Tested 195. Latest 194 backup didn’t work. I use Wireguard App. Tried 195 Wireguard: is Global ID page necessary when a Configuration is used.
![]()
I’m using a translator and I’m afraid I don’t understand this sentence exactly.
Could you explain more broadly?
Tom, I no longer have 195 to refer. It seems, from memory, that to get to the configuration area—I have a conf. file for a working Wireguard App—there was a first page called Global. Is filling in that page necessary to advance to the config page?
I hope the following information will be helpful to you
Today I installed IPFire CU194 on VirtualBox then switched to the test version of CU195.
After switching to the test version - CU195, a new item “WireGuard” appears in the menu.
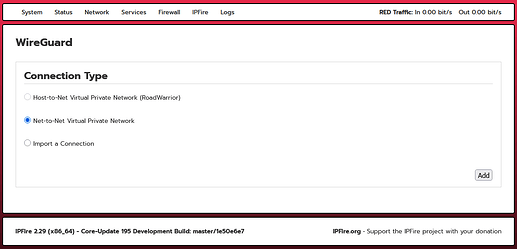
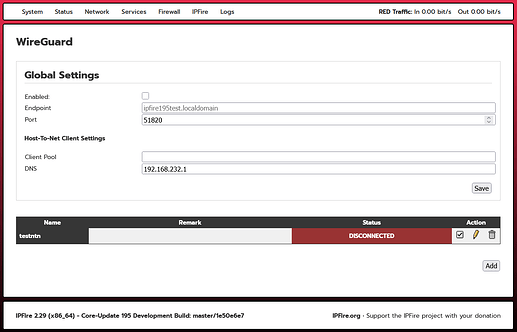
After clicking “WireGuard,” the following page opened:
After clicking the “Add” button (without filling in the fields and without checking “Enabled”), the following page opened
Only two items were active
“Net-to-Net Virtual Private Network”.
“Import a Connection”
I left “Net-to-Net Virtual Private Network” checked.
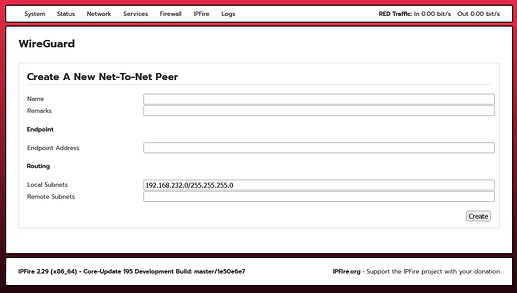
After clicking “Add” the following page opened
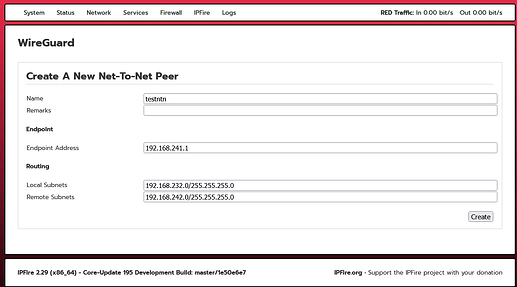
I added the test data then clicked “Create”
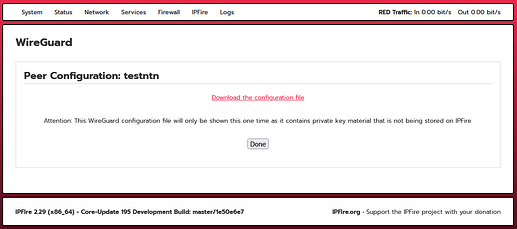
After clicking “Create,” the following page opened
I downloaded a testntn.conf file containing the following data
[Interface]
PrivateKey = [ removed ]
Port = 60881
[Peer]
Endpoint = ipfire195test.localdomain:60875
PublicKey = [ removed ]
PresharedKey = [ removed ]
AllowedIPs = 192.168.232.0/24
PersistentKeepalive = 25
After clicking “Done” the following page opened
You should never post any key material on a forum. I have removed this for you. I suppose you delete this connection as soon as possible and create a new one.
