Hello Forum,
i’m new here searching for a reasonable replacement for a recently bought Unifi Dream Machine (UDM, an all in one Firewall, Access Point and Managed 4-Port Gigabit Switch-Device), that sounded good first but is way far from being stable, is only usable with an ubiquity account and as i found out today, likes to phone home even if i opt out in the unifi controller. So this device needs to go away soon. Added to that i bought a Unifi managed 24-port Switch and two Access Points, that i don’t really want to get rid of. So only a replacement for UDM is needed. An IPFire with an extra Access Point seems to be a good alternative for a SOHO environment. I’m not a firewall expert and additionally a native german speaker, so i hope you understand, what i want to ask. Apologizes, if it is not that clear 
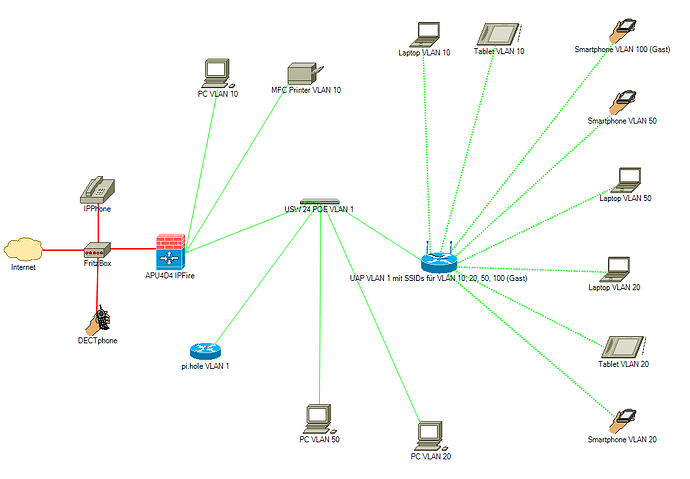
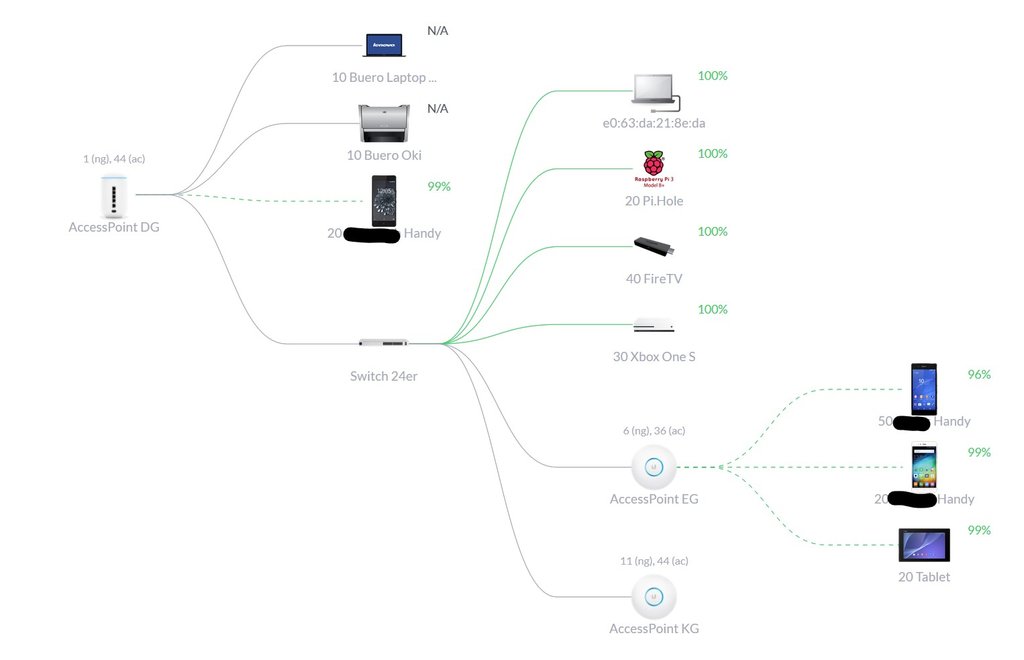
I uploaded the desired layout as attachment. There are more wired and wireless clients, another two VLANS one with a wired Xbox and one with a wired FireTV stick and not one but three Access Points, but the general layout doesn’t change with that additional devices. So i left them out for clarity.
