Good morning all,
good news, from Nov. 19th there was the last IPHone user here which use also iOS succesfully → Open VPN -> no internet access - #9 by jon
Don´t know which Windows version do you use but on Endians FAQ for OpenVPN, Windows PKCS#12 is in usage → https://help.endian.com/hc/en-us/articles/218144498-How-to-configure-Windows-OpenVPN-client-with-certificate-authentication and this article from 2013…
OK, the simplest first step to check why, is to start it via console with an
sudo openvpn --config {NAME-to-ipfire.ovpn}
If you want it via Network manager Linux Mint do not support the “Read from the File” option like e.g. Fedora does it. In that case a short storybook for you
- Install OpenVPN on Linux Mint
sudo apt install openvpn network-manager-openvpn network-manager-openvpn-gnome
this includes also ‘nmcli’ which you need to import the ovpn file and the rest.
- Use nmcli
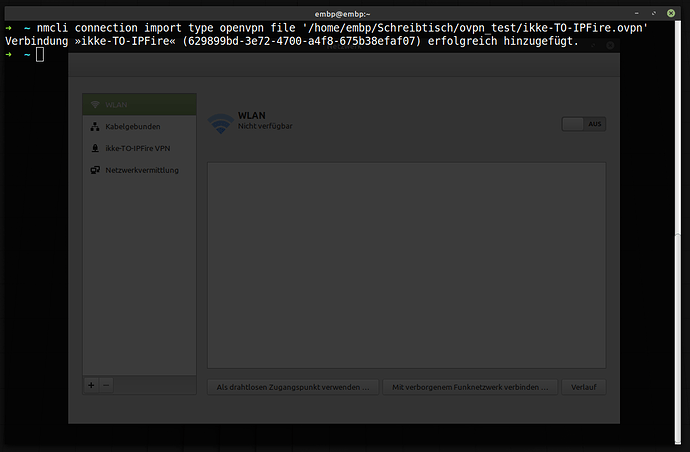
nmcli connection import type openvpn file '/path/to/your/connectionname-TO-IPFire.ovpn'
which looks like this:
That´s it. Or is it really ? → CHECK THE LOGS:
Dec 10 08:19:23 embp nm-openvpn[3604]: OpenVPN 2.4.4 x86_64-pc-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [PKCS11] [MH/PKTINFO] [AEAD] built on May 14 2019
Dec 10 08:19:23 embp nm-openvpn[3604]: library versions: OpenSSL 1.1.1 11 Sep 2018, LZO 2.08
Dec 10 08:19:23 embp nm-openvpn[3604]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Dec 10 08:19:24 embp nm-openvpn[3604]: TCP/UDP: Preserving recently used remote address: [AF_INET]192.168.110.1:1194
Dec 10 08:19:24 embp nm-openvpn[3604]: UDP link local: (not bound)
Dec 10 08:19:24 embp nm-openvpn[3604]: UDP link remote: [AF_INET]192.168.110.1:1194
Dec 10 08:19:24 embp nm-openvpn[3604]: NOTE: chroot will be delayed because of --client, --pull, or --up-delay
Dec 10 08:19:24 embp nm-openvpn[3604]: NOTE: UID/GID downgrade will be delayed because of --client, --pull, or --up-delay
Dec 10 08:19:24 embp nm-openvpn[3604]: [ipfire-prime.local] Peer Connection Initiated with [AF_INET]192.168.110.1:1194
Dec 10 08:19:25 embp nm-openvpn[3604]: TUN/TAP device tun0 opened
Dec 10 08:19:25 embp nm-openvpn[3604]: /usr/lib/NetworkManager/nm-openvpn-service-openvpn-helper --debug 0 3598 --bus-name org.freedesktop.NetworkManager.openvpn.Connection_5 --tun -- tun0 1500 1552 10.75.18.2 10.75.18.1 init
Dec 10 08:19:25 embp nm-openvpn[3604]: chroot to '/var/lib/openvpn/chroot' and cd to '/' succeeded
Dec 10 08:19:25 embp nm-openvpn[3604]: GID set to nm-openvpn
Dec 10 08:19:25 embp nm-openvpn[3604]: UID set to nm-openvpn
Dec 10 08:19:25 embp nm-openvpn[3604]: Initialization Sequence Completed
Yes it is…
So now the easy way to check without all that:
Open up a terminal and feed it with:
sudo openvpn --config ikke-TO-IPFire.ovpn
Hit Enter →
➜ con sudo openvpn --config ikke-TO-IPFire.ovpn
[sudo] Passwort für embp:
Thu Dec 10 08:23:02 2020 OpenVPN 2.4.4 x86_64-pc-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [PKCS11] [MH/PKTINFO] [AEAD] built on May 14 2019
Thu Dec 10 08:23:02 2020 library versions: OpenSSL 1.1.1 11 Sep 2018, LZO 2.08
Thu Dec 10 08:23:02 2020 Outgoing Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
Thu Dec 10 08:23:02 2020 Incoming Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
Thu Dec 10 08:23:02 2020 TCP/UDP: Preserving recently used remote address: [AF_INET]192.168.110.1:1194
Thu Dec 10 08:23:02 2020 Socket Buffers: R=[212992->212992] S=[212992->212992]
Thu Dec 10 08:23:02 2020 UDP link local: (not bound)
Thu Dec 10 08:23:02 2020 UDP link remote: [AF_INET]192.168.110.1:1194
Thu Dec 10 08:23:02 2020 TLS: Initial packet from [AF_INET]192.168.110.1:1194, sid=611d3bf5 41161f71
Thu Dec 10 08:23:02 2020 VERIFY OK: depth=1, C=DE, ST=BW, L=Karlsruhe, O=ummeegge, OU=Fzeit, CN=ummeegge CA, emailAddress=ummeegge@ue.org
Thu Dec 10 08:23:02 2020 VERIFY KU OK
Thu Dec 10 08:23:02 2020 Validating certificate extended key usage
Thu Dec 10 08:23:02 2020 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
Thu Dec 10 08:23:02 2020 VERIFY EKU OK
Thu Dec 10 08:23:02 2020 VERIFY X509NAME OK: C=DE, ST=BW, O=ummeegge, OU=Fzeit, CN=ipfire-prime.local
Thu Dec 10 08:23:02 2020 VERIFY OK: depth=0, C=DE, ST=BW, O=ummeegge, OU=Fzeit, CN=ipfire-prime.local
Thu Dec 10 08:23:03 2020 Key [AF_INET]192.168.110.1:1194 [0] not initialized (yet), dropping packet.
