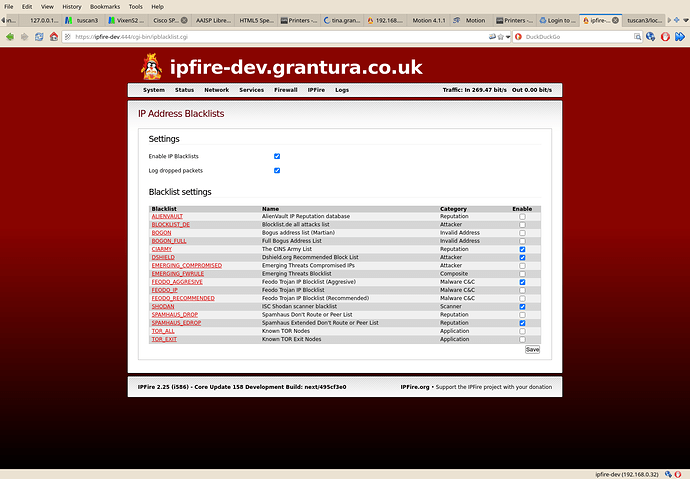
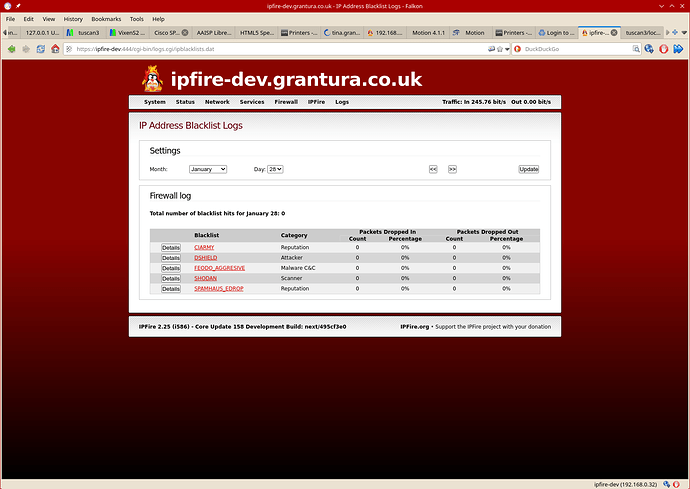
I managed to set up a i586 build for v2.25 core 158 and compiled the 2 C programs and installed then on my alix test system and copied the remaining files over.
Results look ok but this box is behind my production firewall so doesn’t see any firewall hits. Looking OK but I can’t get fcron to update (maybe a permission problem) and looking into it.
I now need to decide on making this available as a stand alone add-on or patch it back into IPFire for which I would need a hand hold !
A couple of screen shots:
3 Likes