56:59 charon: 14[NET] received packet: from 173.15.187.122[4500] to 96.83.209.249[4500] (736 bytes)
20:56:59 charon: 11[NET] sending packet: from 96.83.209.249[4500] to 173.15.187.122[4500] (944 bytes)
20:56:59 charon: 11[ENC] generating CREATE_CHILD_SA request 145 [ N(REKEY_SA) N(IPCOMP_SUP) SA No KE TSi TSr ]
20:56:59 charon: 11[IKE] establishing CHILD_SA TechSupport{319} reqid 1
20:56:59 charon: 11[IKE] establishing CHILD_SA TechSupport{319} reqid 1
20:56:59 charon: 11[KNL] creating rekey job for CHILD_SA ESP/0xc77011f7/96.83.209.249
20:56:46 charon: 16[NET] sending packet: from 96.83.209.249[4500] to 173.15.187.122[4500] (80 bytes)
20:56:46 charon: 16[ENC] generating INFORMATIONAL response 218 [ ]
20:56:46 charon: 16[ENC] parsed INFORMATIONAL request 218 [ ]
20:56:46 charon: 16[NET] received packet: from 173.15.187.122[4500] to 96.83.209.249[4500] (80 bytes)
20:56:16 charon: 11[NET] sending packet: from 96.83.209.249[4500] to 173.15.187.122[4500] (80 bytes)
20:56:16 charon: 11[ENC] generating INFORMATIONAL response 217 [ ]
20:56:16 charon: 11[ENC] parsed INFORMATIONAL request 217 [ ]
20:56:16 charon: 11[NET] received packet: from 173.15.187.122[4500] to 96.83.209.249[4500] (80 bytes)
20:55:46 charon: 01[NET] sending packet: from 96.83.209.249[4500] to 173.15.187.122[4500] (80 bytes)
20:55:46 charon: 01[ENC] generating INFORMATIONAL response 216 [ ]
20:55:46 charon: 01[ENC] parsed INFORMATIONAL request 216 [ ]
20:55:46 charon: 01[NET] received packet: from 173.15.187.122[4500] to 96.83.209.249[4500] (80 bytes)
20:55:16 charon: 06[NET] sending packet: from 96.83.209.249[4500] to 173.15.187.122[4500] (80 bytes)
20:55:16 charon: 06[ENC] generating INFORMATIONAL response 215 [ ]
20:55:16 charon: 06[ENC] parsed INFORMATIONAL request 215 [ ]
20:55:16 charon: 06[NET] received packet: from 173.15.187.122[4500] to 96.83.209.249[4500] (80 bytes)
20:54:46 charon: 05[NET] sending packet: from 96.83.209.249[4500] to 173.15.187.122[4500] (80 bytes)
20:54:46 charon: 05[ENC] generating INFORMATIONAL response 214 [ ]
20:54:46 charon: 05[ENC] parsed INFORMATIONAL request 214 [ ]
20:54:46 charon: 05[NET] received packet: from 173.15.187.122[4500] to 96.83.209.249[4500] (80 bytes)
20:54:16 charon: 11[NET] sending packet: from 96.83.209.249[4500] to 173.15.187.122[4500] (80 bytes)
20:54:16 charon: 11[ENC] generating INFORMATIONAL response 213 [ ]
20:54:16 charon: 11[ENC] parsed INFORMATIONAL request 213 [ ]
20:54:16 charon: 11[NET] received packet: from 173.15.187.122[4500] to 96.83.209.249[4500] (80 bytes)
20:53:46 charon: 11[NET] sending packet: from 96.83.209.249[4500] to 173.15.187.122[4500] (80 bytes)
20:53:46 charon: 11[ENC] generating INFORMATIONAL response 212 [ ]
20:53:46 charon: 11[ENC] parsed INFORMATIONAL request 212 [ ]
20:53:46 charon: 11[NET] received packet: from 173.15.187.122[4500] to 96.83.209.249[4500] (80 bytes)
20:53:16 charon: 11[NET] sending packet: from 96.83.209.249[4500] to 173.15.187.122[4500] (80 bytes)
20:53:16 charon: 11[ENC] generating INFORMATIONAL response 211 [ ]
