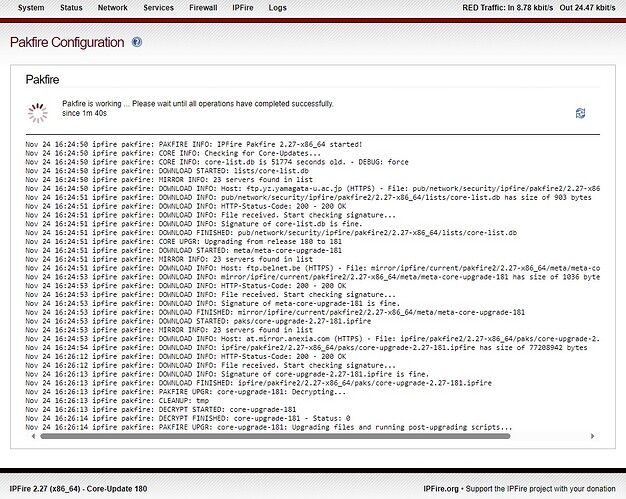
During my update from CU 180 to CU 181 (on a PC Engine APU4D4), the WebGUI stalled for a long time after:
10:20:18 pakfire: PAKFIRE UPGR: core-upgrade-181: Upgrading files and running post-upgrading scri pts...
.
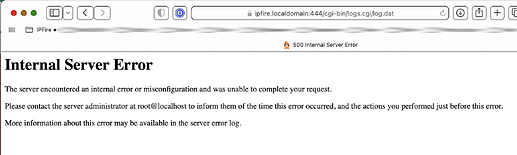
And I could no longer refresh the browser to see the System Logs > Pakfire log:
Note: I was watching the message log and the Pakfire WebGUI and the System Logs > Pakfire at the same time (a belts and suspenders approach!!)
For me it seems like the Apache restarted and after a minute or so it finally came back. Maybe something is timing out during the restart??
Apache finally started working, but then it stopped, waited, and then started again. Keep in mind I am seeing this from my browser and it displaying the WebGUI and then not displaying.
There are no references to Apache in the message logs. There are messages in the httpd > error log
[Sun Nov 26 09:55:17.255791 2023] [core:error] [pid 31949:tid 124702664144576] (70007)The timeout specified has expired: [client 192.168.60.212:54734] AH00574: ap_content_length_filter: apr_bucket_read() failed, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:05:02.933632 2023] [core:error] [pid 31949:tid 124702680929984] (70007)The timeout specified has expired: [client 192.168.60.212:57651] AH00574: ap_content_length_filter: apr_bucket_read() failed, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:30.279349 2023] [cgid:error] [pid 30884:tid 124702930366656] (13)Permission denied: AH01241: exec of '/srv/web/ipfire/cgi-bin/speed.cgi' failed
[Sun Nov 26 10:24:30.284639 2023] [cgid:error] [pid 31949:tid 124702697715392] [client 192.168.60.212:49399] End of script output before headers: speed.cgi, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:30.810333 2023] [cgid:error] [pid 30885:tid 124702930366656] (13)Permission denied: AH01241: exec of '/srv/web/ipfire/cgi-bin/speed.cgi' failed
[Sun Nov 26 10:24:30.812930 2023] [cgid:error] [pid 31949:tid 124702798362304] [client 192.168.60.212:49946] End of script output before headers: speed.cgi, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:31.077069 2023] [cgid:error] [pid 30886:tid 124702930366656] (13)Permission denied: AH01241: exec of '/srv/web/ipfire/cgi-bin/speed.cgi' failed
[Sun Nov 26 10:24:31.081893 2023] [cgid:error] [pid 31949:tid 124702664144576] [client 192.168.60.212:50016] End of script output before headers: speed.cgi, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:32.337705 2023] [cgid:error] [pid 30887:tid 124702930366656] (13)Permission denied: AH01241: exec of '/srv/web/ipfire/cgi-bin/speed.cgi' failed
[Sun Nov 26 10:24:32.341779 2023] [cgid:error] [pid 31949:tid 124702781576896] [client 192.168.60.212:50024] End of script output before headers: speed.cgi, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:32.849874 2023] [cgid:error] [pid 30892:tid 124702930366656] (13)Permission denied: AH01241: exec of '/srv/web/ipfire/cgi-bin/speed.cgi' failed
[Sun Nov 26 10:24:32.852377 2023] [cgid:error] [pid 31949:tid 124702806755008] [client 192.168.60.212:50031] End of script output before headers: speed.cgi, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:33.787879 2023] [cgid:error] [pid 30893:tid 124702930366656] (13)Permission denied: AH01241: exec of '/srv/web/ipfire/cgi-bin/pakfire.cgi' failed
[Sun Nov 26 10:24:33.790362 2023] [cgid:error] [pid 31949:tid 124702831933120] [client 192.168.60.212:49320] End of script output before headers: pakfire.cgi, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:34.028659 2023] [cgid:error] [pid 30894:tid 124702930366656] (13)Permission denied: AH01241: exec of '/srv/web/ipfire/cgi-bin/speed.cgi' failed
