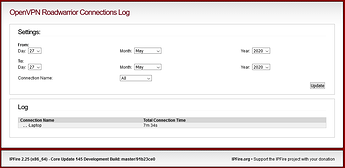
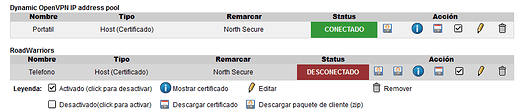
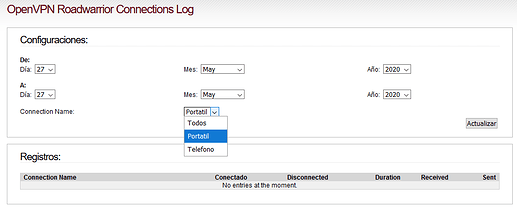
I have been doing more tests without result, no data appears.
|17:41:45|openvpnserver[3050]: Portatil/xxx.xxx.xxx.xxx:7861 SENT CONTROL [Portatil]: |'PUSH_REPLY,route 10.113.239.1,topology net30,route 10.254.0.0 255.255.255.0,ifc onfig 10.113.239.6 10.113.239.5,peer-id 0' (status=1)|
|---|---|---|
|17:41:45|openvpnserver[3050]: |Portatil/xxx.xxx.xxx.xxx:7861 PUSH: Received control message: 'PUSH_REQUEST'|
|17:41:44|openvpnserver[3050]: |Portatil/xxx.xxx.xxx.xxx:7861 MULTI: primary virtual IP for Portatil/xxx.xxx.xxx. xxx:7861: 10.113.239.6|
|17:41:44|openvpnserver[3050]: |Portatil/xxx.xxx.xxx.xxx:7861 MULTI: Learn: 10.113.239.6 -> Portatil/xxx.xxx.xxx. xxx:7861|
|17:41:44|openvpnserver[3050]: |Portatil/xxx.xxx.xxx.xxx:7861 MULTI_sva: pool returned IPv4=10.113.239.6, IPv6=(N ot enabled)|
|17:41:44|openvpnserver[3050]: |Portatil/xxx.xxx.xxx.xxx:7861 OPTIONS IMPORT: reading client specific options fro m: /var/ipfire/ovpn/ccd/Portatil|
|17:41:44|openvpnserver[3050]: |xxx.xxx.xxx.xxx:7861 [Portatil] Peer Connection Initiated with [AF_INET]xxx.xxx.xxx.xxx.56:7861|
|17:41:44|openvpnserver[3050]: |xxx.xxx.xxx.xxx:7861 Control Channel: TLSv1.2, cipher TLSv1.2 ECDHE-RSA-AES256-GC M-SHA384, 2048 bit RSA|
|17:41:44|openvpnserver[3050]: |xxx.xxx.xxx.xxx:7861 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key|
|17:41:44|openvpnserver[3050]: |xxx.xxx.xxx.xxx:7861 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key|
|17:41:44|openvpnserver[3050]: |xxx.xxx.xxx.xxx:7861 peer info: IV_GUI_VER=OpenVPN_GUI_11|
|17:41:44|openvpnserver[3050]: |xxx.xxx.xxx.xxx:7861 peer info: IV_TCPNL=1|
|17:41:44|openvpnserver[3050]: |xxx.xxx.xxx.xxx:7861 peer info: IV_COMP_STUBv2=1|
|17:41:44|openvpnserver[3050]: |xxx.xxx.xxx.xxx:7861 peer info: IV_COMP_STUB=1|
|17:41:44|openvpnserver[3050]: |xxx.xxx.xxx.xxx:7861 peer info: IV_LZO=1|
|17:41:44|openvpnserver[3050]: |xxx.xxx.xxx.xxx:7861 peer info: IV_LZ4v2=1|
|17:41:44|openvpnserver[3050]: |xxx.xxx.xxx.xxx:7861 peer info: IV_LZ4=1|
|17:41:44|openvpnserver[3050]: |xxx.xxx.xxx.xxx:7861 peer info: IV_NCP=2|
|17:41:44|openvpnserver[3050]: |xxx.xxx.xxx.xxx:7861 peer info: IV_PROTO=2|
|17:41:44|openvpnserver[3050]: |xxx.xxx.xxx.xxx:7861 peer info: IV_PLAT=win|
|17:41:44|openvpnserver[3050]: |xxx.xxx.xxx.xxx:7861 peer info: IV_VER=2.4.7|
|17:41:44|openvpnserver[3050]: |xxx.xxx.xxx.xxx:7861 VERIFY OK: depth=0, C=ES, ST=Bizkaia, O=North Secure, OU=Nor th Secure, CN=Portatil|
|17:41:44|openvpnserver[3050]: |xxx.xxx.xxx.xxx:7861 VERIFY SCRIPT OK: depth=0, C=ES, ST=Bizkaia, O=North Secure, OU=North Secure, CN=Portatil|
|17:41:44|openvpnserver[3050]: |xxx.xxx.xxx.xxx:7861 VERIFY OK: depth=1, C=ES, ST=Bizkaia, L=Derio, O=North Secur e, OU=Informatica, CN=North Secure CA, emailAddress=contacto@northsecure.es|
|17:41:44|openvpnserver[3050]: |xxx.xxx.xxx.xxx:7861 VERIFY SCRIPT OK: depth=1, C=ES, ST=Bizkaia, L=Derio, O=Nort h Secure, OU=Informatica, CN=North Secure CA, emailAddress=contacto@northsecure. es|
|17:41:43|openvpnserver[3050]: |xxx.xxx.xxx.xxx:7861 TLS: Initial packet from [AF_INET]xxx.xxx.xxx.xxx:7861, sid=8 831bd78 93fc1498|
|17:41:43|openvpnserver[3050]: |xxx.xxx.xxx.xxx:7861 WARNING: normally if you use --mssfix and/or --fragment, you should also set --tun-mtu 1500 (currently it is 1400)|
|17:11:57|openvpnserver[3050]: |Telefono/xxx.xxx.xxx.xxx:19705 SIGTERM[soft,remote-exit] received, client-instanc e exiting|
|17:11:49|openvpnserver[3050]: |Telefono/xxx.xxx.xxx.xxx:19705 AEAD Decrypt error: bad packet ID (may be a replay ): [ #9 ] -- see the man page entry for --no-replay and --replay-window for more info or silence this warning with --mute-replay-warnings|
And this is what appears:
Logically, I have closed the connection and nothing appears or waiting for a while.
I have tried with both that I have without result.
Any ideas?.
Regards.