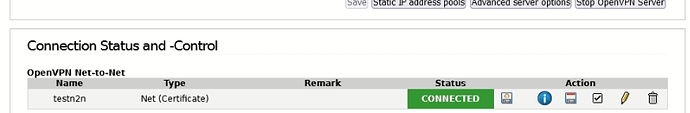
This is just a small example OpenVPN Net-to-Net Virtual Private Network
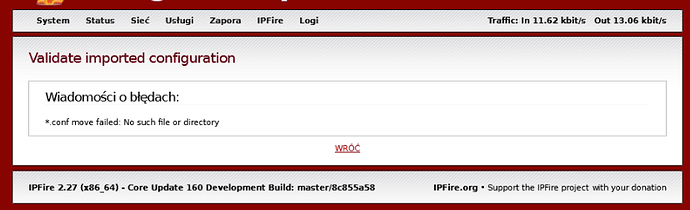
If you have a problem importing Client Package on IPFire client OpenVPN
you can try the solution below:
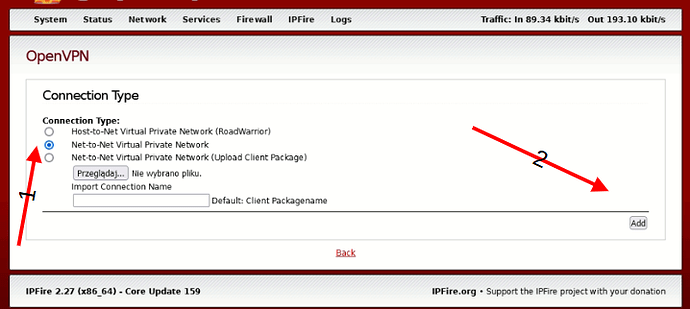
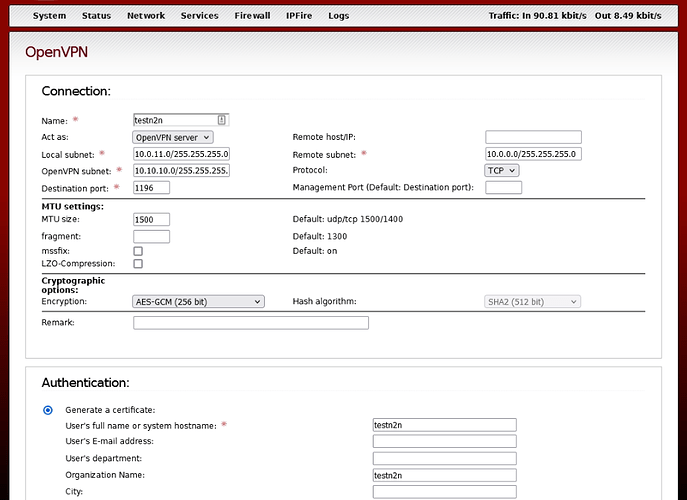
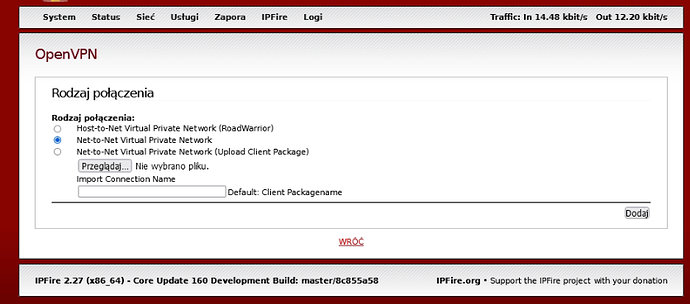
On IPfire server OpenVPN
then enter proper settings
