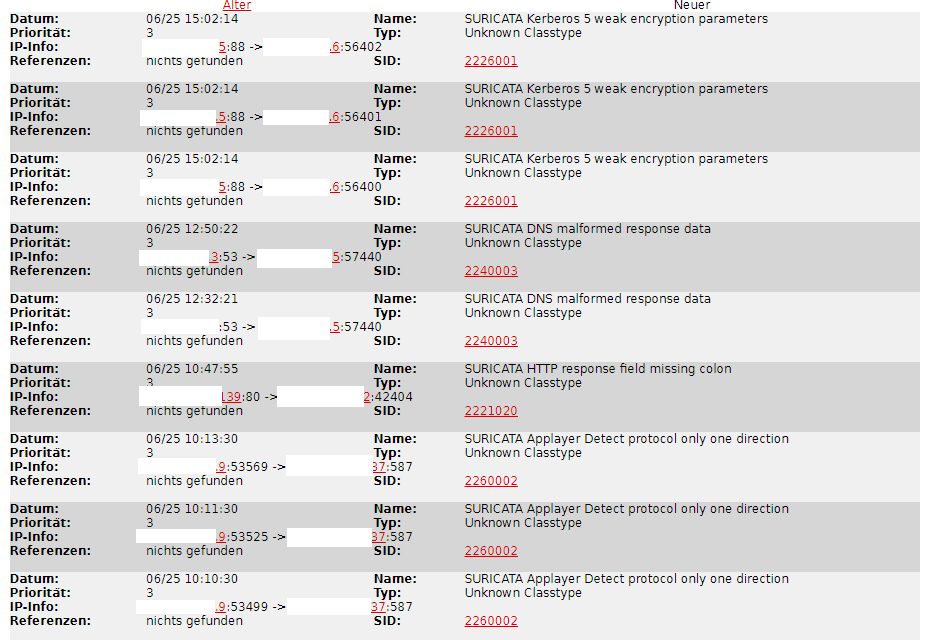
I have the same problem as dzenc. The log is flooded with legitimate connections, all with priority 3. Mail-traffic, kerberos, dns-queries, printer-queries, etc.
I’m not really familiar with suricata now, but is it possible, that priority 3 means just monitoring, because this connections are not blocked. All real attack-rules (Emergingthreatst Community Rules) are logged with priority 2. So wouldn’t it be enough, if we could set which priority should be logged?