Hello @jon
Thank you so much 
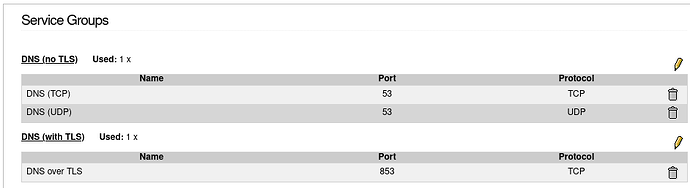
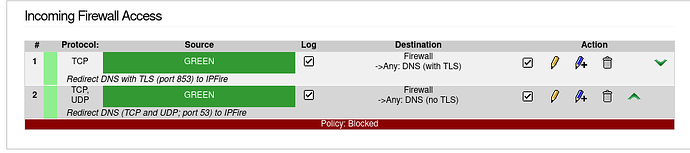
I deactivated the firewall rule for DoT, applied the change. Then disabled Cloudflare’s DNS servers.
Here’s a test I ran (command and result):
$ echo | openssl s_client -connect '1.1.1.1:853'
CONNECTED(00000003)
Can't use SSL_get_servername
depth=2 C = US, O = DigiCert Inc, OU = www.digicert.com, CN = DigiCert Global Root CA
verify return:1
depth=1 C = US, O = DigiCert Inc, CN = DigiCert TLS Hybrid ECC SHA384 2020 CA1
verify return:1
depth=0 C = US, ST = California, L = San Francisco, O = "Cloudflare, Inc.", CN = cloudflare-dns.com
verify return:1
---
Certificate chain
0 s:C = US, ST = California, L = San Francisco, O = "Cloudflare, Inc.", CN = cloudflare-dns.com
i:C = US, O = DigiCert Inc, CN = DigiCert TLS Hybrid ECC SHA384 2020 CA1
a:PKEY: id-ecPublicKey, 256 (bit); sigalg: ecdsa-with-SHA384
v:NotBefore: Jan 12 00:00:00 2023 GMT; NotAfter: Jan 11 23:59:59 2024 GMT
1 s:C = US, O = DigiCert Inc, CN = DigiCert TLS Hybrid ECC SHA384 2020 CA1
i:C = US, O = DigiCert Inc, OU = www.digicert.com, CN = DigiCert Global Root CA
a:PKEY: id-ecPublicKey, 384 (bit); sigalg: RSA-SHA384
v:NotBefore: Apr 14 00:00:00 2021 GMT; NotAfter: Apr 13 23:59:59 2031 GMT
---
Server certificate
-----BEGIN CERTIFICATE-----
MIIF9TCCBXygAwIBAgIQA8JqRlvV7Wjej2b5dc4uXzAKBggqhkjOPQQDAzBWMQsw
CQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMTAwLgYDVQQDEydEaWdp
Q2VydCBUTFMgSHlicmlkIEVDQyBTSEEzODQgMjAyMCBDQTEwHhcNMjMwMTEyMDAw
MDAwWhcNMjQwMTExMjM1OTU5WjByMQswCQYDVQQGEwJVUzETMBEGA1UECBMKQ2Fs
aWZvcm5pYTEWMBQGA1UEBxMNU2FuIEZyYW5jaXNjbzEZMBcGA1UEChMQQ2xvdWRm
bGFyZSwgSW5jLjEbMBkGA1UEAxMSY2xvdWRmbGFyZS1kbnMuY29tMFkwEwYHKoZI
zj0CAQYIKoZIzj0DAQcDQgAE8WA8mNsEQxx1/IvfcBNZj/HOWGEFoHH5gLTJQ+mD
iQ3+ItaqCY7TT+R/picYF5ljVow7R7jn6iCxMFkVjXChG6OCBA4wggQKMB8GA1Ud
IwQYMBaAFAq8CCkXjKU5bXoOzjPHLrPt+8N6MB0GA1UdDgQWBBRkutjX+1Qhhwjz
soJm+Z5fS3AE8jCBpgYDVR0RBIGeMIGbghJjbG91ZGZsYXJlLWRucy5jb22CFCou
Y2xvdWRmbGFyZS1kbnMuY29tgg9vbmUub25lLm9uZS5vbmWHBAEAAAGHBAEBAQGH
BKKfJAGHBKKfLgGHECYGRwBHAAAAAAAAAAAAEAGHECYGRwBHAAAAAAAAAAAAERGH
ECYGRwBHAAAAAAAAAAAAAGSHECYGRwBHAAAAAAAAAAAAZAAwDgYDVR0PAQH/BAQD