[Sun Nov 26 10:24:34.031572 2023] [cgid:error] [pid 31949:tid 124702815147712] [client 192.168.60.212:50040] End of script output before headers: speed.cgi, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:34.279465 2023] [cgid:error] [pid 30895:tid 124702930366656] (13)Permission denied: AH01241: exec of '/srv/web/ipfire/cgi-bin/speed.cgi' failed
[Sun Nov 26 10:24:34.282126 2023] [cgid:error] [pid 31949:tid 124702672537280] [client 192.168.60.212:50041] End of script output before headers: speed.cgi, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:34.882606 2023] [cgid:error] [pid 30896:tid 124702930366656] (13)Permission denied: AH01241: exec of '/srv/web/ipfire/cgi-bin/speed.cgi' failed
[Sun Nov 26 10:24:34.884984 2023] [cgid:error] [pid 31949:tid 124702680929984] [client 192.168.60.212:50044] End of script output before headers: speed.cgi, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:34.973131 2023] [cgid:error] [pid 30897:tid 124702930366656] (13)Permission denied: AH01241: exec of '/srv/web/ipfire/cgi-bin/pakfire.cgi' failed
[Sun Nov 26 10:24:34.975695 2023] [cgid:error] [pid 31949:tid 124702913717952] [client 192.168.60.212:50045] End of script output before headers: pakfire.cgi, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:35.559319 2023] [cgid:error] [pid 30899:tid 124702930366656] (13)Permission denied: AH01241: exec of '/srv/web/ipfire/cgi-bin/logs.cgi/log.dat' failed
[Sun Nov 26 10:24:35.561932 2023] [cgid:error] [pid 31949:tid 124702697715392] [client 192.168.60.212:50052] End of script output before headers: log.dat, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:36.074747 2023] [cgid:error] [pid 30900:tid 124702930366656] (13)Permission denied: AH01241: exec of '/srv/web/ipfire/cgi-bin/pakfire.cgi' failed
[Sun Nov 26 10:24:36.077146 2023] [cgid:error] [pid 31949:tid 124702664144576] [client 192.168.60.212:50056] End of script output before headers: pakfire.cgi, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:36.100123 2023] [cgid:error] [pid 30901:tid 124702930366656] (13)Permission denied: AH01241: exec of '/srv/web/ipfire/cgi-bin/speed.cgi' failed
[Sun Nov 26 10:24:36.108909 2023] [cgid:error] [pid 31949:tid 124702689322688] [client 192.168.60.212:50054] End of script output before headers: speed.cgi, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:36.256246 2023] [cgid:error] [pid 30902:tid 124702930366656] (13)Permission denied: AH01241: exec of '/srv/web/ipfire/cgi-bin/speed.cgi' failed
[Sun Nov 26 10:24:36.261312 2023] [cgid:error] [pid 31949:tid 124702781576896] [client 192.168.60.212:50060] End of script output before headers: speed.cgi, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:37.286849 2023] [cgid:error] [pid 30903:tid 124702930366656] (13)Permission denied: AH01241: exec of '/srv/web/ipfire/cgi-bin/pakfire.cgi' failed
[Sun Nov 26 10:24:37.289302 2023] [cgid:error] [pid 31949:tid 124702789969600] [client 192.168.60.212:50065] End of script output before headers: pakfire.cgi, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:38.275040 2023] [cgid:error] [pid 30904:tid 124702930366656] (13)Permission denied: AH01241: exec of '/srv/web/ipfire/cgi-bin/speed.cgi' failed
[Sun Nov 26 10:24:38.277696 2023] [cgid:error] [pid 31949:tid 124702655751872] [client 192.168.60.212:50073] End of script output before headers: speed.cgi, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:38.386826 2023] [cgid:error] [pid 30905:tid 124702930366656] (13)Permission denied: AH01241: exec of '/srv/web/ipfire/cgi-bin/pakfire.cgi' failed
[Sun Nov 26 10:24:38.389262 2023] [cgid:error] [pid 31949:tid 124702806755008] [client 192.168.60.212:50075] End of script output before headers: pakfire.cgi, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:38.593321 2023] [cgid:error] [pid 30906:tid 124702930366656] (13)Permission denied: AH01241: exec of '/srv/web/ipfire/cgi-bin/speed.cgi' failed
