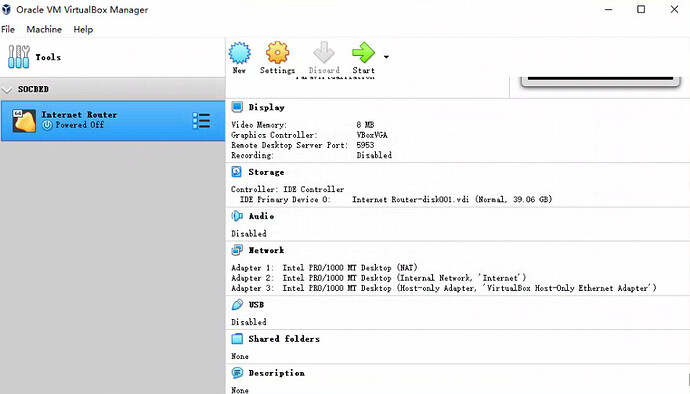
it’s automated generated by virtualbox, the internet access gateway is automated generated using nat
I am using nat as the network interface mode on my vm’s, and the red is the nat mode.
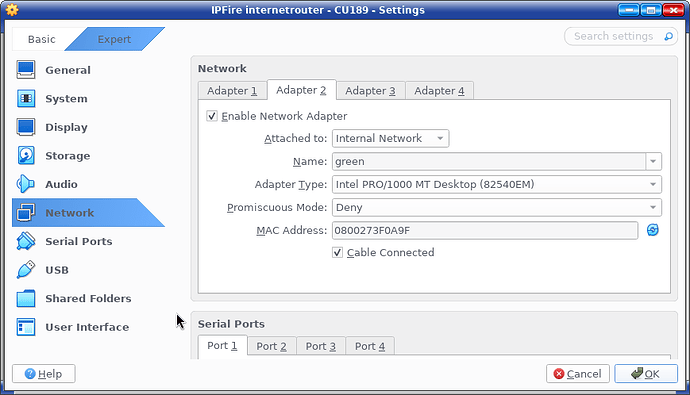
The red is using the nat adapter as below:
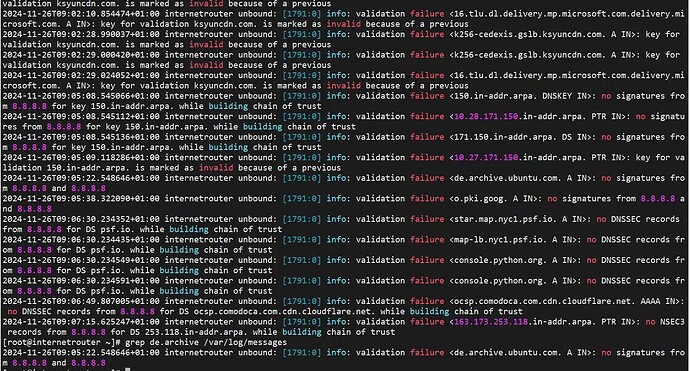
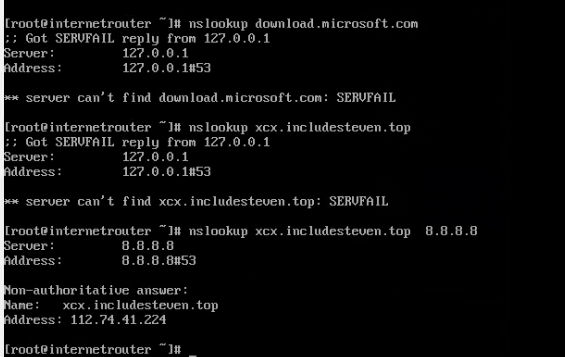
And nslookup can not work for some unusal domain as below:
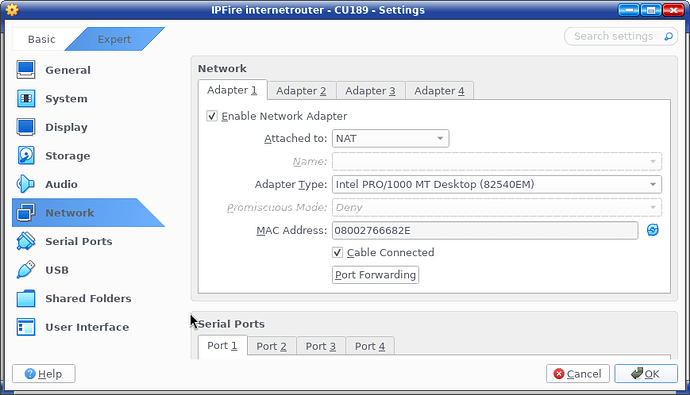
When import the ova in virtualbox, the MAC address policy should be Include all network adapter MAC addresses so that everythink worked.