AgeAMB0GA1UdJQQWMBQGCCsGAQUFBwMBBggrBgEFBQcDAjCBmwYDVR0fBIGTMIGQ
MEagRKBChkBodHRwOi8vY3JsMy5kaWdpY2VydC5jb20vRGlnaUNlcnRUTFNIeWJy
aWRFQ0NTSEEzODQyMDIwQ0ExLTEuY3JsMEagRKBChkBodHRwOi8vY3JsNC5kaWdp
Y2VydC5jb20vRGlnaUNlcnRUTFNIeWJyaWRFQ0NTSEEzODQyMDIwQ0ExLTEuY3Js
MD4GA1UdIAQ3MDUwMwYGZ4EMAQICMCkwJwYIKwYBBQUHAgEWG2h0dHA6Ly93d3cu
ZGlnaWNlcnQuY29tL0NQUzCBhQYIKwYBBQUHAQEEeTB3MCQGCCsGAQUFBzABhhho
dHRwOi8vb2NzcC5kaWdpY2VydC5jb20wTwYIKwYBBQUHMAKGQ2h0dHA6Ly9jYWNl
cnRzLmRpZ2ljZXJ0LmNvbS9EaWdpQ2VydFRMU0h5YnJpZEVDQ1NIQTM4NDIwMjBD
QTEtMS5jcnQwCQYDVR0TBAIwADCCAX0GCisGAQQB1nkCBAIEggFtBIIBaQFnAHUA
7s3QZNXbGs7FXLedtM0TojKHRny87N7DUUhZRnEftZsAAAGFqCecuAAABAMARjBE
AiAdA/2qx7A3w0Jn7vVuS/qJjfHQURcg1UbQ4JG9wjDBXAIgYsXLQjjc4KaK6y+g
vU+HP4Ow41mj3tiDSp/6GrZCJzEAdwBIsONr2qZHNA/lagL6nTDrHFIBy1bdLIHZ
u7+rOdiEcwAAAYWoJ5zeAAAEAwBIMEYCIQCbW0qSTa+OBqRPNVxEjsAlZ7O31yxx
hRQI5t1UjU97AgIhAJJGLQBjwKVLAul//qX6KKnN/aJDzUSe+i9AeNvCU61+AHUA
O1N3dT4tuYBOizBbBv5AO2fYT8P0x70ADS1yb+H61BcAAAGFqCec6QAABAMARjBE
AiBP/2dqsY1syhBOL5tOc6a6JDzAchfFlDSd6W8DKerZ3QIgZUQUM4nYFlyMBRxn
YfTXn63X/m5ViNBrV/z1GSPzJ5IwCgYIKoZIzj0EAwMDZwAwZAIwP/iWG6Wa0U8A
dDjvbUOxXdI6WgQXwVng/Wrs2G3P2CPXyDi8y4D523XfIYDdY3KQAjA0t0mL62JA
NgpCMd3y7oOrMz01u/FQVel18mXq+PAkEYB6S+9BJOxjGcKGIEXtMxg=
-----END CERTIFICATE-----
subject=C = US, ST = California, L = San Francisco, O = "Cloudflare, Inc.", CN = cloudflare-dns.com
issuer=C = US, O = DigiCert Inc, CN = DigiCert TLS Hybrid ECC SHA384 2020 CA1
---
No client certificate CA names sent
Peer signing digest: SHA256
Peer signature type: ECDSA
Server Temp Key: X25519, 253 bits
---
SSL handshake has read 2889 bytes and written 373 bytes
Verification: OK
---
New, TLSv1.3, Cipher is TLS_AES_256_GCM_SHA384
Server public key is 256 bit
This TLS version forbids renegotiation.
Compression: NONE
Expansion: NONE
No ALPN negotiated
Early data was not sent
Verify return code: 0 (ok)
---
DONE
Out of curiosity, is there some reason you want to block DNS over TLS (DoT) with Port 853?
It was my lack of understanding. I do now have a vague idea, and that is because of yours and @cfusco’s excellent explanations in this thread; for which I am forever grateful.
Thanks,
Arslan