[Sun Nov 26 10:24:38.595911 2023] [cgid:error] [pid 31949:tid 124702672537280] [client 192.168.60.212:50076] End of script output before headers: speed.cgi, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:39.509988 2023] [cgid:error] [pid 30907:tid 124702930366656] (13)Permission denied: AH01241: exec of '/srv/web/ipfire/cgi-bin/pakfire.cgi' failed
[Sun Nov 26 10:24:39.514402 2023] [cgid:error] [pid 31949:tid 124702555104960] [client 192.168.60.212:50084] End of script output before headers: pakfire.cgi, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:40.317722 2023] [cgid:error] [pid 30908:tid 124702930366656] (13)Permission denied: AH01241: exec of '/srv/web/ipfire/cgi-bin/speed.cgi' failed
[Sun Nov 26 10:24:40.321114 2023] [cgid:error] [pid 31949:tid 124702680929984] [client 192.168.60.212:50090] End of script output before headers: speed.cgi, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:40.598625 2023] [cgid:error] [pid 30909:tid 124702930366656] (13)Permission denied: AH01241: exec of '/srv/web/ipfire/cgi-bin/pakfire.cgi' failed
[Sun Nov 26 10:24:40.606648 2023] [cgid:error] [pid 31949:tid 124702697715392] [client 192.168.60.212:50095] End of script output before headers: pakfire.cgi, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:40.648084 2023] [cgid:error] [pid 30910:tid 124702930366656] (13)Permission denied: AH01241: exec of '/srv/web/ipfire/cgi-bin/speed.cgi' failed
[Sun Nov 26 10:24:40.651488 2023] [cgid:error] [pid 31949:tid 124702913717952] [client 192.168.60.212:50094] End of script output before headers: speed.cgi, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:41.722693 2023] [cgid:error] [pid 30911:tid 124702930366656] (13)Permission denied: AH01241: exec of '/srv/web/ipfire/cgi-bin/pakfire.cgi' failed
[Sun Nov 26 10:24:41.726014 2023] [cgid:error] [pid 31949:tid 124702664144576] [client 192.168.60.212:50106] End of script output before headers: pakfire.cgi, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:42.384684 2023] [cgid:error] [pid 30912:tid 124702930366656] (13)Permission denied: AH01241: exec of '/srv/web/ipfire/cgi-bin/speed.cgi' failed
[Sun Nov 26 10:24:42.386831 2023] [cgid:error] [pid 31949:tid 124702689322688] [client 192.168.60.212:50113] End of script output before headers: speed.cgi, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:42.601752 2023] [cgid:error] [pid 30913:tid 124702930366656] (13)Permission denied: AH01241: exec of '/srv/web/ipfire/cgi-bin/speed.cgi' failed
[Sun Nov 26 10:24:42.604590 2023] [cgid:error] [pid 31949:tid 124702789969600] [client 192.168.60.212:50115] End of script output before headers: speed.cgi, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:42.853641 2023] [cgid:error] [pid 30914:tid 124702930366656] (13)Permission denied: AH01241: exec of '/srv/web/ipfire/cgi-bin/pakfire.cgi' failed
[Sun Nov 26 10:24:42.855652 2023] [cgid:error] [pid 31949:tid 124702655751872] [client 192.168.60.212:50117] End of script output before headers: pakfire.cgi, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:44.112308 2023] [cgid:error] [pid 30915:tid 124702930366656] (13)Permission denied: AH01241: exec of '/srv/web/ipfire/cgi-bin/pakfire.cgi' failed
[Sun Nov 26 10:24:44.114450 2023] [cgid:error] [pid 31949:tid 124702815147712] [client 192.168.60.212:50126] End of script output before headers: pakfire.cgi, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:44.278682 2023] [cgid:error] [pid 30916:tid 124702930366656] (13)Permission denied: AH01241: exec of '/srv/web/ipfire/cgi-bin/speed.cgi' failed
[Sun Nov 26 10:24:44.281159 2023] [cgid:error] [pid 31949:tid 124702672537280] [client 192.168.60.212:50130] End of script output before headers: speed.cgi, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:45.339707 2023] [cgid:error] [pid 30917:tid 124702930366656] (13)Permission denied: AH01241: exec of '/srv/web/ipfire/cgi-bin/pakfire.cgi' failed
