After reading an older post
How to disable ssh from RED - Dec2020
it occurred to me that ANY device connected to green could become a BACKDOOR for the outside world and access IpFire’s WebUI, or the SSH port. It’s every Security I.T’s nightmare; an employee that connects their badly compromised laptop to the company network.
In the case of the prior post I suspect it may have been the Pi-Hole installed on the green, as my playing around with Pi-Hole one or two years ago produced some odd behaviour activity which made me drop the project. Never had time to futher investigate.
Anyways back to my topic…
In order to tighten up security of any device access to ipFire’s WebUI and SSH ports from the green (this is already blocked on blue by default) I created rulesets that would allow full access to only one specific IP, own by one fully trusted device having a static IP, and blocking access to ports 444, 222, and 81 for all others.
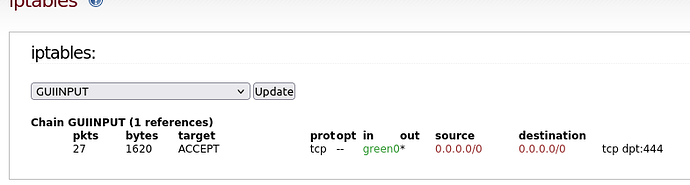
In firewall groups I created the ports entries, and added those to a new Service Group call ipFire_Access_Ports, and used that to create the blocking rule. See my INPUTFW chain
Chain INPUTFW (1 references)
target prot opt in out source destination
LOG all – * * 192.168.68.181 192.168.68.1 limit: avg 10/sec burst 20 LOG flags 0 level 4 prefix "INPUTFW "
ACCEPT all – * * 192.168.68.181 192.168.68.1
LOG tcp – * * 192.168.68.0/24 192.168.68.1 multiport dports 444,222,81 limit: avg 10/sec burst 20 LOG flags 0 level 4 prefix "INPUTFW "
DROP tcp – * * 192.168.68.0/24 192.168.68.1 multiport dports 444,222,81
LOG udp – * * 192.168.68.0/24 192.168.68.1 multiport dports 444,222,81 limit: avg 10/sec burst 20 LOG flags 0 level 4 prefix "INPUTFW "
DROP udp – * * 192.168.68.0/24 192.168.68.1 multiport dports 444,222,81
The new rules works for SSH port 222 as I can access SSH from my trusted PC, and is blocked when accessing from another PC.
However, I was still able to get to the WebUI port 444 from the other PC !!!
I did a netstat -tulpen and got the following …
[root@ipfire ~]# netstat -tulpen
Active Internet connections (only servers)
Proto Local Address Foreign Address State User Inode PID/Program name
tcp 0.0.0.0:222 0.0.0.0:* LISTEN 0 330399 14760/sshd: /usr/sb
tcp 0.0.0.0:53 0.0.0.0:* LISTEN 0 23337 3020/unbound
tcp 127.0.0.1:8953 0.0.0.0:* LISTEN 0 23339 3020/unbound
tcp6 :::444 :::* LISTEN 0 30170 5008/httpd
tcp6 :::81 :::* LISTEN 0 30166 5008/httpd
tcp6 :::1013 :::* LISTEN 0 30174 5008/httpd
udp 0.0.0.0:53 0.0.0.0:* 0 23336 3020/unbound
udp 0.0.0.0:67 0.0.0.0:* 0 159290 11924/dhcpd
udp 192.168.0.101:68 0.0.0.0:* 0 29731 730/dhcpcd: [netwo
udp 192.168.68.1:123 0.0.0.0:* 0 29945 4893/ntpd
udp 192.168.0.101:123 0.0.0.0:* 0 29943 4893/ntpd
udp 127.0.0.1:123 0.0.0.0:* 0 29941 4893/ntpd
udp 0.0.0.0:123 0.0.0.0:* 0 29936 4893/ntpd
udp 0.0.0.0:514 0.0.0.0:* 0 23297 2983/syslogd
udp6 :::123 :::* 0 29933 4893/ntpd
The tcp6 :::444 caught my eye.
Is it possible that even though the rule was blocking tcpV4 traffic that it was letting through tcpV6 from my other PC (A win10 box)?
Oddly in that the netstat did not display a listening for 222 for tcp6, and the rule worked correctly for that one.
Is there a way to disable tcp6 listening on port 444 ?