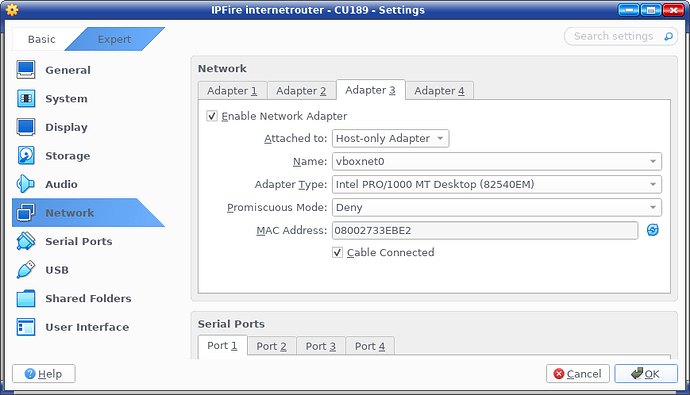
And the adapter 3 is the host-only adapter which names vboxnet0, which can be generated using below command.
vboxmanage hostonlyif create # should create vboxnet0, else adapt following lines
vboxmanage hostonlyif ipconfig vboxnet0 --ip 192.168.56.1 --netmask 255.255.255.0
vboxmanage dhcpserver modify --ifname vboxnet0 --disable
If the adapter name is not vboxnet0, then you can change the adapter 3 according to your configuration.
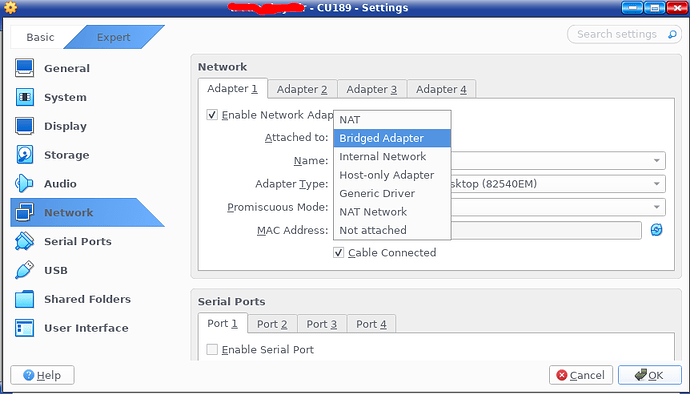
It is the default setting as NAT is at the top of the drop down box list of network types but you can just easily change it to Bridged Adapter by changing the selection in the drop down box list as shown here.
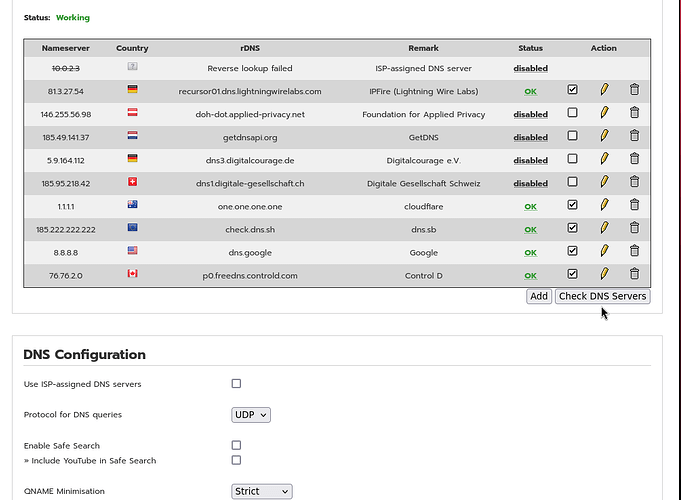
On my working vm system, I changed the Network type from Bridged Adapter to NAT and made no other changes and my vm IPFire DNS still worked fine. I could select no DNS services and I then got the Working (Recursor Mode) or I could enable my existing range of TLS protocol only DNS servers and those also all came back with a green OK status.
I then changed the protocol to UDP and to TCP and tested with a new range of UDP/TCP servers from the list and all came back with a green OK status.
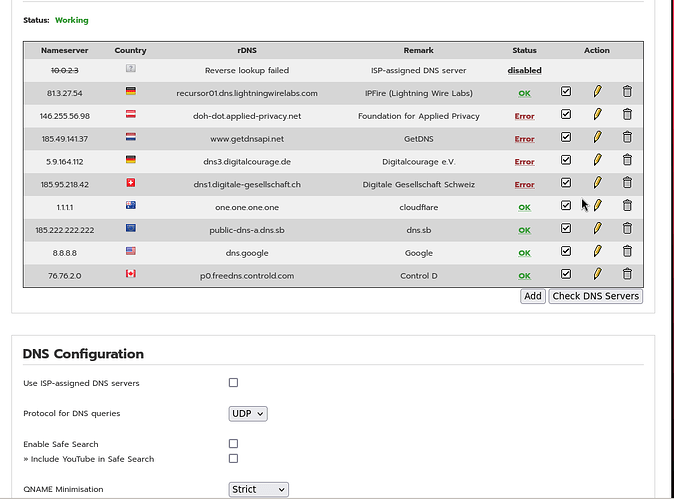
The only way I have been able to get the Error status with a message about response timeout is when I had the TLS only DNS servers being used with a UDP or TCP protocol selected. That makes sense because they only support DNS over TLS and therefore trying to connect without TLS will not get a response.
The IPFire DNS server worked in both cases because it is supporting all of UDP/TCP/TLS
However your Error status with response timeout was with udp for 1.1.1.1 and 8.8.8.8 both of which have worked for me with both NAT and Bridged Adapter.
So I cannot reproduce your problem by using the vm red interface as NAT or Bridged Adapter.
I know how to change the adpter from nat to bridge, and I also know the differences between nat and bridge. But I wonder why this dns service can not be worked when internet router starting. And I note that the name of your virtual machine named xxx - CU189, which indicates that you don’t use my Internet Router.ova
Below is steps to reproduce above problem more detail.
When import the ova, we should first using Include all network adapter MAC addresses
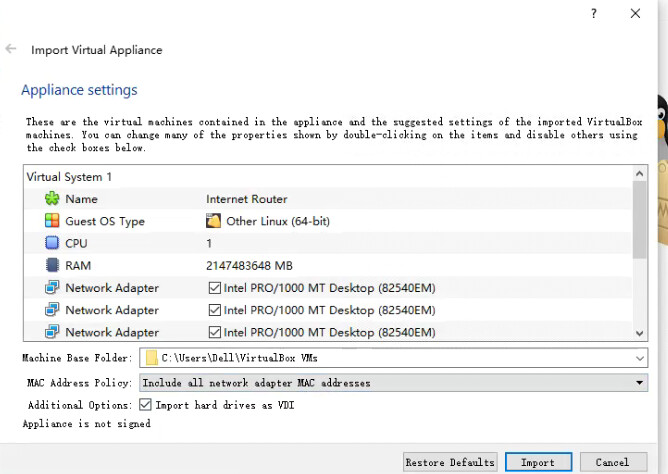
Then, change the adapter 3 with your own host-only adapter name, note that this host-only adapter’s IP address should be 192.168.56.0/24.