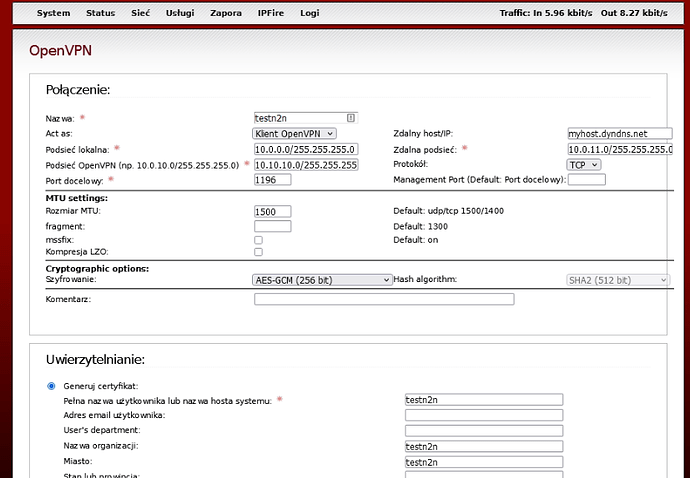
Then on IPfire client OpenVPN
then
After add connections
on IPfire server OpenVPN and on IPfire client OpenVPN
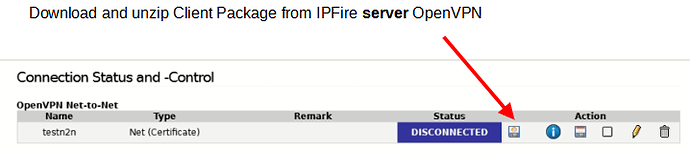
download and unzip Client Package from IPfire server OpenVPN
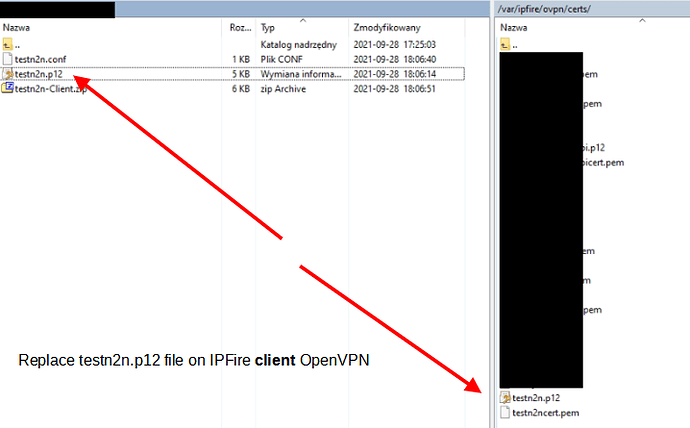
then replace
Effects:
on server
on client
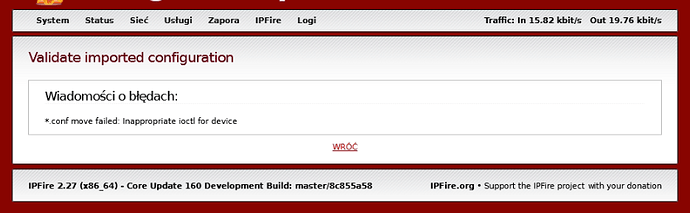
Note: in my case, I had to use TCP protocol, but after switching to UDP it also worked.