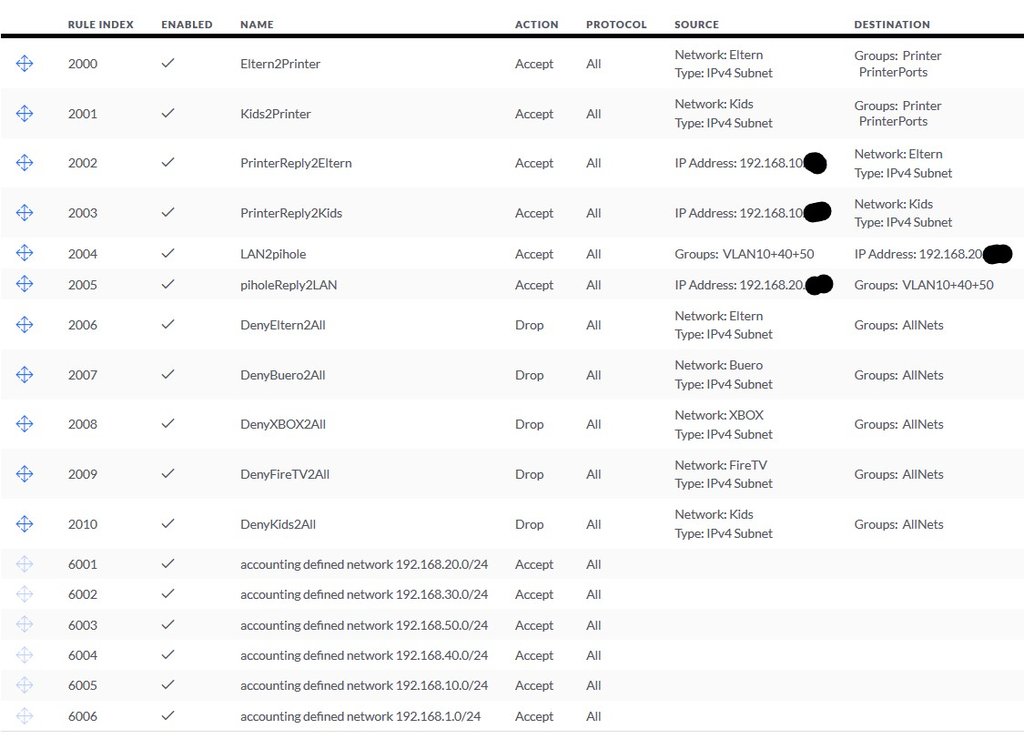
First, there is a Fritzbox serving as the VDSL modem and DECT-Base for IP-Telephones (wired and wireless) in the red area. Then comes the IPFirebox (at the moment planned APU4D4 if reasonable), because i need besides the WAN-Port and the Port to connect the Switch on Admin-VLAN 1 at least another two Gigabit Ports to connect my office Equipment (Laptop and Printer/Scanner-Device) directly to that box on VLAN10 because it is not possible to connect them to the switch. All these devices should be in the green area, if i understand that principle correctly. And not to forget a Raspberry Pi with pi.hole serving as the primary DNS-Server, AdBlocker and anti-tracking for the whole green area (except the Guest VLAN 100).
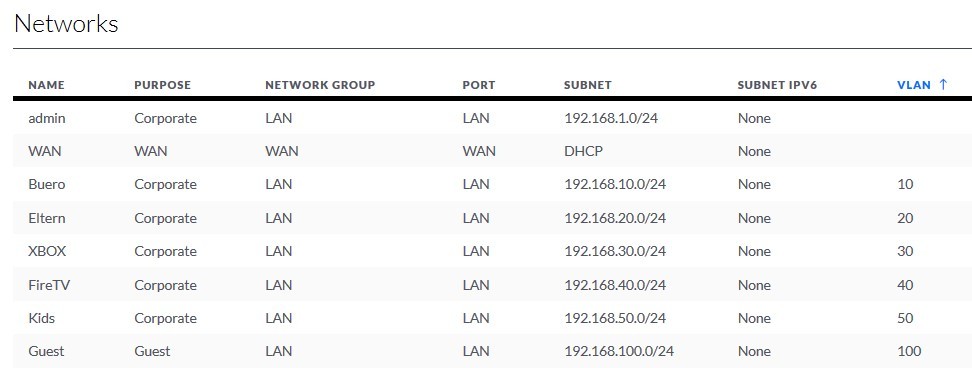
The managed switch has POE-ports leading to the access points in the Admin-VLAN 1 broadcasting four different SSIDs on VLANs 10, 20, 50 and 100. 100 is the guest VLAN with a different port range.
At the moment, the UDM sits at the place of the (maybee soon to be there) IPFirebox and because everything is Unifi, it is very easy to assign the same VLANs to the Switch-Ports on the UDM and the Switch-Ports on the Unifi Switch.
So my questions are now: Is it also possible to assign the same VLANs on the IPFirebox-Ports and on the Unifi-Switch-Ports? And if yes, is the APU4D4 sufficient for a 100Mbit-VDSL-Line, IPS with suricata and at least 10 devices in local network (one of them streaming netflix, one Xbox, one streaming youtube and one homeoffice device remotely connecting to a company server). Or should i look for a more powerful device? Two more Ports on the IPFire-Device wouldn’t hurt either. And it needs to be fanless. Any suggestions are appreciated.
So, i hope you understand what i’ve written 
I’m looking forward to your answers. Thank you in advance
Chris