And now, we can start the internet router, and login the internet router with username root and password breach, and then test the dns service with nslookup. Below is some cases:
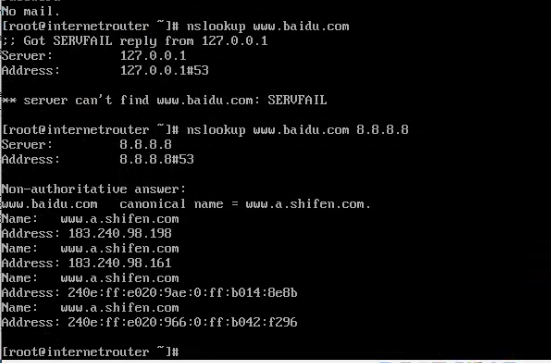
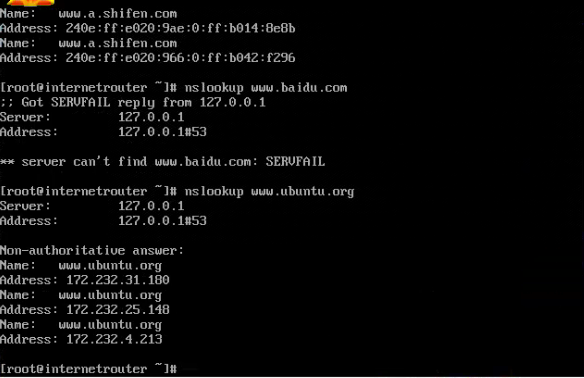
However, this nslookup failure does not always occur. You need to try several domain names. Some domain names can be resolved successfully, while some cannot.
I am sorry but from a security principle I don’t import and install vm images onto my system from anywhere.
I only build them from scratch myself.
To advance in this topic, it would be nice to know how the system is built.
I don’t think of the vm config of IPFire ( your ‘internet router’ ), but the whole system: WAN, access device, IPFire, LAN. Where are the components located, how are they connected?
Fine, I use packer and ansible to build internet router. Below is relevant files to reproduce internet router.
below is the command to install packer and ansible
# Install packer v1.6.3
export VER="1.6.3"
sudo wget https://releases.hashicorp.com/packer/${VER}/packer_${VER}_linux_amd64.zip
sudo unzip packer_${VER}_linux_amd64.zip -d /usr/local/bin
pip install -r requirements.txt
the content of requirements.txt is as below:
ansible==8.7.0
colorama==0.4.6
paramiko==3.4.1
pytest==8.3.3
pyvmomi==6.7.1.2018.12
pywinrm==0.4.1
selenium==4.3.0
tox==4.18.1
veryprettytable==0.8.1
asyncio==3.4.3
setuptools~=74.1.2
The relevant packer and ansible config files are all in the google drive link here code.zip - Google Drive.
After install packer and ansible, then you can use ./tooles/build_internetrouter to build your own internet router
Why run this in a virtual box in the first place?
I would use the internet router to monitor attack scenary to collect all log information about attack scenary.
the internet router is just for route function and to record all relevant traffic information.
And the username and password for internet router is seperately root and breach
Packer and Ansible is also not going to work as it is still a deployment of an existing external vm setup onto my system.
Also the versions you mention of packer and ansible are old.
To make this work that I can see if I can reproduce the problem you are seeing, you would need to detail the MAC addresses for each of the interfaces you have set up, together with the subnets for each of the zones used. Also the hostname and the domain used.
I could then reconstruct your vm IPFire on my system by installing CU189 and setting up the zones that you have defined. I would then use dhcp on red so it gets its IP from my production IPFire and define an IP range for the dhcp on green based on the subnet you have defined.
To access the WUI I would use a vm system on the green interface and will clone one of my existing green vm systems and adapt it for this purpose.
If you are willing to provide the above info then I will try and find the time to set it up on my system and evaluate it.
