As I understand the instructions for DNS forwarding, you can use a separate DNS server for certain target addresses (FQDN) than the one distributed via the DHCP.
This is going to get wild, but without knowing the context, the error cannot be narrowed down to that extent.
Let’s leave the upstream proy out of the equation for now, but you can use it to prove that the routing is basically working.
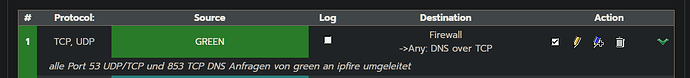
Ipfire runs in forward block mode. Whitelist
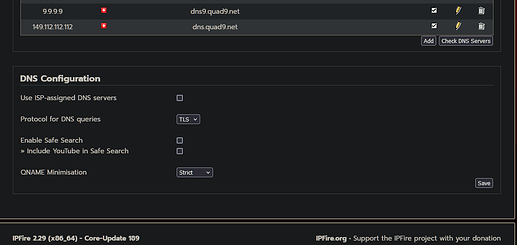
DNS:
The Ipfire with unbound runs with the recursor mode and is the DNS server for all clients, all requests on port 53 are redirected to the ipfire using a firewall rule.
DNS requests from IPfire in TLS mode and striker Qname.
However, the problem also occurs when I select a DNS server. e.g. 5.9.164.112 (Digitalcourage)
DNS Forwarding:
I use “ipleak.net” and “browerleaks.com” as the destination address (FQDN) and for the DNS server “1.1.1.1”.
Client 1 is restricted with the Windows Firewall, which only allows two connections to the outside, a VPN exit whose port in the IPfire is only released to certain fixed IP addresses and access to the IPfire itself.
In multi-tab mode, the Firefox browser of client 1 has the option of specifying a separate proxy server for each group. Group 1 uses the Squid proxy of the Ipfire.
The DNS via Socks5 option in the proxy settings must be activated. I will also explain why.
Let’s assume I deactivate the DNS forwarding option and call the domain ipleak.net.
This provides me with my IP and the same IP as DNS because Ipfire itself is the DNS server.
If I now activate DNS Forwarding, I expect that my IP is still displayed, but the DNS server is 1.1.1.1 or one of cloudflare’s DNS servers.
Instead, Firefox can’t find the address and I get the error message in the unbound log mentioned in the initial post.
Under connections I also see Ipfire trying to connect on port 53 with 1.1.1.1.
I do not get an entry in the log that this call is blocked.
So where is the error?
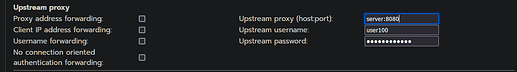
How do I use this error and what does the upstream proxy enable?
If I now switch an upstream proxy in front of the Squid and deactivate DNS forwarding, call ipleak.net again, the so-called DNS leak occurs.
I am shown the IP of the upstream proxy and the corresponding DNS server plus the IP of the Ipfire. That’s not what I wanted.
If I now activate DNS Forwarding, unbound generates the same error message again BUT the page can be accessed and the IP of the IPfire has disappeared.
It only recognizes the IP of the UPstream proxy and its DNS server.
Actually it would have been enough for me that the IP of the Ipfire disappears as DNS and 1.1.1.1 is displayed.
Due to the errors in unbound I played around a bit and got the same result even without recursor mode.
Why does the DNS over Socks Proxy option have to be activated for this? The Firefox APi unfortunately has the strange habit of sending a DNS query to everything and everyone else, which then ensures that all DNS servers used are displayed, including those of the VPN connection from Windows or those of the other socks proxy connections that are defined in multitab mode.
So why I get this unbound errors with DNS Forwarding?
P.s. Same results with browserleaks.com, but dnsleaktest.com or dnstools.check do not show the DNS leaks so not recommend for this tests.