You are going to want to use the correct gateway address on RED and GREEN.
RED gateway is probably your Fritzbox ip look at WORKstation network setup.
Green 109.168.55.* subnet 255.255.255.0 can change this. DHCP range 192.168.55.100-150
well need to log in to WUI to make changes and add firewall rules.
From WUI set server ip to Something out side of the DHCP range. Like 192.168.55.50
Your server sould be able to reach the internet.
If this is not desired. Change default firewall rules to block.
you will need fire wall rules to allow traffic in all directions.!
like an rule to allow workstation to reach server.
Thank you for your help and patience with me…
I don’t get it, I’m desperate. I’ve attached a screenshot of the firewall.
Well, it’s really easy for me
made with the connection:
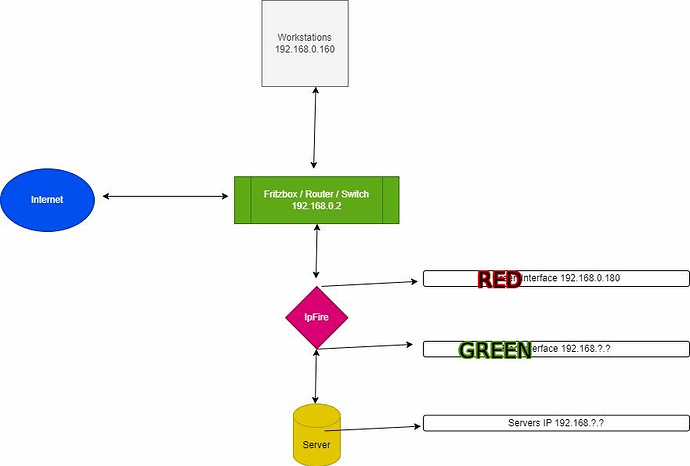
1 workstation, from which an Ethernet cable goes to the green interface of the firewall. The workstation has the 192.168.0.100 - 255.255.255.0
Green interface 192.168.0.180 - 255.255.255.0
A cable goes out of the firewall via the orange interface on the server. The server has the IP 192.168.0.170 - 255.255.255.0
Orange interface 192.168.50.181 - 255.255.0.0
A cable goes via the red interface to the Fritzbox/router. The Fritzbox has the address 192.168.0.2 - 255.255.255.0
Red interface - 192.168.1.1 - 255.255.255.0
I cannot access the server from the workstation and have not created a firewall rule.


Your Network Topography is a moving target.
Your getting closer. but a new diagram is in order.
I have to ask. What is your end goal?
Problems I see.
IPfire WAN / RED zone IP is not in the correct subnet
If connected to Fritzbox Should be something like 192.168.0.200
Which means Green zone should be different like 192.168.1.*
When you interpose an IPFire, then you need to change the network addresses used for Green & Orange.
You will need to have Red0 on network 192.168.0.0/24, for compatibility with Fritzbox. (say) 192.168.0.10 for Red0. I would avoid 192.168.0.1, in case it is already assigned by the router.
Green0, workstations and server could be on 192.168.1.0/24. So Green0 could be (say) 192.168.1.180. If the server is not accessible from the Internet then put it on 192.168.1.0/24 too.
You would find it much easier if you had initiated DHCP for Green, when installing IPFire, and set the workstations for DHCP.
Hello folks,
I don’t think I get it, I’m too stupid for that ![]()
I recorded again what it should roughly look like. I used the IP addresses in the drawing as well as in Ipfire. I can’t ping the server when I log in to the IPFire via SSh.
You will have to move the workstations from the Fritzbox. Only red0 should connect directly to the Fritzbox. Red interface must be connected for IPFire to work.
If you don’t have a separate Ethernet switch, then simply connect one workstation to green interface initially. You need to depict the second, separate switch, for the diagram to make sense.
Don’t bother with the Orange interface, initially. You can add that after you get the basics working.
![]() Do workstations need to be in this segment of the network?
Do workstations need to be in this segment of the network?

Okay, then I’ll connect it like that.
So I MUST connect the red interface, regardless of whether I need internet or not?
I can’t just block/control the traffic between the orange and the green?
Thank you for your time…
Have you read the following IPFire Wiki pages?
edit:
I hope the following example clarifies looking at your case.
No, not yet, but maybe I should look into it before I write any more here ![]()
Thank you very much for the picture…I will try it as quickly as possible in the next few days and get back to you immediately.
Thank you for your time and support
So I created the image like that and lo and behold it works great.
Could it be that the error was with the gateway? I didn’t enter them into the workstations and servers.
Now I can test test test :-)))
Thank you for all the help and your time…
greeting
Hello folks,
Now that I’m slowly understanding it better, I need your professional advice again.
I have recorded two examples of how I would like to set up my networks.
What must definitely be the case is that the servers can make a backup of each other. I think example 2 would be better.
But my concern would be that in Example 2 the Raspberry would not be able to manage traffic. The orange and red interfaces are powered by USB Ethernet. What do you all mean ?
If the IpFire PC were strong enough, is example 2 better?
greeting
Sasha
Example 2 would not be recommended, because Orange network has less protection than Green or Blue. You could move the Business network to Blue interface in Example 2, to get better protection. You would then need to create blue-green pinhole
Example 1 would be a better choice. However, it would require a VPN, in order to synchronise the servers.
Whether or not Raspberry Pi would handle the traffic would depend on:
- version of RPi
- amount of traffic
- reliability required, because USB-Ethernet devices have occasionally had “issues”
Thanks for the tip,
what exactly do you mean by “blue-green pinhole”? Isn’t there something between orange and green?
Can you briefly explain to me why the blue one is more safe? I thought the blue one was mostly WIFI?
So I think the VPN would be feasible.
Yes, I had already thought about the USB. I would then have to get a PC with 3-4 Ethernet interfaces. The Raspberry PI is from 2018 with 8 GB RAM, the traffic in the business network is very low. But higher in the private sector.
Let’s see how I do it. Quick question about the VPN: It is set up in both Ipfire devices, right?
greeting
Orange interface is intended for publicly accessible servers and has to be more “open”
Blue interface is a separate, protected LAN. Although many use it for WiFi, it could be used for wired LAN.
I don’t know much about VPN and can’t answer your question there.
The only way to assess performance & reliablity of the RPi is to try them.
Thank you again for your help and your time,
I will implement it in the next few weeks and report here how it works and how the Raspberry manages it all.
I’m now looking for a PC with a little more power and that the Ethernet doesn’t run via USB.
Until then stay healthy,
greeting
Sorry for the very late reaction. I wasn’t online the last three weeks ( yes this is possible ![]() ).
).
I think the main problem in this thread isn’t the association if IPs etc. It is the network topology ( including the right connections ). The wiki articles cited give a good introduction to this topic.
In short the philosophy of IPFire ( and many other firewall routers ) is
- interface RED — WAN, the whole internet
- interface GREEN — LAN on ethernet, the place for local devices
- interface BLUE — LAN in wifi, place for wireless local devices
- interface ORANGE – DMZ, area for local servers accessible from the WAN.
These are the physical networks connected through IPFire only.
IP addresses define logical networks. These networks must be separated according to the physical topology. The connection between is done by the routing function of IPFire.
Hope this makes some things clearer.
Regards,
Bernhard
Thanks for the reply,
The more I delve into this topic the clearer it becomes.
Greetings
Hello professionals,
I have another question about a variant.
In the two examples I drew above, a telephone system would have to be used in the business network.
Does it make sense to integrate it into the Ipfire or not allow it to run over the Ipfire at all? ?
Do you have a suggestion?
greeting
Keep it on a separate device.
My 2 cents.