@dr_techno: Please refrain from posting this kind of advice. I am not even sure where you are taking this from and what problem you are trying to solve, but certainly it is not the one in this thread. You have also posted similar things in other threads that barely have anything to do with the original discussion. Your advice here is dangerous. Please stop this immediately.
To use automated tools may be ‘nice’. But to search issues it is necessary to know the config of the generated system.
This starts with the overall system layout.
IMHO.
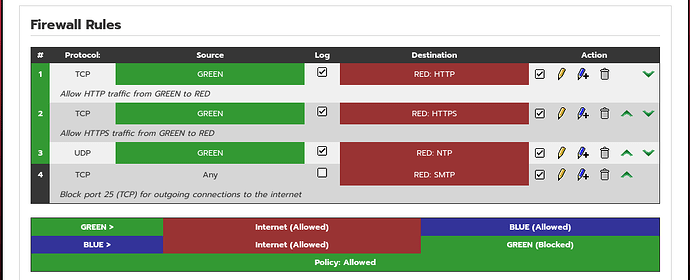
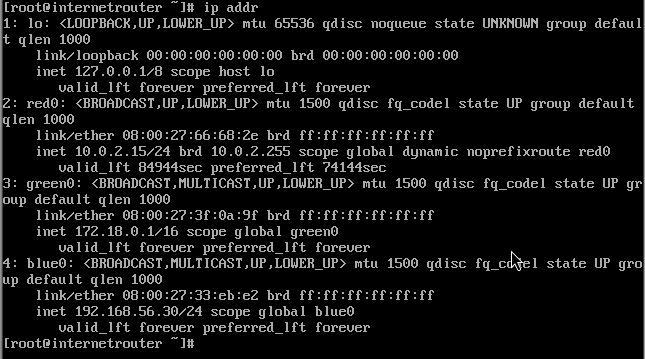
There are 3 network adapter with nat, internal network and host-only adapter seperately.
The ip address configuration is as below:
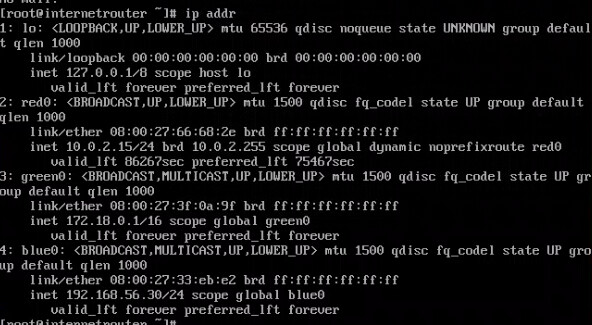
The red is use nat adapter, the green is set with internal network with 172.18.0.1/16, the blue is set with host-only adapter with 192.168.56.30/24.
Configuration to internet router running with shell is as below:
echo "1,ACCEPT,FORWARDFW,ON,std_net_src,GREEN,std_net_tgt,RED,,TCP,,,ON,,,cust_srv,HTTP,Allow HTTP traffic from GREEN to RED,ON,,,,,,,,,00:00,00:00,,AUTO,,dnat,,,,,second" >> /var/ipfire/firewall/config
echo "2,ACCEPT,FORWARDFW,ON,std_net_src,GREEN,std_net_tgt,RED,,TCP,,,ON,,,cust_srv,HTTPS,Allow HTTPS traffic from GREEN to RED,ON,,,,,,,,,00:00,00:00,,AUTO,,dnat,,,,,second" >> /var/ipfire/firewall/config
echo "3,ACCEPT,FORWARDFW,ON,std_net_src,GREEN,std_net_tgt,RED,,UDP,,,ON,,,cust_srv,NTP,,ON,,,,,,,,,00:00,00:00,,AUTO,,dnat,,,,,second" >> /var/ipfire/firewall/config
sed -i '8iiptables -I INPUT -p tcp --dport 222 -j ACCEPT' /etc/sysconfig/firewall.local
sed -i '9iiptables -I INPUT -p tcp --dport 444 -j ACCEPT' /etc/sysconfig/firewall.local
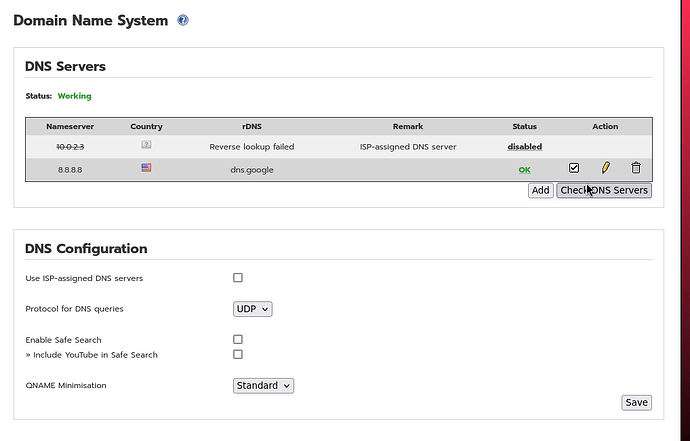
echo "USP_ISP_NAMESERVERS=off" > /var/ipfire/dns/settings