Edit
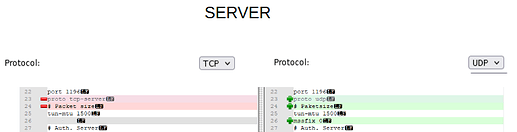
Ovpnconfig file on server for TCP
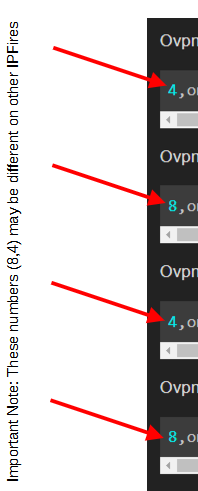
4,on,testn2n,testn2n,net,cert,,server,,10.0.11.0/255.255.255.0,,,10.0.0.0/255.255.255.0,,,,,,,,,,,1196,,,,red,10.10.10.0/255.255.255.0,tcp,1196,,1500,,,,,,,,,AES-256-GCM
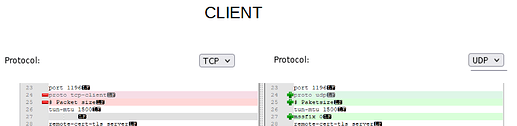
Ovpnconfig file on client for TCP
8,on,testn2n,testn2n,net,cert,,client,,10.0.0.0/255.255.255.0,,myhost.dyndns.net,10.0.11.0/255.255.255.0,,,,,,,,,,,1196,,,,red,10.10.10.0/255.255.255.0,tcp,1196,,1500,,,,,,,,,AES-256-GCM
Ovpnconfig file on server after switch to UDP
4,on,testn2n,testn2n,net,cert,,server,,10.0.11.0/255.255.255.0,,,10.0.0.0/255.255.255.0,,,,,,,,,,,1196,,,,red,10.10.10.0/255.255.255.0,udp,1196,,1500,,,,,,,,,AES-256-GCM
Ovpnconfig file on client after switch to UDP
8,on,testn2n,testn2n,net,cert,,client,,10.0.0.0/255.255.255.0,,myhost.dyndns.net,10.0.11.0/255.255.255.0,,,,,,,,,,,1196,,,,red,10.10.10.0/255.255.255.0,udp,1196,,1500,,,,,,,,,AES-256-GCM
Edit 2
Important Note: These numbers (8,4) may be different on other IPFires
Edit 3
Content of testn2n.conf file on the server
# IPFire n2n Open VPN Server Config by ummeegge und m.a.d
# User Security
user nobody
group nobody
persist-tun
persist-key
script-security 2
# IP/DNS for remote Server Gateway
float
# IP adresses of the VPN Subnet
ifconfig 10.10.10.1 10.10.10.2
# Client Gateway Network
route 10.0.0.0 255.255.255.0
up "/etc/init.d/static-routes start"
# tun Device
dev tun
#Logfile for statistics
status-version 1
status /var/run/openvpn/testn2n-n2n 10
# Port and Protokol
port 1196
proto udp
# Paketsize
tun-mtu 1500
mssfix 0
# Auth. Server
tls-server
ca /var/ipfire/ovpn/ca/cacert.pem
cert /var/ipfire/ovpn/certs/servercert.pem
key /var/ipfire/ovpn/certs/serverkey.pem
dh /var/ipfire/ovpn/ca/dh1024.pem
# Cipher
cipher AES-256-GCM
tls-version-min 1.2
# Debug Level
verb 3
# Tunnel check
keepalive 10 60
# Start as daemon
daemon testn2nn2n
writepid /var/run/testn2nn2n.pid
# Activate Management Interface and Port
management localhost 1196
Content of testn2n.conf file on the client
# IPFire rewritten n2n Open VPN Client Config by ummeegge und m.a.d
#
# User Security
user nobody
group nobody
persist-tun
persist-key
script-security 2
# IP/DNS for remote Server Gateway
remote myhost.dyndns.net
float
# IP adresses of the VPN Subnet
ifconfig 10.10.10.2 10.10.10.1
# Server Gateway Network
route 10.0.11.0 255.255.255.0
up "/etc/init.d/static-routes start"
# tun Device
dev tun
#Logfile for statistics
status-version 1
status /var/run/openvpn/testn2n-n2n 10
# Port and Protokol
port 1196
proto udp
# Paketsize
tun-mtu 1500
mssfix 0
remote-cert-tls server
# Auth. Client
tls-client
# Cipher
cipher AES-256-GCM
pkcs12 /var/ipfire/ovpn/certs/testn2n.p12
tls-version-min 1.2
# Debug Level
verb 3
# Tunnel check
keepalive 10 60
# Start as daemon
daemon testn2nn2n
writepid /var/run/testn2nn2n.pid
# Activate Management Interface and Port
management localhost 1196
Below are the differences in the contents of the testn2n.conf files, between the TCP and UDP settings.