[Sun Nov 26 10:24:45.342195 2023] [cgid:error] [pid 31949:tid 124702555104960] [client 192.168.60.212:50135] End of script output before headers: pakfire.cgi, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:46.494860 2023] [core:error] [pid 31949:tid 124702697715392] (13)Permission denied: [client 192.168.60.212:50144] AH00035: access to /cgi-bin/speed.cgi denied (filesystem path '/srv/web') because search permissions are missing on a component of the path, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:46.583137 2023] [core:error] [pid 31949:tid 124702913717952] (13)Permission denied: [client 192.168.60.212:50145] AH00035: access to /cgi-bin/pakfire.cgi denied (filesystem path '/srv/web') because search permissions are missing on a component of the path, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:47.627709 2023] [core:error] [pid 31949:tid 124702823540416] (13)Permission denied: [client 192.168.60.212:50144] AH00035: access to /cgi-bin/pakfire.cgi denied (filesystem path '/srv/web') because search permissions are missing on a component of the path, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:48.166043 2023] [core:error] [pid 31949:tid 124702798362304] (13)Permission denied: [client 192.168.60.212:50144] AH00035: access to /cgi-bin/speed.cgi denied (filesystem path '/srv/web') because search permissions are missing on a component of the path, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:48.635594 2023] [core:error] [pid 31949:tid 124702664144576] (13)Permission denied: [client 192.168.60.212:50144] AH00035: access to /cgi-bin/pakfire.cgi denied (filesystem path '/srv/web') because search permissions are missing on a component of the path, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:49.641482 2023] [core:error] [pid 31949:tid 124702689322688] (13)Permission denied: [client 192.168.60.212:50144] AH00035: access to /cgi-bin/pakfire.cgi denied (filesystem path '/srv/web') because search permissions are missing on a component of the path, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:50.167054 2023] [core:error] [pid 31949:tid 124702563497664] (13)Permission denied: [client 192.168.60.212:50144] AH00035: access to /cgi-bin/speed.cgi denied (filesystem path '/srv/web') because search permissions are missing on a component of the path, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:50.653669 2023] [core:error] [pid 31949:tid 124702781576896] (13)Permission denied: [client 192.168.60.212:50144] AH00035: access to /cgi-bin/pakfire.cgi denied (filesystem path '/srv/web') because search permissions are missing on a component of the path, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:51.757655 2023] [core:error] [pid 31949:tid 124702789969600] (13)Permission denied: [client 192.168.60.212:50144] AH00035: access to /cgi-bin/pakfire.cgi denied (filesystem path '/srv/web') because search permissions are missing on a component of the path, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:52.167593 2023] [core:error] [pid 31949:tid 124702655751872] (13)Permission denied: [client 192.168.60.212:50144] AH00035: access to /cgi-bin/speed.cgi denied (filesystem path '/srv/web') because search permissions are missing on a component of the path, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:52.853145 2023] [core:error] [pid 31949:tid 124702806755008] (13)Permission denied: [client 192.168.60.212:50144] AH00035: access to /cgi-bin/pakfire.cgi denied (filesystem path '/srv/web') because search permissions are missing on a component of the path, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:53.858357 2023] [core:error] [pid 31949:tid 124702831933120] (13)Permission denied: [client 192.168.60.212:50144] AH00035: access to /cgi-bin/pakfire.cgi denied (filesystem path '/srv/web') because search permissions are missing on a component of the path, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:54.167573 2023] [core:error] [pid 31949:tid 124702815147712] (13)Permission denied: [client 192.168.60.212:50144] AH00035: access to /cgi-bin/speed.cgi denied (filesystem path '/srv/web') because search permissions are missing on a component of the path, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:54.807291 2023] [core:error] [pid 31949:tid 124702672537280] (13)Permission denied: [client 192.168.60.212:50144] AH00035: access to /cgi-bin/speed.cgi denied (filesystem path '/srv/web') because search permissions are missing on a component of the path, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:54.893635 2023] [core:error] [pid 31949:tid 124702555104960] (13)Permission denied: [client 192.168.60.212:50144] AH00035: access to /cgi-bin/pakfire.cgi denied (filesystem path '/srv/web') because search permissions are missing on a component of the path, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:55.899087 2023] [core:error] [pid 31949:tid 124702680929984] (13)Permission denied: [client 192.168.60.212:50144] AH00035: access to /cgi-bin/pakfire.cgi denied (filesystem path '/srv/web') because search permissions are missing on a component of the path, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:56.168198 2023] [core:error] [pid 31949:tid 124702697715392] (13)Permission denied: [client 192.168.60.212:50144] AH00035: access to /cgi-bin/speed.cgi denied (filesystem path '/srv/web') because search permissions are missing on a component of the path, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:56.904659 2023] [core:error] [pid 31949:tid 124702913717952] (13)Permission denied: [client 192.168.60.212:50144] AH00035: access to /cgi-bin/pakfire.cgi denied (filesystem path '/srv/web') because search permissions are missing on a component of the path, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:57.923912 2023] [core:error] [pid 31949:tid 124702823540416] (13)Permission denied: [client 192.168.60.212:50144] AH00035: access to /cgi-bin/pakfire.cgi denied (filesystem path '/srv/web') because search permissions are missing on a component of the path, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:58.168720 2023] [core:error] [pid 31949:tid 124702798362304] (13)Permission denied: [client 192.168.60.212:50144] AH00035: access to /cgi-bin/speed.cgi denied (filesystem path '/srv/web') because search permissions are missing on a component of the path, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:58.929592 2023] [core:error] [pid 31949:tid 124702664144576] (13)Permission denied: [client 192.168.60.212:50144] AH00035: access to /cgi-bin/pakfire.cgi denied (filesystem path '/srv/web') because search permissions are missing on a component of the path, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:24:59.935664 2023] [core:error] [pid 31949:tid 124702689322688] (13)Permission denied: [client 192.168.60.212:50144] AH00035: access to /cgi-bin/pakfire.cgi denied (filesystem path '/srv/web') because search permissions are missing on a component of the path, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:25:00.176601 2023] [core:error] [pid 31949:tid 124702563497664] (13)Permission denied: [client 192.168.60.212:50144] AH00035: access to /cgi-bin/speed.cgi denied (filesystem path '/srv/web') because search permissions are missing on a component of the path, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:25:00.941561 2023] [core:error] [pid 31949:tid 124702789969600] (13)Permission denied: [client 192.168.60.212:50144] AH00035: access to /cgi-bin/pakfire.cgi denied (filesystem path '/srv/web') because search permissions are missing on a component