20:53:16 charon: 11[ENC] parsed INFORMATIONAL request 211 [ ]
20:53:16 charon: 11[NET] received packet: from 173.15.187.122[4500] to 96.83.209.249[4500] (80 bytes)
20:52:46 charon: 05[NET] sending packet: from 96.83.209.249[4500] to 173.15.187.122[4500] (80 bytes)
20:52:46 charon: 05[ENC] generating INFORMATIONAL response 210 [ ]
20:52:46 charon: 05[ENC] parsed INFORMATIONAL request 210 [ ]
20:52:46 charon: 05[NET] received packet: from 173.15.187.122[4500] to 96.83.209.249[4500] (80 bytes)
20:52:16 charon: 11[NET] sending packet: from 96.83.209.249[4500] to 173.15.187.122[4500] (80 bytes)
20:52:16 charon: 11[ENC] generating INFORMATIONAL response 209 [ ]
20:52:16 charon: 11[ENC] parsed INFORMATIONAL request 209 [ ]
20:52:16 charon: 11[NET] received packet: from 173.15.187.122[4500] to 96.83.209.249[4500] (80 bytes)
20:51:46 charon: 06[NET] sending packet: from 96.83.209.249[4500] to 173.15.187.122[4500] (80 bytes)
20:51:46 charon: 06[ENC] generating INFORMATIONAL response 208 [ ]
20:51:46 charon: 06[ENC] parsed INFORMATIONAL request 208 [ ]
20:51:46 charon: 06[NET] received packet: from 173.15.187.122[4500] to 96.83.209.249[4500] (80 bytes)
20:51:16 charon: 13[NET] sending packet: from 96.83.209.249[4500] to 173.15.187.122[4500] (80 bytes)
20:51:16 charon: 13[ENC] generating INFORMATIONAL response 207 [ ]
20:51:16 charon: 13[ENC] parsed INFORMATIONAL request 207 [ ]
20:51:16 charon: 13[NET] received packet: from 173.15.187.122[4500] to 96.83.209.249[4500] (80 bytes)
20:50:46 charon: 07[NET] sending packet: from 96.83.209.249[4500] to 173.15.187.122[4500] (80 bytes)
20:50:46 charon: 07[ENC] generating INFORMATIONAL response 206 [ ]
20:50:46 charon: 07[ENC] parsed INFORMATIONAL request 206 [ ]
20:50:46 charon: 07[NET] received packet: from 173.15.187.122[4500] to 96.83.209.249[4500] (80 bytes)
20:50:16 charon: 07[NET] sending packet: from 96.83.209.249[4500] to 173.15.187.122[4500] (80 bytes)
20:50:16 charon: 07[ENC] generating INFORMATIONAL response 205 [ ]
20:50:16 charon: 07[ENC] parsed INFORMATIONAL request 205 [ ]
20:50:16 charon: 07[NET] received packet: from 173.15.187.122[4500] to 96.83.209.249[4500] (80 bytes)
20:49:46 charon: 11[NET] sending packet: from 96.83.209.249[4500] to 173.15.187.122[4500] (80 bytes)
20:49:46 charon: 11[ENC] generating INFORMATIONAL response 204 [ ]
20:49:46 charon: 11[ENC] parsed INFORMATIONAL request 204 [ ]
20:49:46 charon: 11[NET] received packet: from 173.15.187.122[4500] to 96.83.209.249[4500] (80 bytes)
20:49:16 charon: 14[NET] sending packet: from 96.83.209.249[4500] to 173.15.187.122[4500] (80 bytes)
20:49:16 charon: 14[ENC] generating INFORMATIONAL response 203 [ ]
20:49:16 charon: 14[ENC] parsed INFORMATIONAL request 203 [ ]
20:49:16 charon: 14[NET] received packet: from 173.15.187.122[4500] to 96.83.209.249[4500] (80 bytes)
20:48:46 charon: 12[NET] sending packet: from 96.83.209.249[4500] to 173.15.187.122[4500] (80 bytes)
pmueller
11 May 2022 09:13
8
Hi all,
sorry for the late response.
