I assume that your RED interface is getting a public IP address.
If you insist on staying with the GREEN netmask of 255.255.0.0 (which with 40 devices is not necessary) I suggest you change the BLUE address to a different private address.
If your GREEN range is 192.168.0.0 -192.168.255.255
Then the IP address ranges for the BLUE network should be
10.0.0.0 -10.255.255.255
or
172.16.0.0 -172.31.255.255
And I think that if there are no other needs and the number of devices in the network is less than 254, it is more practical to use a mask of 255.255.255.0
edit:
I made a quick test on the VM
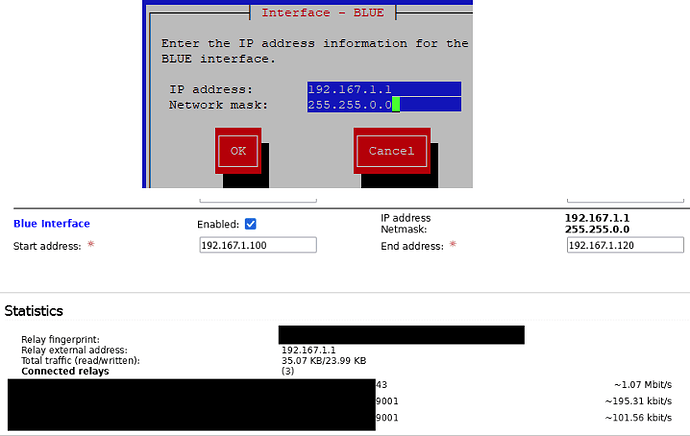
Below BLUE has IP address 192.167.1.1/255.255.0.0
effect - “Relay external address” has the address 192.167.1.1
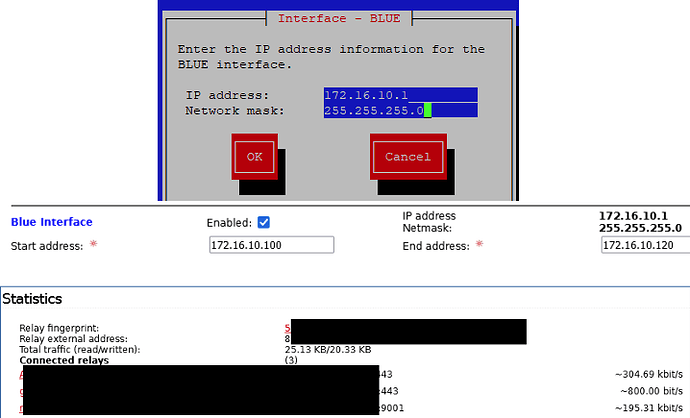
Below BLUE has IP address 172.16.10.1/255.255.255.0
effect - “Relay external address” has a public address