Hi, My situation is… I have Ipfire as a perimeter firewall with whole lan vpn, qemu truenas and nextcloud. I try to block the NAS and Nextcloud from internet, to make it only accessible via lan or vpn, but it doesn’t work. The lan vpn is via 10.8.0.0/16. I’ve tried to block that ip range, and blocking all red, but Truenas and Nextcloud still are internet accessible. I’m at a loss. No firewall rules seem to affect.
What firewall rules did you setup?
You could post a screenshot.
I am not an expert but I had some issues in the past so maybe I can help. ![]()
Hi,
also, a brief description or even a simple diagram of your network would help us to understand your issue.
In particular, I did not yet understood the “VPN” part in “I have Ipfire as a perimeter firewall with whole lan vpn”. Does that mean IPFire serves as a VPN server? Or is the LAN part of a VPN?
Thanks, and best regards,
Pete Müller
Hi, thanks for the interest. I have red input from cable modem to pc running ipfire with a qemu kvm virtual machine Truenas with a Nextcloud jail. (sounds like a mess already right:). So, the lan is on 172.x.x.x, but all the internet traffic is routed through openvpn on a 10.8.x.x to NordVPN. Truenas is 172.x.x.25 and Nextcloud 172.x.x.50. I want LAN only access, so I’m trying to block those two from red. The firewall rules I have tried are: the ip’s to red, the ip’s to 10.8.x.x, the ip’s to and from red firewall.
Peter, the IPFire is a VPN client that provides VPN internet to the green LAN.
Hi,
thanks for your reply.
(sigh) A mess indeed, but I guess there is no sense in arguing about this…
Well, that sounds like a simple firewall rule to me indeed.
Please post a screenshot of them. It is a bit tricky to understand the rules based on your description.
Thanks, and best regards,
Peter Müller
Thanks Peter! I’m not exactly sure what screenshot you are requesting.
That screenshot was of rules that I have enabled/disabled in my troubleshooting.
I tried to group tnas (TrueNAS) and tnasnc (NextCloud instance running in TrueNAS) together.
I have also tried to block individual ip’s…
Thank you for having a look!
To visualize:
Red is ISP to IPFire. Where I have the green LAN connecting to Nord VPN via:
TID=300 #Table ID
VPN_GTWY="$route_vpn_gateway" # provided by OpenVPN at runtime
VPN_IF="$dev" # provided by OpenVPN at runtime
echo “Table ID=” $TID
echo “VPN Gateway=” $VPN_GTWY
echo “VPN Interface=” $VPN_IF
copy main routing table to VPN routing table (ignore default gateway)
ip route flush table $TID > /dev/null 2>&1
ip route show table main | grep -Ev ^default
| while read route; do
ip route add $route table $TID
done
specify VPN as default gateway
ip rule add from 172.25.25.0/24 table $TID
ip route add default via $VPN_GTWY dev $VPN_IF table $TID
ip route flush cache
add postrouting
iptables -t nat -A POSTROUTING -s 172.25.25.0/24 -o $VPN_IF -j MASQUERADE
TrueNas and Nextcloud are running in IPFire virtual machine.
No arguing in any way. If there is a less messy solution, I’m all ears. Thanks so much for any insight.
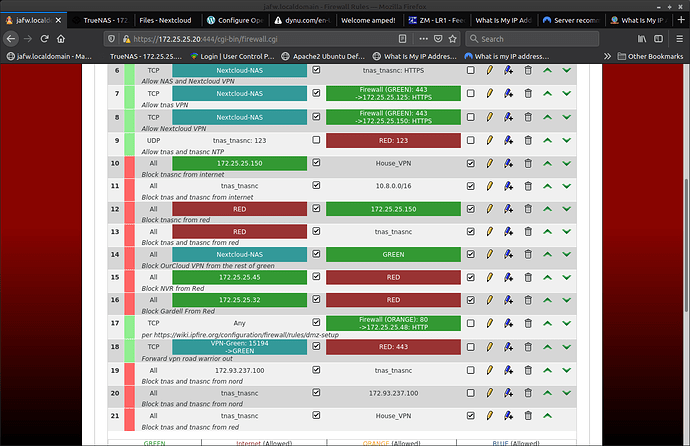
Thanks trish! I posted a screenshot, but it is probably nonsensical. As I have added/removed edited etc… trying different things.
Hi,
thank you for your detailed replies.
First, it appears to me that there are some errors in your firewall rules, and they could be organised better:
-
Rule 9: Source ports are not necessary here (“tnas_tnasnc:123”), and since they won’t be necessarily used as source port numbers for NTP queries, that rule probably does not work. Also, consider using a predefined service for the destination port.
-
Rule 11 looks unnecessary to me, but I am not sure about it.
-
Rules 12 and 13 are bogus, since incoming traffic from RED is never permitted according to the firewall default policy, unless it belongs to a previously established connection from an internal network.
-
Rules 15 and 16 could be simplified by using a host group.
Since I did not fully understand what you configured for routing all traffic through the VPN provider, I am not quite sure about the rest. Frankly - and no offense intended -, I think it might be better if you change the default firewall behaviour of your installation to “blocked” for both forwarded and outgoing connections.
Then, no traffic will be permitted unless explicitly allowed by a firewall rule, which I believe would lead to a more clear firewall ruleset, since you only have to worry about the traffic you explicitly want to permit, and the rest is dropped automatically.
A while ago, I wrote this blog post about configuration recommendations for IPFire’s firewall engine. Perhaps it might be helpful to you as well. ![]()
Would you do me the favor of doing this, and then taking a screenshot of your entire firewall rule page (see here on how to do so in Firefox), and report back? While this may sound lazy from my side, I believe it would be the better approach to your problem.
Well, I really do not want do go this thread to down the road towards a “religious war” of whether using a commercial VPN is a good idea or not.
Personally, I am not really fond of them, for reasons explained here (section “Avoid VPN providers: Nobody is going to jail for you for a few bucks per month”).
If I understood your situation correctly, you are trying to force traffic of devices or applications not prepared for this through a VPN. Since they are not designed/hardened for such a thing, I believe this causes more harm than good.
My approach would be to enforce a strict firewall policy first, restricting network communication to the bare minimum, and then use something like Tor Browser or Whonix (more secure) for the private surfing - these are designed for this task, and can deal with all sorts of issues that come with increased privacy demands.
Thanks, and best regards,
Peter Müller