It would be nice, but this is not that straight-forward. We have to assume that people know the basics of networking and can design a flat plan.
You can rest reassured ![]()
The IPFire CU195 in this post is only a virtual test machine.
Before posting in my post:
I removed the connection configuration from this IPFire CU195.
I changed the keys before pasting into the post.
However, I completely agree that such data should not be disclosed.
Regards
Hi.
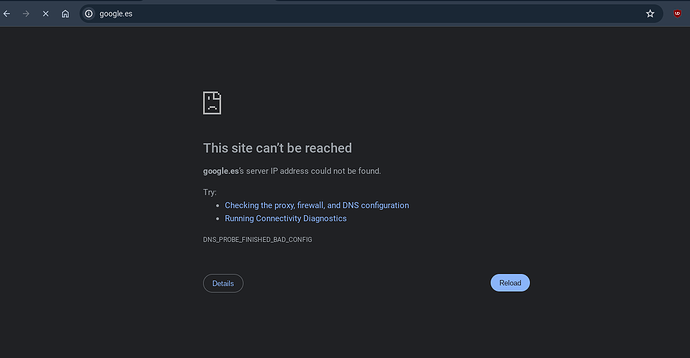
I have set up WireGuard on a Chromebook and it connects correctly, but the problem I have is that once connected, I cannot browse the internet anywhere.
I also don’t have access to any resources found in the IPFire Green interface.
The funny thing is, I have an Android phone with WireGuard, and everything works perfectly by following the same steps.
Is this happening to anyone else?
Saludos.
Hi again.
Well, after testing, I restarted the Chromebook and it started working. So, I consider it fixed.
Saludos y gracias.
Repeated the upgrade from CU194 to CU195 Testing, via WUI, on virtual machine. Went smoothly and build 1e50e6e7 is running OK.
Hi, i switched back to ipfire, because of the newly added wireguard support. It works great, but i get multiple of these per day
13:44:28 kernel: ==================================================================
13:44:28 kernel: BUG: KFENCE: use-after-free read in ipt_do_table+0x1b9/0x7d0
13:44:28 kernel:
13:44:28 kernel: Use-after-free read at 0x00000000cb4559ce (in kfence-#227):
13:44:28 kernel: ipt_do_table+0x1b9/0x7d0
13:44:28 kernel: nf_hook_slow+0x42/0x120
13:44:28 kernel: ip_output+0x126/0x1f0
13:44:28 kernel: ip_sublist_rcv+0x335/0x350
13:44:28 kernel: ip_list_rcv+0x130/0x170
13:44:28 kernel: __netif_receive_skb_list_core+0x2c8/0x2f0
13:44:28 kernel: netif_receive_skb_list_internal+0x1b6/0x300
13:44:28 kernel: napi_complete_done+0x72/0x230
13:44:28 kernel: wg_packet_rx_poll+0x40c/0x8e0 [wireguard]
13:44:28 kernel: __napi_poll+0x28/0x170
13:44:28 kernel: net_rx_action+0x323/0x410
13:44:28 kernel: handle_softirqs+0xf9/0x2d0
13:44:28 kernel: run_ksoftirqd+0x45/0x50
13:44:28 kernel: smpboot_thread_fn+0x188/0x230
13:44:28 kernel: kthread+0xde/0x110
13:44:28 kernel: ret_from_fork+0x31/0x50
13:44:28 kernel: ret_from_fork_asm+0x1a/0x30
13:44:28 kernel:
13:44:28 kernel: kfence-#227: 0x00000000ae01ff22-0x00000000ea544824, size=2048, cache=kmalloc-rnd-12-2k
13:44:28 kernel:
13:44:28 kernel: allocated by task 15100 on cpu 1 at 512417.565579s (0.000127s ago):
13:44:28 kernel: kmalloc_reserve+0x64/0x100
13:44:28 kernel: pskb_expand_head+0x95/0x380
13:44:28 kernel: __pskb_pull_tail+0x5b/0x4d0
13:44:28 kernel: skb_cow_data+0x77/0x320
13:44:28 kernel: decrypt_packet+0xd6/0x1d0 [wireguard]
13:44:28 kernel: wg_packet_decrypt_worker+0x66/0x1b0 [wireguard]
13:44:28 kernel: process_one_work+0x174/0x330
13:44:28 kernel: worker_thread+0x266/0x3a0
13:44:28 kernel: kthread+0xde/0x110
13:44:28 kernel: ret_from_fork+0x31/0x50
13:44:28 kernel: ret_from_fork_asm+0x1a/0x30
13:44:28 kernel:
13:44:28 kernel: freed by task 28 on cpu 1 at 512417.565609s (0.000131s ago):
13:44:28 kernel: pskb_expand_head+0x1d2/0x380
13:44:28 kernel: __pskb_pull_tail+0x5b/0x4d0
13:44:28 kernel: match+0x18c/0x6e0 [xt_layer7]
13:44:28 kernel: ipt_do_table+0x2c5/0x7d0
13:44:28 kernel: nf_hook_slow+0x42/0x120
13:44:28 kernel: ip_output+0x126/0x1f0
13:44:28 kernel: ip_sublist_rcv+0x335/0x350
13:44:28 kernel: ip_list_rcv+0x130/0x170
13:44:28 kernel: __netif_receive_skb_list_core+0x2c8/0x2f0
13:44:28 kernel: netif_receive_skb_list_internal+0x1b6/0x300
13:44:28 kernel: napi_complete_done+0x72/0x230
13:44:28 kernel: wg_packet_rx_poll+0x40c/0x8e0 [wireguard]
13:44:28 kernel: __napi_poll+0x28/0x170
13:44:28 kernel: net_rx_action+0x323/0x410
13:44:28 kernel: handle_softirqs+0xf9/0x2d0
13:44:28 kernel: run_ksoftirqd+0x45/0x50
13:44:28 kernel: smpboot_thread_fn+0x188/0x230
13:44:28 kernel: kthread+0xde/0x110
13:44:28 kernel: ret_from_fork+0x31/0x50
13:44:28 kernel: ret_from_fork_asm+0x1a/0x30
13:44:28 kernel:
13:44:28 kernel: CPU: 1 UID: 0 PID: 28 Comm: ksoftirqd/1 Tainted: G B 6.12.23-ipfire #1
13:44:28 kernel: Tainted: [B]=BAD_PAGE
13:44:28 kernel: Hardware name: Default string Default string/Default string, BIOS 5.27 11/21/2024
13:44:28 kernel: ==================================================================
Hi Eric,
Welcome to the IPFire community! It’s great that the new WireGuard support (still in testing) brought you back to IPFire.
Those kernel errors you’re seeing look like they might be tied to how your Quality of Service (QoS) rules are handling WireGuard traffic. In particular, if you’re using a non-standard port for WireGuard, it could be causing a conflict with QoS’s protocol inspection.
To help figure this out, could you share a couple of details?
- In the WireGuard global settings what port are you using? The default is 51820, but if you’ve picked something else, that’s key info.
- Via IPFire’s console or SSH, please run this command and paste the output here:
This shows your QoS rules and is safe to share.cat /var/ipfire/qos/classes /var/ipfire/qos/level7config /var/ipfire/qos/portconfig /var/ipfire/qos/tosconfig
If the errors are causing crashes or slowdowns, you could try disabling QoS temporarily to see if they stop, which would confirm QoS is the issue.
Cheers,
A G
Hi Adam,
thanks for your fast and detailed reply.
- I did not change the default port. Port 51820 is displayed in global WireGuard settings.
- These are my QoS rules. I removed all but the default classes.