echo "QNAME_MIN=standard" >> /var/ipfire/dns/settings
echo "PROTO=UDP" >> /var/ipfire/dns/settings
echo "ENABLE_SAFE_SEARCH=off" >> /var/ipfire/dns/settings
echo "3,8.8.8.8,,enabled," >> /var/ipfire/dns/servers
/etc/init.d/unbound restart
sleep 10
pakfire update
pakfire install python3-setuptools -y
content of /etc/hosts:
127.0.0.1 localhost
172.18.0.1 internetrouter.localdomain internetrouter
10.0.2.2 gateway
content of /etc/unbound/hosts
# This file is automatically generated and any changes
# will be overwritten. DO NOT EDIT!
local-data: 'internetrouter.localdomain 60 IN A 172.18.0.1'
local-data: '1.0.18.172.in-addr.arpa 60 IN PTR internetrouter.localdomain'
local-data: '30.56.168.192.in-addr.arpa 60 IN PTR internetrouter.localdomain'
local-data: 'extmail1. 60 IN A 172.18.0.3'
local-data: '3.0.18.172.in-addr.arpa 60 IN PTR extmail1.'
local-data: 'extmail2. 60 IN A 172.18.0.3'
local-data: '3.0.18.172.in-addr.arpa 60 IN PTR extmail2.'
local-data: 'extmail3. 60 IN A 172.18.0.3'
local-data: '3.0.18.172.in-addr.arpa 60 IN PTR extmail3.'
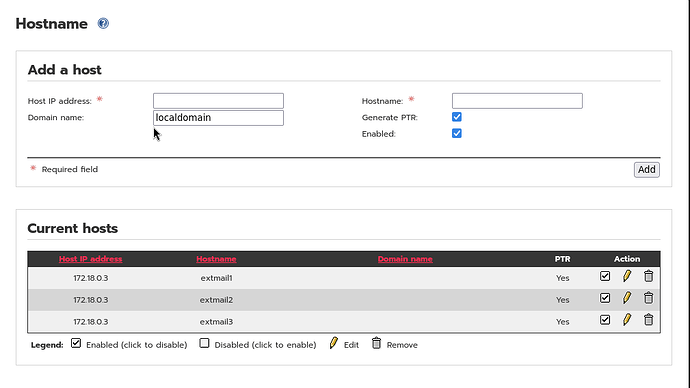
content of /var/ipfire/main/hosts
on,172.18.0.3,extmail1,,on
on,172.18.0.3,extmail2,,on
on,172.18.0.3,extmail3,,on
content of /etc/ntp.conf
# Configuration file for ntpd, created by time.cgi.
# Do not edit manually.
#
restrict default kod limited nomodify nopeer noquery notrap
restrict 127.0.0.1
# Our networks
restrict 172.18.0.0 mask 255.255.0.0 nomodify noquery notrap
restrict 192.168.56.0 mask 255.255.255.0 nomodify noquery notrap
# Servers
server 0.pool.ntp.org iburst
server 1.pool.ntp.org iburst
server 2.pool.ntp.org iburst
# Local clock
#server 127.127.1.0
#fudge 127.127.1.0 stratum 7
# Other settings
driftfile /var/log/ntp/drift
tinker panic 0
logconfig +allsync +allclock +allsys
So I set up a vm using the information you provided.
