Why don’t you use DNSSEC for Pi-Hole? It works.
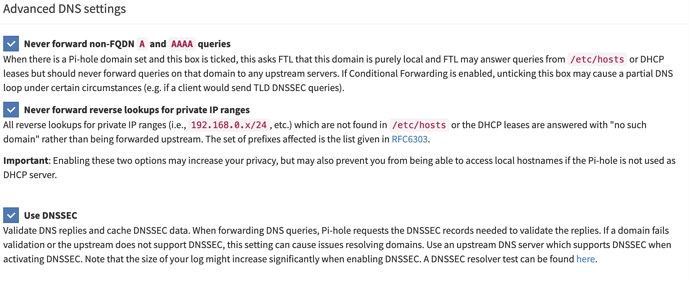
"*Use DNSSEC
Validate DNS replies and cache DNSSEC data. When forwarding DNS queries, Pi-hole requests the DNSSEC records needed to validate the replies. If a domain fails validation or the upstream does not support DNSSEC, this setting can cause issues resolving domains. Use an upstream DNS server which supports DNSSEC when activating DNSSEC. Note that the size of your log might increase significantly when enabling DNSSEC. A DNSSEC resolver test can be found here."
https://bilderupload.org/bild/234588729-bildschirmfoto-2021-10-02
EDIT: mod added image to replace link.
On the security concerns of using Pi-Hole:
See above. + I had once tried to observe which sites use DNSSEC. I have barely found some.
On the other hand, between 15 and 20 percent of queries are blocked in Pi-Hole (currently 16.7%; 8 525 305 domains on blocklist). Among them will be many trackers that compromise privacy (especially on devices where the use of blockers is restricted).
Without Pi-Hole, those would go through for the most part.
Makes me wonder which is more insecure?
In addition, you can find articles and opinions on the net that DNSSEC has failed [1]. One site has even described DNSSEC as counterproductive [2]. Even though I don’t share this opinion at the moment, I wonder if the right balance is being made here.
SquidGuard I would probably use (where possible). The problem seems to be that there are not so many and good blacklists for it. I have seen there are scripts to convert typical lists so that Squid understands them. That seems to me to involve a lot of tinkering though. And the scripts probably don’t always work or break. If I find time, I’ll take a look at it.
That was my impression after a quick research
[1] Golem.de: IT-News für Profis
[2] 14 DNS Nerds Don't Control The Internet — Quarrelsome