While I am unaware of Core Update 167 introducing any general IPsec issues (and all my IPsec connections are working fine as far as I am aware), this sounds more like being a firewalling or routing problem, as toggling the “drop hostile” feature causes the firewall engine to be reloaded.
Are there any correlating firewall hits during the time IPsec tunnels are not working? If so, could you please post them here?
Thanks, and best regards,
I am also facing some Core Update 167 IPsec issues.
I have a SonicWall TZ500 and I’m using the SonicWall Global VPN Client to connect to my office network. The VPN connection works fine before the Core Update, but after the Core Update, I can’t access anything on my office network. I am able to ping the gateway, but not anything within my office subnet.
pmueller
11 May 2022 13:34
10
Hi,
thank you for reporting this.
Do you mean the remote IPsec peer by “gateway”? If so, I guess IPsec is generally working, but you are facing a routing/firewalling issue for some reason. Should that be the case, please look for firewall hits correlating, and kindly post them here.
Thanks, and best regards,
donbrill
11 May 2022 16:09
11
I’m seeing no traffic through IPsec VPN tunnels anywhere I’ve Core Update 167 to Core Update 167 even though the ipfire web console reports the VPN is “Open”. If either box is Core Update 166, no issue.
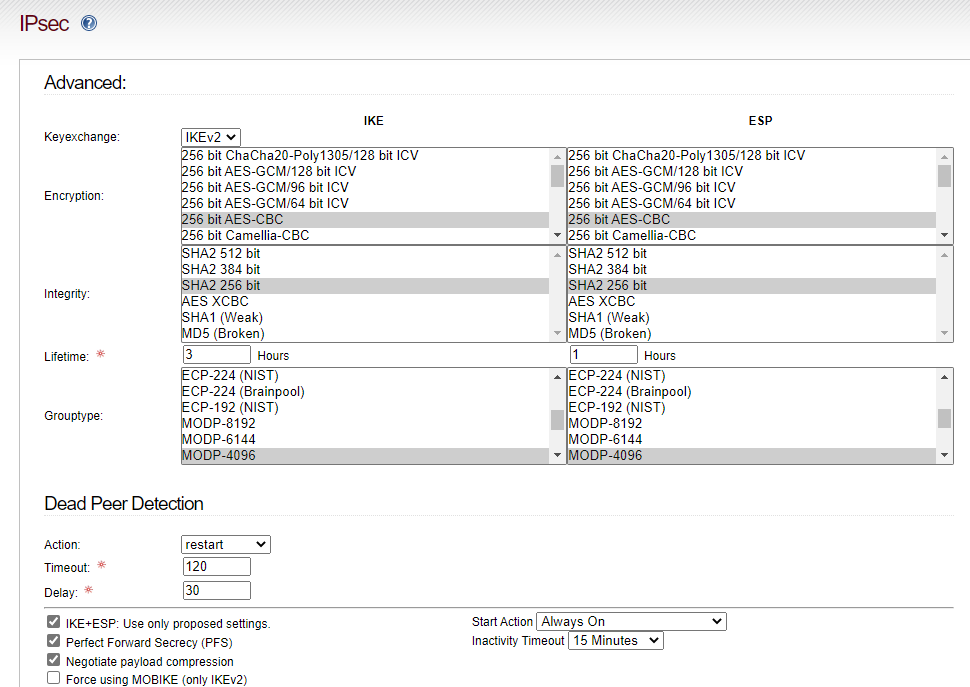
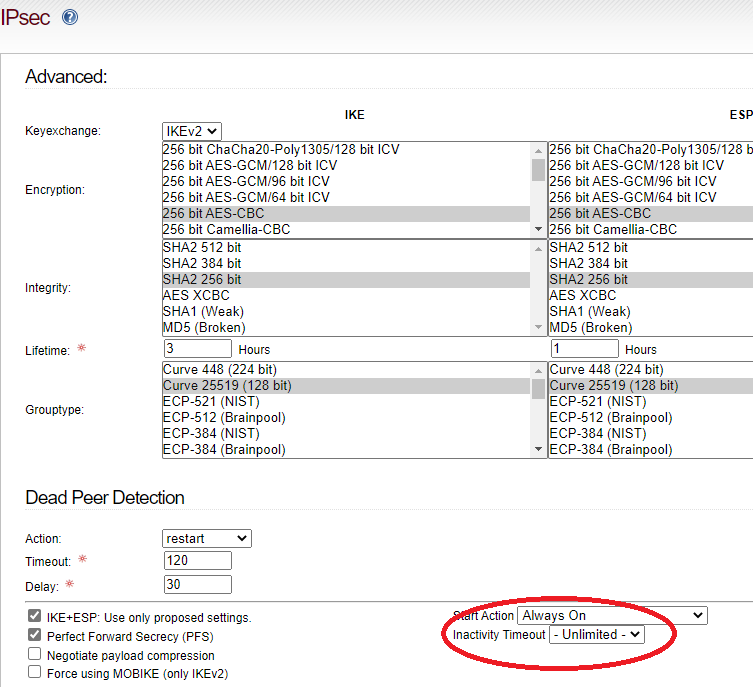
Started trying this setting on the advanced screen last night:
The default value for Inactivity Timeout is 15 Minutes, which on previous updates appears to be fine. I’m having fewer issues with 167 if I set both ends of the VPN to " - Unlimited -", however making that change will not getting traffic moving along the tunnel. If I login to an ipfire console and ping the green interface of the remote ipfire box then traffic starts moving along the tunnel.
donbrill
18 May 2022 14:57
12
I’m seeing the same issue with the 168 build that is in testing.
pmueller
18 May 2022 15:15
13
Hi,
thank you for reporting back.