Thu Dec 10 08:23:05 2020 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, 2048 bit RSA
Thu Dec 10 08:23:05 2020 [ipfire-prime.local] Peer Connection Initiated with [AF_INET]192.168.110.1:1194
Thu Dec 10 08:23:06 2020 SENT CONTROL [ipfire-prime.local]: 'PUSH_REQUEST' (status=1)
Thu Dec 10 08:23:06 2020 PUSH: Received control message: 'PUSH_REPLY,route 10.30.103.1,topology net30,ping 10,ping-restart 60,redirect-gateway,route 192.168.110.0 255.255.255.0,route 192.168.7.0 255.255.255.0,dhcp-option DNS 8.8.8.8,dhcp-option DNS 8.8.4.4,ifconfig 10.75.18.2 10.75.18.1,peer-id 1,cipher AES-256-GCM'
Thu Dec 10 08:23:06 2020 OPTIONS IMPORT: timers and/or timeouts modified
Thu Dec 10 08:23:06 2020 OPTIONS IMPORT: --ifconfig/up options modified
Thu Dec 10 08:23:06 2020 OPTIONS IMPORT: route options modified
Thu Dec 10 08:23:06 2020 OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified
Thu Dec 10 08:23:06 2020 OPTIONS IMPORT: peer-id set
Thu Dec 10 08:23:06 2020 OPTIONS IMPORT: adjusting link_mtu to 1624
Thu Dec 10 08:23:06 2020 OPTIONS IMPORT: data channel crypto options modified
Thu Dec 10 08:23:06 2020 Data Channel: using negotiated cipher 'AES-256-GCM'
Thu Dec 10 08:23:06 2020 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Thu Dec 10 08:23:06 2020 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Thu Dec 10 08:23:06 2020 ROUTE_GATEWAY 192.168.110.1/255.255.255.0 IFACE=wlp3s0 HWADDR=68:a8:3d:1d:5a:e2
Thu Dec 10 08:23:06 2020 TUN/TAP device tun0 opened
Thu Dec 10 08:23:06 2020 TUN/TAP TX queue length set to 100
Thu Dec 10 08:23:06 2020 do_ifconfig, tt->did_ifconfig_ipv6_setup=0
Thu Dec 10 08:23:06 2020 /sbin/ip link set dev tun0 up mtu 1500
Thu Dec 10 08:23:06 2020 /sbin/ip addr add dev tun0 local 10.7.18.2 peer 10.7.18.1
Thu Dec 10 08:23:06 2020 /sbin/ip route add 192.168.110.1/32 dev wlp3s0
Thu Dec 10 08:23:06 2020 /sbin/ip route del 0.0.0.0/0
Thu Dec 10 08:23:06 2020 /sbin/ip route add 0.0.0.0/0 via 10.75.18.1
Thu Dec 10 08:23:06 2020 /sbin/ip route add 10.30.103.1/32 via 10.75.18.1
Thu Dec 10 08:23:06 2020 /sbin/ip route add 192.168.110.0/24 via 10.75.18.1
Thu Dec 10 08:23:06 2020 /sbin/ip route add 192.168.7.0/24 via 10.75.18.1
Thu Dec 10 08:23:06 2020 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
Thu Dec 10 08:23:06 2020 Initialization Sequence Completed
Still connected…
So the message said you did not define the CA. This fix needed to be made by you.
Guys in general i can NOT help you out in any way shape or form if you only write “it does not work” have invested now more time to illustrate how it simply works here, to read FAQs for your devices to manage your configuration problems than you describe your problems and deliver some usable informations or logs which should be really in your interest if you want someone to help you out.
Also, please stay at ONE problem in one topic we have here now Android, Windows, IPhones and Linux Mint with 1000% different problems so please stay on topic before the moderator steps in.
Best,
Erik