Good morning.
I would like to know if there is any way to mitigate the vulnerabilities affecting the Broadcom BCM2711, 64-bit Cortex-A72 (ARM v8) 64-bit 1.5 GHz. microprocessor of the raspberry pi 4 on ipfire:
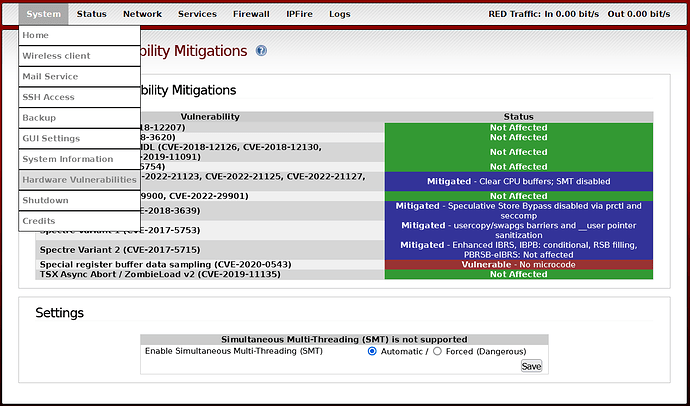
Spectre Variant 4 (CVE-2018-3639) Vulnerable
Spectre Variant 2 (CVE-2017-5715) Vulnerable
Thank you very much!
Thanks! yeah that’s where I saw that they are vulnerable, but it doesn’t say anything specific to fix it in the ipfire OS.
The mitigation for spectre variant 4 on my x86_64 says
Speculative Store Bypass disabled via prctl and seccomp
This approach was not possible earlier as seccomp was not activated for arm as some boards ended up with other problems when it was enabled.
That issue has now been resolved and seccomp was enabled in CU171.
If you are not on CU171 try updating to it and see if that changes the Spectre Variant 4 message from vulnerable to mitigated.
I am not sure why the Spectre Variant 2 message does not say mitigated. I have not currently found anything indicating a problem with the mitigation for Spectre Variant 2 on ARM but that does not mean that it doesn’t exist.
Generally if the table says vulnerable then it means that the system is vulnerable and there is no fix or mitigation currently available.
2 Likes
Thanks for your answer. by CU171 you mean update 171? i currently have that update and it still says it is vulnerable. do you think there is a possibility to apply the patches that the manufacturer indicates for linux on the ipfire OS?
Yes. Rather than typing Core Update each time I tend to abbreviate it to CU.
Typically the developers will try and apply any hardware vulnerability kernel patches as soon as they are able to. There is only one developer in the IPFire team that is expert on the kernel.
Sometimes applying the kernel patches causes other issues to arise that stop the processor working at all. This was the case with the seccomp fix that was applied to x86_64 but not to arm until CU171.
I have no familiarity with the kernel aspects of IPFire at all.
Hopefully @arne_f can give you some input on the patches you mention and why your processor is still showing as vulnerable with Spectre Variant 2 and Spectre Variant 4 with CU171.
I will wait for the developers to solve it. I already tried it on my own and the only thing I got is that ipfire didn’t work and I had to install it from 0, luckily I had a backup. Thank you very much Adolf, have a nice weekend.