Hi all,
may a little OT even it is not available via Pakfire but i tried to get an Wazuh agent ready for IPFire whereby the Manager works on a CentOS VM even on a headless platform it was a fast setup.
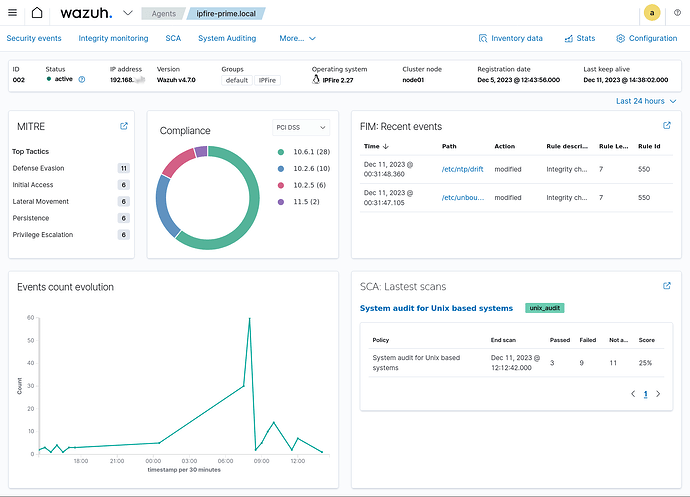
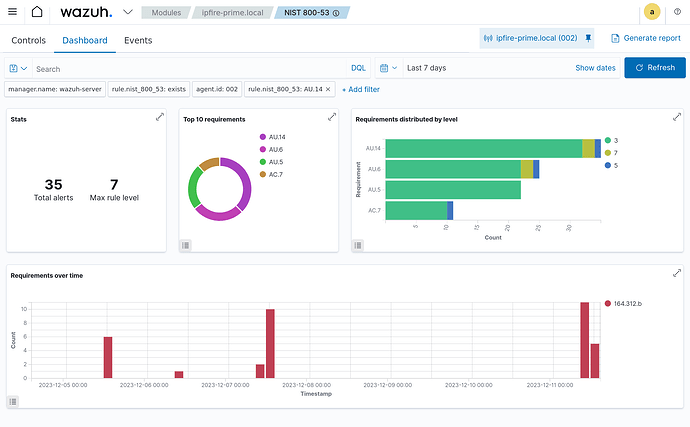
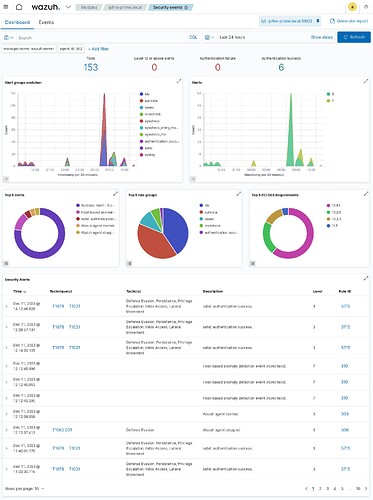
The results are nice even with default settings and a platform (IPFire) which is not known in Wazuh.
← just a little overview of much more available…
And it even like Suricata´s eve.json logs… But am not sure if this makes sense for you and for sure for the IPFire dev´s opinion
Best,
Erik