trish
(trish)
4
Thank you Peter,
Oh yes almost every Wordpress website is using Cloudflare.
I see these fellows are thinking about a similar idea,
@mutley created a script that can do CNAME inspection:
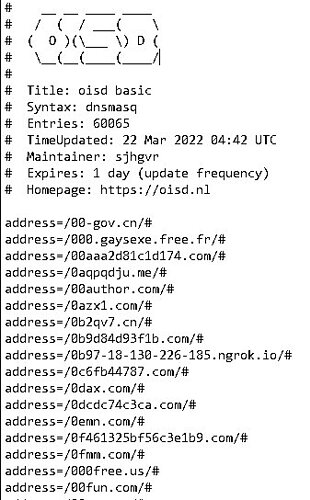
I wonder if this would help. This list is being updated every morning at 5:00 UTC
https://hosts.oisd.nl/basic/ with 60000 domains
or even the full list
https://hosts.oisd.nl/ with 1.8 million domains
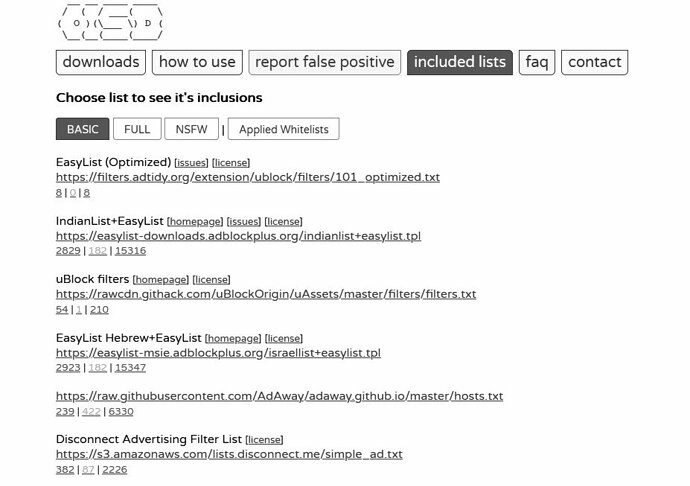
If anyone is interested, here are some partial screenshots regarding the list: