Is there a way to block urls using wildcards. I am trying to block all .xxx sites
Would be a nice feature!
You may not need to use wildcards as far as I know, if the domain name hierarchy is respected in the list…
E.g. say you wanted to block only ‘community.ipfire.org’ then you would add that to the list. That would still allow www.ipfire.org and any other sub-domain/sub-sites to work.
If you wanted to block everything from that domain then just put in: ‘ipfire.org’ - that would block anything from that domain.
If you want to block an entire region/zone/group such as .org, .biz, or .xxx in this case, maybe you could just try adding xxx to the list and seeing if it works at blocking domain names based on the tree hierarchy. Otherwise you may need to use the custom expression - I believe that allows wildcards to be used but not entirely familiar with the notation used.
Not tested it myself as not using proxy (any more).
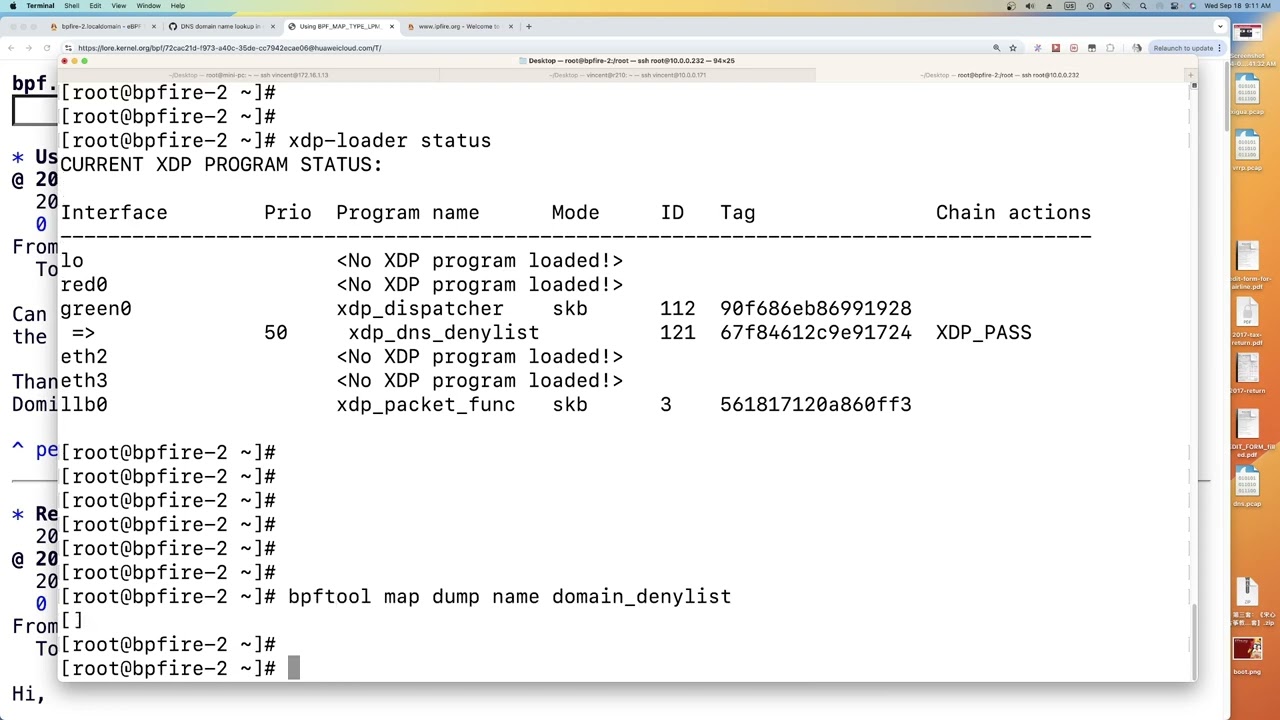
this is alternative option, which can be achieved by simple XDP DNS wildcard blocklist, for example put example.com in blocklist, xxx.example.com will be blocked. https://www.youtube.com/watch?v=luFBhVU8FPM&t=2s. I am also working with lunatik maintainer GitHub - luainkernel/lunatik: Lunatik is a framework for scripting the Linux kernel with Lua. to block site by TLS/SSL server name extension, only one issue left which is can’t block chrome browser because chrome has large clienthello payload > MTU 1500 bytes, this does not work well with XDP in consumer/home network environment, but can be worked around by fall back to netfilter.
This is way above my pay grade. I was just looking for a simple way to block xxx sites within IPFire
it is free and open source solution ![]() my goal is to bring enterprise data center technology to consumer/home network with open source technology GitHub - vincentmli/BPFire: BPFire development tree
my goal is to bring enterprise data center technology to consumer/home network with open source technology GitHub - vincentmli/BPFire: BPFire development tree
If there was a easy way to add block list to the IPS system that would be great. Not sure how that would be done…
this can be easily done in DNS eBPF XDP longest prefix match trie map that is implemented in BPFire. just simple as add .mov and .zip in the eBPF map, easy and efficient, and a cheap mini PC could do it since XDP runs from the driver, not much resource required.
for folks who is concerned about XDP security, the code I developed is actually based on DNS unbound author Journeying into XDP: Part 0
hello
it would be great if instead of installing a fork of ipfire there is a pakfire of ipfire
it is not matter of simply install pakfire package, it is the kernel requires eBPF to be enabled which is not possible for ipfire at this time.
it’s a real shame not to be able to integrate these functions into the main distribution
maybe if it were possible I would somehow install them on the official distribution
maybe in the future
A discussion about this topic was started on devel mailing list.
Don’t know the actual state, but maybe @vincentmli knows.
there are quite a few requirements to have kernel with eBPF feature enabled, like add pahole addon to generate BTF during kernel build, enable kernel eBPF config and a few debug kernel config, increase build temporary space, strip kernel module debug symbols…etc. it is not small change to kernel, ipfire devs has not shown interest to explore eBPF, from what I understand, mostly due to lack of understanding about eBPF.
I am using the URL filter - www.ipfire.org - URL filter and I did blocked entire ccTLD (like .cn, .by), entire domains (like adnx.com), subdomain (analytics.yahoo.com) or just a specific URL.
Basically I used almost all blocking features listed there except the “Custom expression list” (that looks like RegEx to me)…
To have all above working each client must use the proxy from ipfire and that is achieved via DHCP & DNS (WPAD is sent by DHCP and also resolved by DNS)
Would it take less RAM or CPU resources if Norm would use Unbound / RPZ blocklist?
it would be even less with XDP since it runs in the kernel. but I know it is a fork, too bad ![]()
You might be right, XDP could blow the Pi out of Pihole ![]()
on the DNS topic, I just added new XDP DNS blocklist feature to log the query name and source ip in system log, happens someone asked this for unbound before in ipfire ![]() Unbound (and other programs ) logging - #32 by bonnietwin
Unbound (and other programs ) logging - #32 by bonnietwin
Vincent
Stop sending me these emails. i have no idea what they meean!!!
I am just posting here, not sending email to you specifically, blocking post from me if you don’t like it
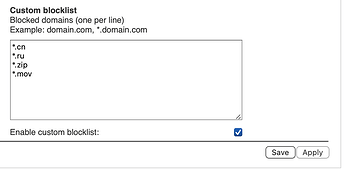
RPZ will do a DNS block and uses wildcards. The user would enter *.xxx to block everything in that Top Level Domain (TLD).
Right now I block these (as an example):
If you are interested I can help get you started. Add your questions or a request for assistance here in this thread:
The email happens because someone is adding a response to your original post. You can block the user or block this entire thread. Let me know which you’d prefer and I will assist.