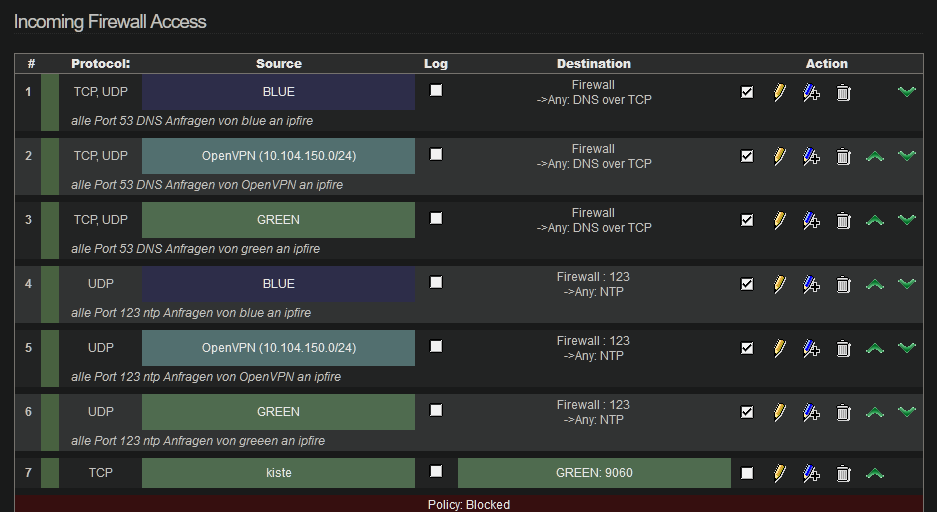
For me it is one device, only firefox with a specific tab that is set for the Squid proxy.
Everything from my network is redirected to the IPfire for DNS requests.
Or VPN or Tor. Other topic.
EDIT:
Ok I had found the resolver who did forward the query…
-open.dns0.eu
-public-dns-b.dns.sb
-unicast.censurfridns.dk
Perhaps it should be mentioned here and here, these served as a template for my selection.
Edit2:
btw. I get also a lot of messages in unbound log while checking DNSSEC, with the mentioned DNS Server above, like this →
03:18:07 unbound: [11795:0] info: validation failure <badsig-watch-2520bf2f.go-alg13.dnscheck.tools. A IN>: signature crypto failed from 81.3.27.54
03:13:27 unbound: [11795:0] info: validation failure <nosig-watch-391a9368.go-alg15.dnscheck.tools. A IN>: no DNSSEC records from 81.3.27.54 for DS nosig-watch-391a9368.go-alg15.dnscheck. tools. while building chain of trust
03:13:26 unbound: [11795:0] info: validation failure <expiredsig-watch-391a9368.go-alg15.dnscheck.tools. A IN>: signature expired from 81.3.27.54