2022-12-06 16:32:00 DEPRECATED OPTION: --cipher set to 'AES-256-CBC' but missing in --data-ciphers (AES-256-GCM:AES-128-GCM). Future OpenVPN version will ignore --cipher for cipher negotiations. Add 'AES-256-CBC' to --data-ciphers or change --cipher 'AES-256-CBC' to --data-ciphers-fallback 'AES-256-CBC' to silence this warning.
2022-12-06 16:32:00 OpenVPN 2.5.7 Windows-MSVC [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11] [AEAD] built on May 27 2022
2022-12-06 16:32:00 Windows version 10.0 (Windows 10 or greater) 64bit
2022-12-06 16:32:00 library versions: OpenSSL 1.1.1o 3 May 2022, LZO 2.10
2022-12-06 16:32:00 MANAGEMENT: TCP Socket listening on [AF_INET]127.0.0.1:25341
2022-12-06 16:32:00 Need hold release from management interface, waiting...
2022-12-06 16:32:00 MANAGEMENT: Client connected from [AF_INET]127.0.0.1:25341
2022-12-06 16:32:00 MANAGEMENT: CMD 'state on'
2022-12-06 16:32:00 MANAGEMENT: CMD 'log all on'
2022-12-06 16:32:00 MANAGEMENT: CMD 'echo all on'
2022-12-06 16:32:00 MANAGEMENT: CMD 'bytecount 5'
2022-12-06 16:32:00 MANAGEMENT: CMD 'hold off'
2022-12-06 16:32:00 MANAGEMENT: CMD 'hold release'
2022-12-06 16:32:15 MANAGEMENT: CMD 'password [...]'
2022-12-06 16:32:15 Outgoing Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
2022-12-06 16:32:15 Incoming Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
2022-12-06 16:32:15 MANAGEMENT: >STATE:1670340735,RESOLVE,,,,,,
2022-12-06 16:32:15 TCP/UDP: Preserving recently used remote address: [AF_INET]XXXXXXXXXXXXXXXXXXX:1194
2022-12-06 16:32:15 Socket Buffers: R=[65536->65536] S=[65536->65536]
2022-12-06 16:32:15 UDP link local: (not bound)
2022-12-06 16:32:15 UDP link remote: [AF_INET]XXXXXXXXXXXXXXXXXXX:1194
2022-12-06 16:32:15 MANAGEMENT: >STATE:1670340735,WAIT,,,,,,
2022-12-06 16:32:15 MANAGEMENT: >STATE:1670340735,AUTH,,,,,,
2022-12-06 16:32:15 TLS: Initial packet from [AF_INET]XXXXXXXXXXXXXXXXXXX:1194, sid=767acfff bf552ac6
2022-12-06 16:32:15 VERIFY OK: depth=1, C=DE, O=XXXXXXXXXXXXXXXXXXX, CN=XXXXXXXXXXXXXXXXXXX CA
2022-12-06 16:32:15 VERIFY KU OK
2022-12-06 16:32:15 Validating certificate extended key usage
2022-12-06 16:32:15 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
2022-12-06 16:32:15 VERIFY EKU OK
2022-12-06 16:32:15 VERIFY X509NAME OK: C=DE, O=XXXXXXXXXXXXXXXXXXX, CN=XXXXXXXXXXXXXXXXXXX
2022-12-06 16:32:15 VERIFY OK: depth=0, C=DE, O=XXXXXXXXXXXXXXXXXXX, CN=XXXXXXXXXXXXXXXXXXX
2022-12-06 16:32:15 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 2048 bit RSA, signature: RSA-SHA256
2022-12-06 16:32:15 [XXXXXXXXXXXXXXXXXXX] Peer Connection Initiated with [AF_INET]XXXXXXXXXXXXXXXXXXX:1194
2022-12-06 16:32:16 MANAGEMENT: >STATE:1670340736,GET_CONFIG,,,,,,
2022-12-06 16:32:16 SENT CONTROL [XXXXXXXXXXXXXXXXXXX]: 'PUSH_REQUEST' (status=1)
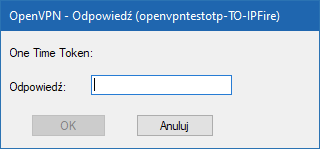
2022-12-06 16:32:16 AUTH: Received control message: AUTH_FAILED,CRV1:R,E:UXXXXXXXXXXXXXXXXXXX:XXXXXXXXXXXXXXXXXXX==:One Time Token:
2022-12-06 16:32:16 SIGUSR1[soft,auth-failure (auth-token)] received, process restarting
2022-12-06 16:32:16 MANAGEMENT: >STATE:1670340736,RECONNECTING,auth-failure (auth-token),,,,,
2022-12-06 16:32:16 Restart pause, 5 second(s)
2022-12-06 16:33:30 MANAGEMENT: Client disconnected
2022-12-06 16:33:30 ERROR: could not read Private Key username/password/ok/string from management interface
2022-12-06 16:33:30 Exiting due to fatal error