Like a picture is worth a thousand words  so is the wealth of information in the output of ifconfig
so is the wealth of information in the output of ifconfig
As @bbitsch noted, when troubleshooting we need to look at the settings of the devices (not just the behavior / misbehavior). That is an efficient way to discover and solve technical problems.
An experienced tech, ‘having read the manuals’ and using in depth knowledge and experience, can look at the concrete configuration and deduce how the system will function (often without even running a test) - an ‘engineering’ approach.
@dazz 's system was behaving correctly and predictably, as defined by its configuration settings. However, it was not functioning as expected and by looking at the settings right away we could figure out how it would behave and how that differed from the expected results.
For example, given all the settings of Green PC (with /16 netmask) and a ‘vanilla’ IPFire install - it would be expected that:
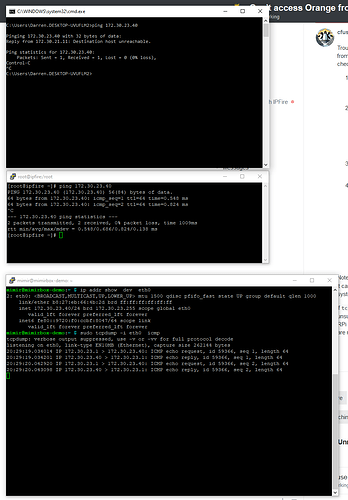
- the PC could access the internet, could ping IPFire’s green and orange interfaces (the network gateways), could connect to the IPFire WUI and ssh to it
- the PC could NOT ping or connect to any computer with IP starting with 172.30 that was not on the local Green LAN (such as the Pi on the Orange network behind the IPFire router)
Testing confirmed this but was not needed to figure this out
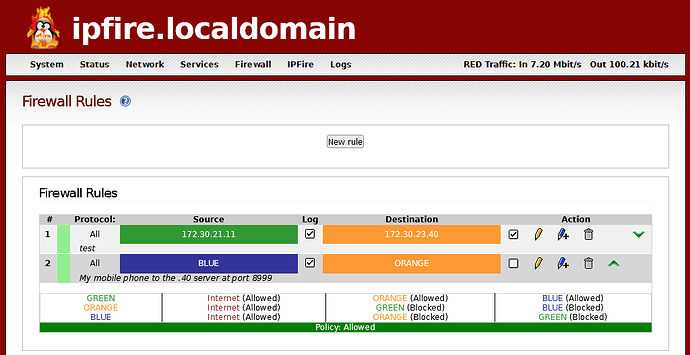
That is why we ask users what is their setup - a diagram and or the actual settings (sanitized as necessary) shared on the forum is most helpful to quickly troubleshoot issues or answer questions.
For example, sharing the config settings like the sample below gives so much concise info about network connectivity: IP addresses, consistent netmasks, consistent MTUs, no physical transmission errors or dropped packets, data sent and received on all interfaces, etc.
[root@ipfire ~]# ifconfig
green0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.100.1 netmask 255.255.255.0 broadcast 0.0.0.0
ether xx:xx:xx:xx:xx:xx txqueuelen 1000 (Ethernet)
RX packets 171871770 bytes 76033671389 (70.8 GiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 243103917 bytes 123274901228 (114.8 GiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
loop txqueuelen 1000 (Local Loopback)
RX packets 13185904 bytes 670156233 (639.1 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 13185904 bytes 670156233 (639.1 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
orange0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.200.1 netmask 255.255.255.0 broadcast 0.0.0.0
ether xx:xx:xx:xx:xx:xx txqueuelen 1000 (Ethernet)
RX packets 2582590 bytes 396472904 (378.1 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1193113 bytes 115655978 (110.2 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
red0: flags=67<UP,BROADCAST,RUNNING> mtu 1500
inet xxx.xxx.xxx.xxx netmask 255.255.255.yyy broadcast 0.0.0.0
ether xx:xx:xx:xx:xx:xx txqueuelen 1000 (Ethernet)
RX packets 1018932245 bytes 170753823783 (159.0 GiB)
RX errors 0 dropped 50 overruns 0 frame 0
TX packets 167200461 bytes 74534966841 (69.4 GiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
[root@ipfire ~]# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 yyy.yyy.yyy.zzz 0.0.0.0 UG 0 0 0 red0
yyy.yyy.yyy.xxx 0.0.0.0 255.255.255.240 U 0 0 0 red0
yyy.yyy.yyy.zzz 0.0.0.0 255.255.255.255 UH 0 0 0 red0
192.168.200.0 0.0.0.0 255.255.255.0 U 0 0 0 orange0
192.168.100.0 0.0.0.0 255.255.255.0 U 0 0 0 green0