Dear IPFire experts,
I now use the Fire in my home setup for years and I love the easy to operate openVPN server feature. Now I’m asking myself if I could us the IPFire in another Setup (router exists) as a openVPN server. Let’s say the other network is 192.168.0.0/24, how should I configure the red interface in this case? Can it be in the same network like the green one?
Do I have to disable some services (okay, DHCP for sure… rounting?).
Or is this a very stupid idea?
Thanks and cheers buddies!
A basic idea of a firewall, red (WAN) cannot be in the same subnet as green (LAN).
If you could provide a diagram, it would help to understand what you want to do.
Dear paul,
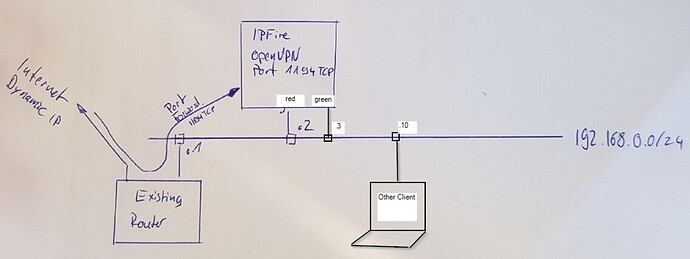
sorry for beeing unspecific, please see my drawing.
My approach is, to use the IPFire as a OpenVPN server inside a existing network, without using both, RED and GREEN interface. Blasphemic, isn’t it? ![]()
I finally found out how this can be done, only using the RED interface. It’s dirty, but I’ll give a short description for other people that are trying to do like me.
-
Installed a fresh IPFire (in a VM)
-
Network config:
RED: Fixed IP within existing LAN, in my example 192.168.0.2
GREEN: Fixed IP within existing LAN, in my example 192.168.0.3 (this interface will be used for setup/access to webinterface only and be disconnected later)
DHCP disabled! -
Access web interface ( GREEN IP https://192.168.0.3:444), create new firewall rules to allow access to the web interface and ssh from RED
Source: Network RED → Destination NAT → Destination: Firewall ALL, Destination Port 444
Second rule:
Source: Network RED → Destination NAT → Destination: Firewall ALL, Destination Port 222 -
Try if you can reach the web interface through the RED IP (https://192.168.0.2:444). If yes, you can now disconnect the GREEN interface forever!
-
Change the LAN-Setting for the GREEN Interface to someting stupid (like 192.168.222.0/24).
(by calling “setup” from the shell) -
Check if the IPFire has received the corect date/time. This is later needed for creating the openvpn base CA)
-
Enable SSH access (System->SSH access)
-
Navigate to “services->OpenVPN” and create the X509 base Certifiacate
-
Create a roadwarrior certificates
-
Start openVPN server, relax, take a beer, enjoy the sunshine

Hope that gave you a good starting point to create your VPNFire…
You could build a container and install just openvpn server. To me, this is much easier than to have an ipfire vm (since ipfire will not act as a firewall). But, anyone can do anything, if that works for you, ok.
I have the same Idee with the IPFire-OpenVPN Server.
The Ipfire Webinterface ist perfekt to manage the OPEN-VPN-SERVER.
Now i have one Problem:
I connect with a client at home(e.g. 192.168.178.0/24) to my work Network (e.g. 192.168.243.0/24)
My Home-PC habe over the VPN connection the IP:10.20.41.6
Now i want with my Home-PC a Windows-Server share use on the IP: 192.168.243.252 Folder: all
If i Ping with my Home-PC to 192.168.243.252 i dont get a answer from my server.
If i want use the Windows-server share with //192.168.243.252/all i get a error server not found.
If i use a Networkscan software on my Home-PC i found only the Green(192.168.243.244)-,Red(192.168.243.113)-Interface and the LANCOM-Gateway: 192.168.243.1
My IpFire have the Config: RED->DHCP, GREEN:Static:192.168.243.244
My LANCOM is the DHCP-Server
What i must config that my Home-PC can use over OPENVPN the Windows-server-sahre folder ?
Sorry for my bad english. My English was long time ago in school
You’re right, paul. Simply using openvpn server would be the easies one. But that comes without a nice and easy to use web interface. I like the way, IPFire implemented the vpn use rmanagement, online monitor, ie…
Dear Robert,
no problem, your english is OK, it reads a little bit german? ![]()
I guess, your problem is that the red and the green interface are in the same subnet. I had exactly the same reaction from my fire when I played around.
For me the solution was
- To give the red interface a static IP/SM
- To make the webinterface and ssh accessable from the RED interface (by creating the firewall rules)
- To give the green interface a completely different IP in a different subnet and than finally DISCONNECT the green interface.
My strong suggestion: Get rid of the green Interface, don’t use it!
Why? I guess (not know) because you can not set a “default gateway” for the green interface. The green interface always uses IPCop itself as default gateway! Second reason (in my understanding) is, that it’s more clean and easy for IPFires routing, not to have two interfaces in the same subnet.
Take care that you don’t forget to assign the correcte default gateway to the red interface ![]()
I cross fingers for you ![]()
Wau its Work ! Thank you, that was a nice tip. But i dont habe disconnect the green interface. Im dont in the room / space its over 100km away. I want drive to the problem but i dont must ![]()
TANK YOU AGAIN !!!
You’re very welcome, Robert ![]()
I forgot a important point. In another Setup i only got it working by setting [X] Redirect gateway in the RoadWarriors profile. Maybe that yould be important?