Core Update 167 came with an updated version of strongSwan , which changelog is available here . Aside from that, I cannot really think of any changes introduced with Core Update 167 that could cause your issue.
Some IPsec N2N connections with Core Update 167 work fine with me.
I’ll try something else I currently have in mind and will get back to you.
EDIT: I was just able to reproduce this issue with an IPsec N2N connection involving two IPFire machines running Core Update 167. Looks like firewall rules for the ESP traffic are missing, I believe this was caused by this commit. See also bug #12808 .
Thanks, and best regards,
pmueller
18 May 2022 15:34
14
For the records: Bug #12866 has been raised for this.
Apologies for the inconvenience.
1 Like
pmueller
20 May 2022 06:19
15
Hi,
for your information: A fix is already available , and will land in Core Update 168 shortly.
Thanks, and best regards,
5 Likes
chrisk1
20 May 2022 11:44
16
Uh! Glad that I saw this here before updating all or instances.
@pmueller I’m missing any statement to this fix in the release info of Core 168? Is it just missing here? Or did the patch not yet get into this testing release? blog.ipfire.org - IPFire 2.27 - Core Update 168 is available for testing
The fix was submitted early this morning. You can check the nightlies to see when the ‘latest’ entry has been updated and at that point a Testing update will have it included.
https://wiki.ipfire.org/devel/nightly-builds
1 Like
pmueller
21 May 2022 07:15
18
Hi,
as @bonnietwin already mentioned, there is no stable release of Core Update 168 yet. It is almost ready, though, with one major and one minor issues aside the IPsec thing still to be fixed. My personal ETA for this update would be around the end of May or the beginning of June.
Not yet indeed, since there is currently still one thing to clarify. As soon as we have that done, the current next branch can be merged into master, and then you will have the patch in Core Update 168 (testing).
Therefore, I ask for a little more patience.
Thanks, and best regards,
2 Likes
pmueller
6 June 2022 10:33
20
Hi,
apologies for the delay.
Core Update 168 is ready to be released, and I expect it to be available over the course of next week.
Thanks, and best regards,
3 Likes