I set up the networks as indicated.
I then entered the three Firewall rules via the WUI.
If your system also has the overall policy of Allowed then these three firewall rules are pointless as Green can connect to anything on Red by default. However I added them in anyway.
I then added the firewall.local rules.
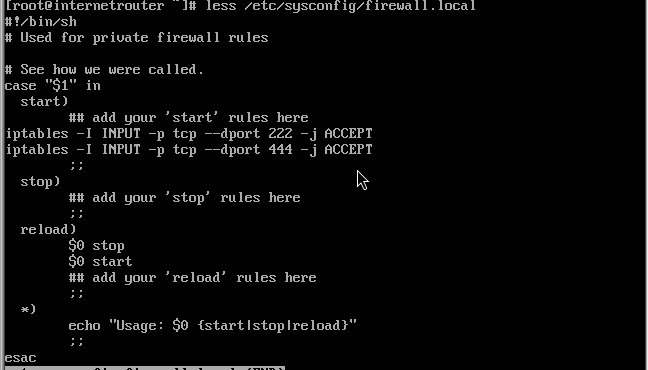
I note that you are inserting the rule into the INPUT chain. These rules could also have been added into the firewall rules via the WUI. Basically you are giving access to the SSH server and the WUI from the red interface.
However I added them in anyway. You also should really also remove them when the system is going down, so the removal should be in the Stop section of firewall.local.
I setup the DNS Server via the WUI
This gave the same result in the dns settings and server files as you showed.
As you can see the 8.8.8.8 dns server is showing a green OK and overall status is Working.
I have no idea why you have python3-setuptools installed but I also installed that via pakfire on the WUI.
I then installed the three hostnames with the same IP in the Hosts section of the WUI
Your output of the /var/ipfire/main/hosts file showed that the domain name was left blank, so I also did that.
The result of installing all the above, via the WUI, except for firewall.local is that the contents of /etc/hosts and /etc/unbound/hosts ended up the same as you showed.
I am presuming that it is a typo but you have referenced /etc/unbound/hosts but it is /etc/unbound/hosts.conf
I have no idea why you have completely altered the ntp.conf to a completely different set of commands compared to what is defined in the IPFire code. This is not something that is modified by the WUI at all but defined in the core code.
I tried the vm system with the normal ntp.conf content
disable monitor
restrict default nomodify noquery
server 127.127.1.0 prefer
fudge 127.127.1.0 stratum 10
driftfile /etc/ntp/drift
and then also with your content
In both cases the DNS system stayed working with no problems on my system.
Anyway, I can not reproduce your problem but if you are modifying various core IPFire files manually then you should first re-install IPFire CU189 from scratch and set everything up via the WUI and if you are still having a problem at that point then I think the source of the issue is not IPFire or probably even your vm setup but the connection from your internetrouter red interface to the internet.
First do a fresh install of IPFire with no file modifications and confirm if the problem is there or not.
If it is still there then show a diagram of how your network is laid out and connected to the Internet, as previously suggested by @bbitsch .
I have found the nslookup error message from /var/log/message!
each nslookup error is because of validatoin failure <>: no DNSSEC records from 8.8.8.8 for DS psf.io. while building chainf of trust
And after a while, DNSSEC seems to be worked? that’s why?
Somewhere in the path from your ipfire to the 8.8.8.8 dns server something is stopping or messing with the DNSSEC validation.
What are you using for your connection to the internet? Is that an ipfire system or is it an ISP provided modem? Does that internet connection have dns servers (ISP or external server) specified, some of which are not DNSSEC compliant?