of the path, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:25:01.994318 2023] [core:error] [pid 31949:tid 124702655751872] (13)Permission denied: [client 192.168.60.212:50144] AH00035: access to /cgi-bin/pakfire.cgi denied (filesystem path '/srv/web') because search permissions are missing on a component of the path, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:25:02.170727 2023] [core:error] [pid 31949:tid 124702806755008] (13)Permission denied: [client 192.168.60.212:50144] AH00035: access to /cgi-bin/speed.cgi denied (filesystem path '/srv/web') because search permissions are missing on a component of the path, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:25:03.000844 2023] [core:error] [pid 31949:tid 124702831933120] (13)Permission denied: [client 192.168.60.212:50144] AH00035: access to /cgi-bin/pakfire.cgi denied (filesystem path '/srv/web') because search permissions are missing on a component of the path, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:25:04.007389 2023] [core:error] [pid 31949:tid 124702815147712] (13)Permission denied: [client 192.168.60.212:50144] AH00035: access to /cgi-bin/pakfire.cgi denied (filesystem path '/srv/web') because search permissions are missing on a component of the path, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:25:04.171105 2023] [core:error] [pid 31949:tid 124702672537280] (13)Permission denied: [client 192.168.60.212:50144] AH00035: access to /cgi-bin/speed.cgi denied (filesystem path '/srv/web') because search permissions are missing on a component of the path, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:25:05.040621 2023] [core:error] [pid 31949:tid 124702555104960] (13)Permission denied: [client 192.168.60.212:50144] AH00035: access to /cgi-bin/pakfire.cgi denied (filesystem path '/srv/web') because search permissions are missing on a component of the path, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:25:06.046836 2023] [core:error] [pid 31949:tid 124702680929984] (13)Permission denied: [client 192.168.60.212:50144] AH00035: access to /cgi-bin/pakfire.cgi denied (filesystem path '/srv/web') because search permissions are missing on a component of the path, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:25:06.171916 2023] [core:error] [pid 31949:tid 124702697715392] (13)Permission denied: [client 192.168.60.212:50144] AH00035: access to /cgi-bin/speed.cgi denied (filesystem path '/srv/web') because search permissions are missing on a component of the path, referer: https://ipfire.localdomain:444/
[Sun Nov 26 10:25:19.398723 2023] [mpm_event:notice] [pid 3838:tid 124702930366656] AH00494: SIGHUP received. Attempting to restart
[Sun Nov 26 10:25:20.785820 2023] [ssl:warn] [pid 3838:tid 124702930366656] AH01882: Init: this version of mod_ssl was compiled against a newer library (OpenSSL 3.1.4 24 Oct 2023, version currently loaded is OpenSSL 3.1.2 1 Aug 2023) - may result in undefined or erroneous behavior
[Sun Nov 26 10:25:20.807057 2023] [mpm_event:notice] [pid 3838:tid 124702930366656] AH00489: Apache/2.4.57 (Unix) OpenSSL/3.1.2 configured -- resuming normal operations
[Sun Nov 26 10:25:20.807202 2023] [core:notice] [pid 3838:tid 124702930366656] AH00094: Command line: '/usr/sbin/httpd'
After the Apache stops and starts the pakfire came back and gave me the An update requires a restart! message. And it looks like the 181 updated completed.
EDIT: there seems to me lots of permission denied errors in the above logs…
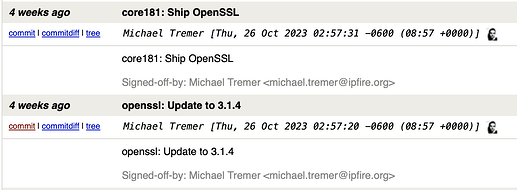
EDIT2: and an odd OpenSSL message at the bottom of log…
Ha! the OpenSSL message includes the statement “may result in undefined or erroneous behavior” and this definitely applies! 
EDIT3: I saw there were updates to OpenSSL in CU 181 but I have no ideal if this is related to the original issue: