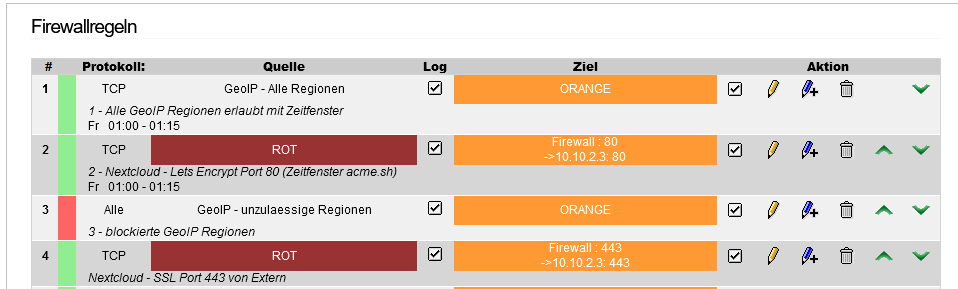
Would that make it so right here?
Rule 1
All GeoIP regions are allowed to connect to the DMZ (Orange) via TCP on Friday between 01:00 - 01:15.
2nd rule
Everyone from RED is allowed to connect to the Nextcloud server via port 80 (TCP) on Friday between 01:00 - 01:15.
3rd rule
All packets from IP addresses from the forbidden regions (except DE) will be dropped if they have the destination DMZ (Orange).
4th rule
Everything from RED on Poort 443 will be forwarded to the IP of NextCloud server.