[root@ipfire ~]# cat /var/ipfire/qos/classes /var/ipfire/qos/level7config /var/ipfire/qos/portconfig /var/ipfire/qos/tosconfig
red0;110;1;1;50000;;;;Default;
imq0;210;1;1;920000;;;;Default;
102;red0;dns;;;
102;red0;rtp;;;
102;red0;skypetoskype;;;
103;red0;ssh;;;
103;red0;rdp;;;
104;red0;http;;;
104;red0;ssl;;;
104;red0;pop3;;;
120;red0;applejuice;;;
120;red0;bittorrent;;;
200;imq0;rtp;;;
200;imq0;skypetoskype;;;
203;imq0;ssh;;;
203;imq0;rdp;;;
204;imq0;http;;;
204;imq0;pop3;;;
204;imq0;ssl;;;
220;imq0;applejuice;;;
220;imq0;bittorrent;;;
101;red0;icmp;;;;;
102;red0;tcp;;;;53;
102;red0;udp;;;;53;
103;red0;esp;;;;;
103;red0;tcp;;1194;;;
103;red0;udp;;1194;;;
103;red0;tcp;;;;1194;
103;red0;udp;;;;1194;
103;red0;udp;;4500;;4500;
103;red0;udp;;500;;500;
104;red0;tcp;;;;80;
200;imq0;icmp;;;;;
203;imq0;esp;;;;;
203;imq0;tcp;;;;1194;
203;imq0;udp;;;;1194;
203;imq0;tcp;;1194;;;
203;imq0;udp;;1194;;;
203;imq0;udp;;4500;;4500;
203;imq0;udp;;500;;500;
204;imq0;tcp;;80;;;
So far these errors didn’t cause any disruption.
This type of fault message has been reported before.
https://community.ipfire.org/t/bug-kfence-use-after-free-read-in-ipt-do-t/6888
At that time it was due to a nic driver problem in the kernel which was fixed in a subsequent kernel update.
Maybe a similar type of issue for you. I have not compared the two sets of log messages in detail as i don’t have the time currently but the top level error message was the same.
Thanks, Adolf! I think Erik’s issue might be similar, likely a kernel bug.
Erik, while waiting for a fix, test disabling QoS, see if that stops the error.
Thanks,
A G
Thanks to @ms for backporting the following patch which we just missed in the 6.12 kernel
A free 15% performance boost in TCP stream speeds over WireGuard? We’ll take it!
The patch was recently mentioned on Phoronix too.
Hopefully this should be included in Core Update 196.
Cheers,
A G
Hi.
I don’t know whether to post this here or in a new thread. I’m posting it here since it’s a “beta” version.
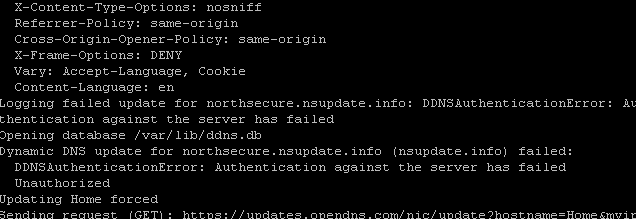
I went to update the DDNS secret key “nsupdate.info” and, after modifying it from the GUI, it didn’t change the “ddns.conf” file. I had to change it manually.
The error I got was:
I had to copy/paste the new key into this configuration file.
Is this happening to anyone else? Maybe it’s just me.
Best regards.
I just tested this on my vm system with CU195 Testing. With English selected it worked fine.
I then changed to Spanish and had the problem you describe.
I then changed the es.pl file to the one I created earlier today with my patch submission and it worked again.
So I am afraid it is the same problem as with the Location Groups on the Firewall Groups menu but the good news is that the patch I submitted earlier today will also fix that issue.
There could well be other WUI pages that will have the same problem but all of those will get fixed by the patch to the Spanish lang file.
Hello Adolf.
Could you post the compressed es.pl file here so we can copy it?
Thanks for everything.
Greetings from Spain.
es.pl.tar.xz (42.9 KB)
Here is the Spanish language file with the patch changes applied to it.
After you copy bthat file to the /var/ipfire/langs/ directory you need to run the command
update-lang-cache so that the language caches are updated with the new file you add.
If you don’t do that then the old strings will still be used until a reboot is carried out.